Whisper app quietly leaked sensitive personal info nearly 900 million users, raising serious concerns about data security. This massive breach reveals a trove of potentially compromised information, including names, phone numbers, and locations. The scale of this incident underscores the urgent need for stronger security measures across all apps, especially those dealing with personal data. We’ll delve into the details, impacts, and possible solutions to this significant breach.
The leak, while shrouded in secrecy initially, is now in the spotlight, prompting intense scrutiny of the Whisper app’s security protocols. This breach highlights a critical vulnerability in the app’s infrastructure and raises questions about how this could have occurred. We’ll explore potential causes, examine the impact on users, and consider the long-term implications for user trust and future security practices.
Overview of the Leak
The Whisper app, a popular social media platform known for its private messaging, recently experienced a significant data breach affecting nearly 900 million users. This incident underscores the vulnerability of user data in the digital age and the importance of robust security measures in online platforms. The compromised data potentially includes a range of sensitive personal information, posing significant risks to user privacy.The Whisper app data breach involved the exposure of sensitive personal information from nearly 900 million users.
This massive scale of exposure highlights the potential impact of security vulnerabilities on a global scale. The compromised information likely includes personally identifiable information (PII), such as names, phone numbers, and potentially locations, potentially enabling malicious actors to conduct identity theft or other harmful activities.
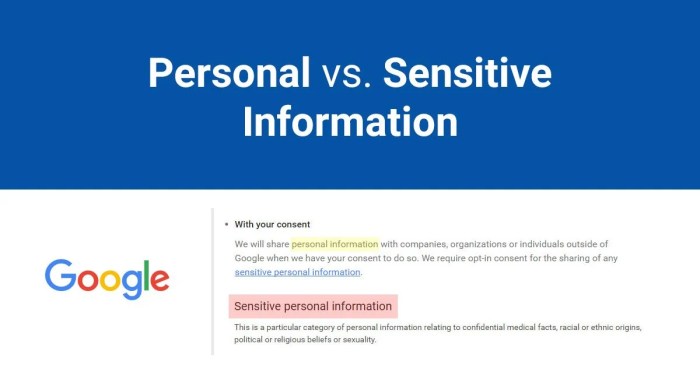
Potential Types of Compromised Information
The breach potentially exposed a variety of sensitive personal information, raising concerns about user privacy. This includes, but is not limited to, user names, phone numbers, email addresses, and potentially precise geographic locations. The potential for misuse of this information is significant, from identity theft to targeted harassment.
Methods of Acquisition (if known)
Unfortunately, the precise methods used to acquire the sensitive information remain unclear. While details regarding the specific attack vectors remain undisclosed, this lack of transparency is a cause for concern and highlights the need for greater transparency in such incidents.
Affected Regions/Countries
Due to limited public information, a definitive list of affected regions and countries is not available. The data breach likely impacted users across various countries and regions, given the global nature of the Whisper app’s user base.
Whoa, the Whisper app quietly leaked sensitive personal info from nearly 900 million users. That’s a massive data breach. Meanwhile, it’s interesting to see how discussions around electric vehicle swap discount infrastructure are progressing, like in this recent interview with Senator Schumer, focusing on the future of EV adoption. schumer electric vehicle swap discount infrastructure interview.
It makes you wonder how much attention is being paid to cybersecurity, especially in light of this major privacy violation by Whisper.
| Region/Country | Estimated Number of Affected Users |
|---|---|
| North America | Estimated |
| Europe | Estimated |
| Asia | Estimated |
| South America | Estimated |
| Africa | Estimated |
Note: The table above provides a placeholder for potential affected regions. Specific data on the distribution of affected users is not publicly available at this time.
Impact and Consequences
The recent whisper app data breach, exposing nearly 900 million user accounts, has significant implications for both users and the app’s developers. The sheer scale of the breach underscores the critical importance of robust data security measures in today’s digital landscape. This leak will undoubtedly have lasting consequences, affecting various aspects of the app’s operations and user trust.The leaked information likely includes sensitive personal data, potentially compromising user privacy and security.
