Windows users beware this fake update could lock up your PC or worse. This deceptive update scam is a serious threat, capable of far more than just freezing your computer. It could compromise your personal data and potentially expose you to severe security risks. We’ll explore the different ways these malicious actors disguise their attacks, and arm you with the knowledge to recognize and avoid them.
From identifying suspicious downloads to verifying authentic updates, we’ll provide practical steps to protect yourself.
Understanding the tactics behind these fake updates is crucial. Cybercriminals often use sophisticated techniques to mimic legitimate Windows updates, making them nearly indistinguishable from the real thing. This article will delve into the specifics of these threats, explaining the methods used and the potential consequences.
Understanding the Threat
Windows users beware! A recent surge in fake update scams highlights a significant cybersecurity risk. These malicious programs, disguised as legitimate system updates, can wreak havoc on your PC, potentially leading to data loss or even financial fraud. Understanding how these threats work and the signs to look for is crucial for safeguarding your digital assets.Fake updates often exploit user trust in legitimate software updates.
The deceptive nature of these attacks relies on creating a sense of urgency or necessity for immediate action, often through misleading notifications or pop-up messages. This creates a vulnerability that cybercriminals exploit to gain unauthorized access.
How Fake Updates Lock Up Your PC
Fake update programs can be designed to disrupt or disable essential system functions, effectively locking your computer. This is often achieved through malicious code that corrupts system files, interferes with operating system processes, or installs malware designed to prevent normal operation. Some methods involve installing software that replaces legitimate system files with corrupted or malicious versions. These actions can cause your PC to freeze, display error messages, or refuse to boot up.
Types of Malicious Software
Various types of malicious software can be disguised as Windows updates. These include:
- Ransomware: This type of malware encrypts your files and demands payment for their release. It’s a significant threat, capable of crippling productivity and potentially causing significant financial loss.
- Spyware: This software monitors your online activity and collects sensitive data like passwords, financial information, and personal details. This type of threat is particularly insidious as it operates in the background without your knowledge, potentially exposing your private information.
- Trojan Horses: These programs appear harmless but contain hidden malicious code. They can grant attackers remote access to your computer, allowing them to control your system and steal data.
- Rootkits: These are designed to conceal malicious activities by hiding their presence within the operating system. This allows cybercriminals to bypass security measures and maintain persistent access to your system.
Common Tactics Used by Cybercriminals
Cybercriminals often employ various tactics to distribute fake updates:
- Phishing Emails: These emails often impersonate legitimate companies, such as Microsoft, to trick users into downloading malicious files disguised as system updates.
- Fake Download Sites: These websites mimic legitimate software download pages, luring users into downloading infected files under the guise of a legitimate update.
- Malvertising: This involves malicious advertisements on legitimate websites. Clicking on these ads can trigger the download and installation of fake updates.
- Exploiting Software Vulnerabilities: Attackers might target vulnerabilities in outdated software to distribute fake updates.
Consequences Beyond PC Lockup
The consequences of downloading and installing a fake Windows update extend beyond a locked PC.
- Data Loss: Malicious software, particularly ransomware, can encrypt or delete your important files and data.
- Financial Fraud: Spyware can steal your financial information, leading to unauthorized transactions and account compromises.
- Identity Theft: Cybercriminals can utilize stolen information to impersonate you and commit fraudulent activities.
- Reputational Damage: If your personal or business data is compromised, your reputation can be severely tarnished.
Genuine vs. Fake Windows Updates
Distinguishing between a genuine and a fake Windows update is crucial.
- Genuine Windows Update: Typically prompts you to restart your computer after installation. The update usually comes from the official Windows Update site or the Microsoft Update Catalog. A legitimate update does not ask for any personal information or money.
- Fake Windows Update: Often displays urgent or threatening messages. The update might require immediate action or offer a reward. The installation process is usually rushed or lacking in detail. It may come from suspicious sources or websites.
Identifying the Fake Update: Windows Users Beware This Fake Update Could Lock Up Your Pc Or Worse
Fake Windows update scams are a serious threat to computer users. These malicious programs can compromise your system, steal your data, or even completely lock your computer. Understanding how to spot these scams is crucial for protecting your valuable information and preventing costly repairs. This section will delve into the characteristics of legitimate updates, common red flags, and the methods used to trick you.Knowing the difference between a legitimate and a fraudulent Windows update is paramount to safeguarding your system.
This knowledge empowers you to avoid falling victim to malicious actors who exploit vulnerabilities in your computer’s operating system.
Legitimate vs. Fake Windows Updates
A crucial step in protecting yourself from fake updates is understanding the distinctions between legitimate and fraudulent ones. The following table highlights key differences in appearance, location, content, and actions:
| Characteristic | Legitimate Windows Update | Fake Windows Update |
|---|---|---|
| Appearance | Clean, professional design. Consistent with the Microsoft style guide. Usually displays a Microsoft logo. | Potentially poor design. May contain spelling errors, grammatical mistakes, or an unprofessional layout. Logos might be slightly off or misrepresented. |
| Location | Downloaded directly from the official Microsoft website (e.g., windowsupdate.com or a dedicated Microsoft download page). | Downloaded from suspicious websites, often with URLs that resemble legitimate Microsoft sites but have slight variations or typos. |
| Content | Concise description of the update, clear details on what files are being updated, and usually, a list of specific problems it addresses. | Vague or misleading description of the update. May promise significant improvements without providing specifics or may include exaggerated claims. |
| Actions | Initiates the update process with clear prompts and options. Provides a confirmation dialog or window after the update. May require user interaction, like clicking “Next.” | May prompt for immediate installation or use deceptive language to pressure the user into installing it quickly. May have a lack of clarity or multiple steps. |
Red Flags for Fake Windows Updates
Recognizing the red flags associated with fake Windows updates is vital for avoiding installation. Here are some common indicators:
- Unexpected pop-up windows or alerts claiming urgent updates are needed. Genuine updates usually are handled in a more structured and less intrusive way.
- Unusual or suspicious email attachments claiming to be Windows updates. Look for misspellings, poor grammar, or generic greetings.
- Prompts for unusual actions or software installations beyond the update itself.
- Links to websites with poor grammar or suspicious design that don’t look official. Be wary of typos or altered domain names.
- Requests for personal information (passwords, credit card details) during the update process. Legitimate updates don’t ask for such sensitive information.
Methods Used to Trick Users
Cybercriminals employ various tactics to trick users into downloading and installing fake updates. These methods include:
- Deceptive emails: Phishing emails often mimic legitimate Microsoft communications. These emails may contain links to fake update download pages or malicious attachments.
- Fake websites: These websites mimic the look and feel of the Microsoft website to trick users into downloading malicious software. Pay close attention to the URL.
- Social engineering: Cybercriminals might try to pressure users into installing updates by creating a sense of urgency or exploiting their trust in a familiar brand.
- Malvertising: Malicious advertisements that redirect users to fake update download pages. These advertisements may appear on legitimate websites.
Spotting Suspicious Downloads and Emails
Carefully examine any downloads or emails that claim to be Windows updates. Look for these clues:
- Suspicious download links: Verify the source of the download. Legitimate updates are usually directly from the Microsoft website.
- Generic or unusual greetings in emails: Phishing emails often use generic greetings or unusual salutations.
- Suspicious attachments: Be cautious of any attachments claiming to be Windows updates, especially if they have unusual file types or extensions.
- Poor grammar or spelling in emails: Legitimate companies typically proofread their communications.