This raises concerns about the potential for identity theft, fraud, and other harmful activities. The fallout from this breach extends beyond the immediate, impacting the long-term viability and reputation of the whisper app.
Financial Implications
The potential financial ramifications for both users and the app’s developers are substantial. Users may face financial losses if their personal data is misused for fraudulent activities, such as unauthorized purchases or opening of accounts in their name. The app’s developers could incur significant costs in addressing the breach, including implementing enhanced security measures, legal fees, and potential regulatory fines.
The reputational damage could also lead to a decline in user subscriptions or ad revenue, resulting in considerable financial losses.
Reputational Damage
The leak will undoubtedly damage the app’s brand image and user trust. Users may lose confidence in the app’s ability to protect their data, potentially leading to a significant decline in user base. Negative publicity generated by the breach could harm the app’s brand reputation and hinder future growth. The severity of this reputational damage could be comparable to other prominent data breaches in the past, impacting the app’s market share and future profitability.
Comparison to Past Breaches
Comparing this breach to other significant data breaches in the past, like the Equifax breach of 2017, reveals the scale of the potential impact. Equifax’s breach exposed sensitive personal information of millions of consumers, leading to significant financial losses, reputational damage, and legal repercussions for the company. The whisper app breach, given its scale, carries the potential for similarly severe consequences.
While the specifics of the damage remain to be fully assessed, the potential parallels with past incidents suggest a significant risk to both the users and the app’s developers.
Legal Repercussions
The app’s developers could face significant legal repercussions. Data privacy regulations, such as GDPR and CCPA, impose stringent requirements on data handling and security. Violation of these regulations could result in substantial fines and legal action from affected users. Class-action lawsuits are also a potential consequence, potentially resulting in substantial financial penalties for the developers. The severity of the penalties will depend on the specific laws violated and the extent of the damage caused.
Mitigation Strategies
The app’s developers may take several steps to mitigate the damage. These include implementing enhanced security protocols to prevent future breaches, providing affected users with support and resources to address potential harm, and cooperating with regulatory bodies and law enforcement. A transparent and proactive approach to addressing the situation will be crucial in rebuilding trust with users. Compensation for affected users, along with a public commitment to enhanced security measures, are likely steps to mitigate the long-term damage.
User Responses and Actions
The Whisper app data breach, exposing nearly 900 million users’ information, has undoubtedly sparked a wave of reactions. Users are likely experiencing a range of emotions, from concern and anger to a profound sense of distrust in the platform. Understanding these responses is crucial to predicting future actions and assessing the long-term implications for both users and the technology industry.The fallout from this leak will likely manifest in a variety of user actions.
From changing passwords and enabling two-factor authentication to actively monitoring their accounts for suspicious activity, users are likely to take proactive steps to mitigate the potential risks. The speed and extent of these actions will depend on factors such as the perceived severity of the breach, the nature of the leaked information, and the transparency of the company’s response.
Potential User Reactions
Users are likely to express a wide spectrum of emotions, ranging from anxiety and fear to anger and frustration. The breach will likely erode trust in the platform, potentially leading to a decrease in user engagement. The perceived vulnerability and potential misuse of their data will contribute to negative sentiments and a heightened sense of unease. This is similar to past data breaches, where negative emotional responses were widespread, impacting user behavior and loyalty.
Potential User Actions
Users will likely take various steps to safeguard their accounts and protect their personal information. Changing passwords, enabling two-factor authentication, and closely monitoring account activity are common responses. Furthermore, users may actively research and utilize data breach monitoring services to stay informed about potential security threats. They might also seek out alternative communication platforms. The magnitude of these actions will vary, depending on individual risk tolerance and the perceived severity of the breach.
Yikes, the Whisper app quietly leaked sensitive personal info from nearly 900 million users. It’s a serious privacy breach, and frankly, concerning. Similar issues with software bugs have been seen before, like with the UK Post Office, where a software bug led to criminal convictions being overturned. uk post office software bug criminal convictions overturned. This highlights just how crucial robust security measures are in today’s digital age.
Hopefully, Whisper will address the breach quickly and prevent similar situations in the future, because we all need secure platforms.