Legitimate vs. Phishing Websites
Differentiating between legitimate and phishing websites is essential. The following table compares common sources for Windows updates with typical phishing websites:
| Characteristic | Legitimate Update Source (e.g., Microsoft) | Phishing Website |
|---|---|---|
| URL | Valid domain name (e.g., windowsupdate.com), consistent with Microsoft’s branding. | Possibly a similar-looking domain name but with slight variations or typos (e.g., microsoftupdates.com). |
| Content | Clear, concise, and accurate information about the update. | Potentially vague, misleading, or exaggerated claims. May contain spelling or grammatical errors. |
| Security | HTTPS security protocol (indicated by the padlock icon in the browser). Valid security certificates. | Potentially lacking HTTPS security, or using a self-signed or invalid certificate. |
Protecting Yourself from the Threat
Fake Windows update scams are a serious concern for computer users. These malicious actors often disguise their software as legitimate system updates, luring unsuspecting victims into downloading and installing harmful programs. Protecting yourself requires a proactive approach, combining common sense, verification methods, and responsible software management.
Common Sense Practices for Avoiding Fake Updates
A crucial first step is to avoid clicking on unsolicited update prompts or links. Be extremely cautious about emails, pop-up ads, or messages that pressure you to update your system immediately. If you are unsure about the source, do not engage. Instead, rely on your trusted software and operating system update channels. Trust your gut; if something feels suspicious, it probably is.
Avoid downloading updates from unofficial websites or untrusted sources.
Methods to Verify the Authenticity of Windows Updates
Verify the source of any update. Legitimate Windows updates are typically downloaded and installed through the official Microsoft Update service or the Windows Update feature. Always check the sender’s email address or website for legitimacy before downloading any update files. Microsoft does not solicit updates through unsolicited emails or unexpected pop-ups. Look for the official Microsoft logo and website addresses when downloading updates from the internet.
Importance of Regularly Updating Your Operating System and Software
Keeping your operating system and software up-to-date is critical for security. Updates often include crucial patches to address vulnerabilities that malicious actors could exploit. Regular updates provide the latest protections against known threats. Out-of-date systems are significantly more vulnerable to attacks. Regular updates are a crucial part of your security posture.
Windows users, beware! That seemingly legitimate update might be a sneaky piece of malware, potentially locking up your PC or worse. Similar to the way misinformation spreads online, this fake update could be a digital Trojan horse. Just like how grok blocked Elon Musk and Trump misinformation , it’s crucial to double-check the source and be cautious of anything you download.
Stay vigilant and protect your system!
Securing Your PC Against Malicious Software
Employ strong antivirus and anti-malware software. These programs actively scan for and remove threats, including fake update programs. Regularly scan your system for malware and suspicious files. Employ a strong password policy and enable two-factor authentication wherever possible. Keeping your software updated helps prevent vulnerabilities that malware can exploit.
Steps to Take if You Suspect a Fake Update
Immediately disconnect from the internet to prevent further infection. Do not attempt to uninstall the suspected program yourself; this could cause further damage. Run a full system scan with your reputable antivirus program. Contact a qualified IT professional for assistance. Report the incident to the appropriate authorities.
If you believe you have downloaded a fake update, take immediate action to mitigate the damage. Seek professional help when necessary.
Impact and Prevention
Fake Windows update scams can inflict significant damage on your computer and personal data. These malicious programs, disguised as legitimate system updates, often hide harmful code designed to compromise your system’s security. Understanding the potential repercussions and preventive measures is crucial for safeguarding your digital assets.A fake update can cause a wide range of problems, from minor annoyances to catastrophic data loss.
Windows users, beware! Those dodgy updates can really mess things up, potentially locking your PC or even worse. Fortunately, there are other ways to enjoy reading, like with an e-reader like the amazon kindle scribe e reader kobo elipsa 2e. But still, always double-check those updates before clicking “install” to avoid any nasty surprises. Don’t let a fake update ruin your day.
The severity depends on the sophistication of the malware and the user’s system configuration. It’s important to be aware of the various ways these threats can manifest and take proactive steps to avoid them.
Damage to a User’s PC, Windows users beware this fake update could lock up your pc or worse
Fake updates can cause various issues, ranging from simple system instability to complete system failure. These malicious programs can corrupt system files, leading to operating system malfunctions, application crashes, and boot problems. In some cases, they can even render the computer unusable. Malicious code might disable security features or install other malware, leaving your PC vulnerable to further attacks.
These updates can also consume significant system resources, impacting performance and responsiveness.
Data Breaches and Personal Information Theft
Fake updates can serve as entry points for data breaches. These malicious programs often contain spyware or keyloggers, designed to collect sensitive information like usernames, passwords, credit card details, and other personal data. This stolen information can be used for identity theft, financial fraud, or other malicious activities. Sophisticated attacks might even exploit vulnerabilities to gain access to sensitive data stored on the affected machine.
These attacks can lead to significant financial losses and reputational damage.
Methods of Personal Information Theft
Fake updates employ various methods to steal personal information. These methods can include: installing keyloggers, which record keystrokes to capture passwords and other sensitive data; deploying spyware to monitor user activity and collect information; creating backdoors to allow unauthorized access to the system; and encrypting files for ransom. These threats can compromise personal accounts, financial information, and confidential documents.
In extreme cases, they might gain access to sensitive corporate data, which can lead to substantial losses.
Windows users, beware! That suspicious update lurking on your system could potentially lock up your PC or worse. Meanwhile, if you’re into smartwatches, check out the latest development in the One UI watch 5 beta 3 roll out, but remember, always be cautious about downloading anything untrusted, especially on your computer. The safety of your PC should always be your top priority.
Strategies for Preventing Fake Update Infections
The following table Artikels various strategies to prevent infections from fake Windows updates:
| Action | Description | Effectiveness |
|---|---|---|
| Verify Update Sources | Always download updates from official and trusted sources like the Microsoft website. Be wary of unsolicited updates or downloads from unfamiliar websites. | High |
| Use a Reliable Antivirus | Install and regularly update a reputable antivirus program. Antivirus software can detect and block malicious files, including fake updates. | High |
| Enable Windows Update | Ensure Windows Update is enabled and configured to automatically download and install updates. | High |
| Maintain Operating System Updates | Keep your operating system and applications up-to-date with the latest security patches. Vulnerabilities are often exploited by attackers. | High |
| Exercise Caution with Emails and Downloads | Be cautious when opening email attachments or downloading files from unknown sources. Exercise extreme caution with emails promising free software or updates. | High |
| Employ Strong Passwords | Implement a robust password policy, using a combination of uppercase and lowercase letters, numbers, and symbols. | Medium |
| Regularly Back Up Data | Create regular backups of important files to safeguard against data loss in case of infection. | High |
| Use a Firewall | Implement a firewall to block unauthorized access to your computer. | Medium |
Creating a Strong Password Policy
Creating a robust password policy is essential for protecting your accounts. Strong passwords make it difficult for attackers to gain unauthorized access. A strong password policy should include the following:
- Use a combination of uppercase and lowercase letters, numbers, and symbols.
- Avoid using easily guessable information like birthdays, names, or common words.
- Use unique passwords for each account to minimize the impact of a breach.
- Consider using a password manager to generate and store strong, unique passwords.
- Change passwords regularly to maintain security.
Following these guidelines can significantly enhance the security of your accounts.
Illustrative Examples
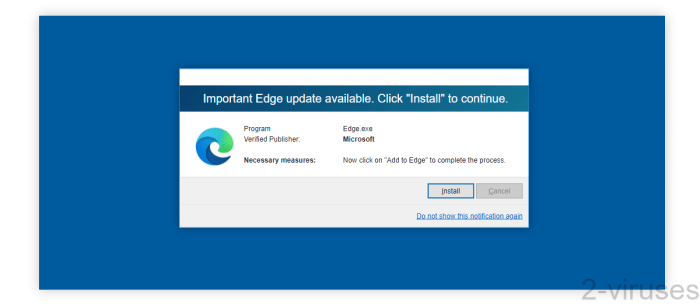
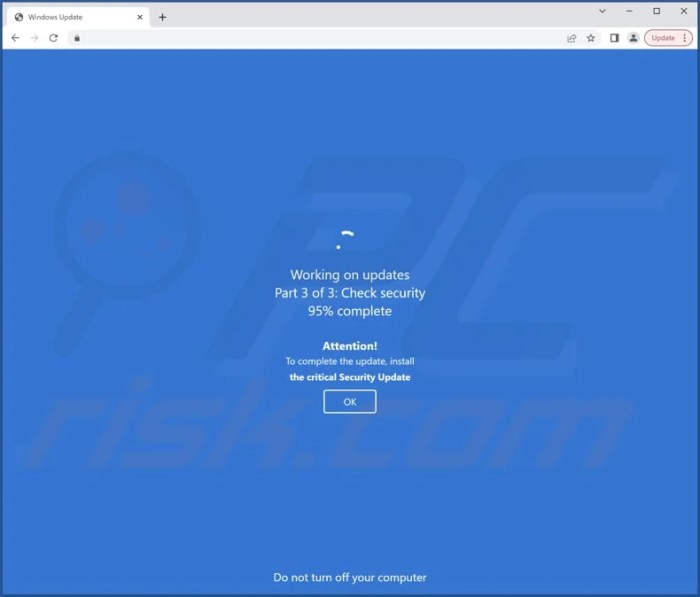
Fake Windows update notifications are a common tactic used by cybercriminals to gain access to your computer. Understanding how these scams appear is crucial for recognizing and avoiding them. These examples will illustrate the red flags to look out for in various attack vectors.
Fake Windows Update Notification
This example shows a deceptive notification designed to trick users into downloading malicious software. The notification mimics the look and feel of a legitimate Windows update, aiming to exploit user trust and familiarity with the system. The notification displays a large, alarming message about critical system updates, often accompanied by an urgent tone. The design is rushed and poorly crafted, containing noticeable inconsistencies compared to the genuine Windows update interface.
The font used is often a generic, non-system font, and the color scheme is off. Key elements like the “Update Now” button might be unusually large or prominent. The language employed may be grammatically incorrect or use overly technical terms, without proper context or explanation. The lack of a clear “Cancel” or “Close” option adds to the sense of urgency and potential threat.
Suspicious elements like the appearance of unfamiliar company logos, and/or contact information, or the use of unusual or vague wording, also suggest a potential threat.
Comparison of Legitimate and Malicious Download Links
Identifying malicious links requires attention to detail. Genuine Microsoft download links and those used in scams often differ in subtle but significant ways. This image displays a legitimate Microsoft download link, contrasted with a malicious one. The legitimate link would typically use the official Microsoft domain (e.g., `microsoft.com` or `update.microsoft.com`). The URL structure would be clean and unambiguous, with a recognizable path indicating the purpose of the download.
The website design would align with Microsoft’s established visual identity, with professional layout, typography, and branding. The malicious link, on the other hand, might use a similar but not exact domain (e.g., `microsoftupdate.xyz`), employing typos or minor variations. The URL structure may contain suspicious characters or an unusual directory path, making it look less authentic. The website design may be poorly executed, with inconsistent formatting, different fonts, or logos that don’t match Microsoft’s style.
Phishing Email Mimicking Windows Update
Phishing emails are another common method used to distribute malware. These emails mimic official notifications, often exploiting users’ reliance on regular software updates. The email subject line might read “Important Windows Update Required,” or something similar, creating a sense of urgency. The email body will usually contain a message about critical system updates, and an accompanying message about the need to act quickly.
It might contain a link to a malicious website. The sender’s email address may look legitimate, but might contain slight variations or be from a non-Microsoft domain. The language in the email may be grammatically incorrect or use technical terms inappropriately, without explanation or context. The email might include an attachment that appears to be an update file, but instead contains malicious code.
Last Recap
In conclusion, safeguarding your Windows PC from fake updates requires vigilance and a proactive approach. By recognizing the red flags, verifying update sources, and implementing robust security measures, you can significantly reduce the risk of falling victim to these malicious schemes. Remember, knowledge is power, and by arming yourself with the information presented here, you can protect your digital life and valuable data.
Stay safe out there!