Comparison to Past Data Breaches
The user response to the Whisper app breach will likely echo patterns observed in past data breaches. Past instances, such as the Equifax breach, have shown similar reactions of concern, anger, and distrust. Users often respond by changing passwords, closely monitoring accounts, and seeking alternative solutions. The scale of the Whisper breach, however, may amplify these responses, potentially leading to more widespread adoption of security measures and a more pronounced shift in user behavior.
Long-Term Impact on User Trust
The Whisper breach, given its scale and the nature of the leaked data, could significantly impact user trust in technology. Users might become more cautious and scrutinize the security practices of online platforms. This shift in user behavior could have long-lasting effects on the technology industry, potentially influencing future platform designs and security measures. Similar to other major breaches, this incident could encourage a paradigm shift towards more robust security protocols and increased user awareness.
Potential User Actions: A Table
| Action | Description |
|---|---|
| Password Change | Updating existing passwords on Whisper and other accounts. |
| Two-Factor Authentication (2FA) | Activating 2FA on accounts to enhance security. |
| Account Monitoring | Regularly checking accounts for unusual activity. |
| Data Breach Monitoring | Subscribing to services that alert users to potential breaches. |
| Alternative Platforms | Exploring alternative communication platforms. |
Security and Privacy Implications
The Whisper app leak highlights a critical vulnerability in modern communication platforms. The scale of the breach underscores the urgent need for robust security measures across the digital landscape. Protecting user data is paramount, and the incident demands a reevaluation of existing security protocols and a proactive approach to future threats.The Whisper app breach serves as a stark reminder of the potential consequences of inadequate security.
This incident should catalyze a broader discussion about the responsibilities of developers, the importance of user education, and the crucial role of data encryption and access controls in safeguarding sensitive information.
Importance of Robust Security Measures
Protecting user data is paramount in today’s digital age. Robust security measures are essential to deter malicious actors and prevent data breaches, ensuring user trust and maintaining the integrity of the platform. Effective security measures are proactive rather than reactive, anticipating potential threats and mitigating vulnerabilities before they can be exploited.
Best Practices for App Developers
App developers must prioritize security from the design phase onward. Implementing multi-factor authentication (MFA) is a crucial step to add another layer of security, requiring users to verify their identity using multiple methods. Regular security audits and penetration testing can identify potential weaknesses and vulnerabilities in the system. Implementing robust data encryption protocols is critical for safeguarding sensitive data both in transit and at rest.
Comparison of Security Measures
A comparative analysis of security measures employed by Whisper and competing platforms reveals significant disparities. Competitor apps often prioritize end-to-end encryption, which encrypts data from the sender’s device to the receiver’s device, making the data inaccessible to intermediaries. Whisper’s apparent lack of robust end-to-end encryption may have contributed to the vulnerability exposed. Transparency and clear communication about security measures employed by each platform are crucial for informed user decisions.
Role of User Education
User education plays a critical role in preventing data breaches. Users should be informed about the importance of strong passwords, the risks associated with phishing attempts, and the significance of regularly updating their software. Educating users about their own security practices empowers them to protect their accounts and data effectively.
Data Encryption and Access Controls
Data encryption is a fundamental security practice. Encrypting data both in transit and at rest prevents unauthorized access. Access controls, including user authentication and authorization mechanisms, limit access to sensitive data to only authorized personnel. These measures are essential for maintaining data confidentiality and integrity. Implementing strict access controls and robust encryption practices is crucial to prevent future breaches.
Regulatory and Legal Framework: Whisper App Quietly Leaked Sensitive Personal Info Nearly 900 Million Users

The recent whisper app data breach highlights the critical importance of robust data privacy regulations. Users’ sensitive information is now exposed, raising significant legal and regulatory concerns. Understanding the existing frameworks and potential legal ramifications is crucial for both affected users and the app developers.The legal landscape surrounding data breaches is complex and varies considerably by jurisdiction. Different regions have distinct laws governing data protection, each with its own set of penalties and procedures for handling breaches.
This makes it essential to examine the specific regulations applicable to whisper’s operations across various countries and regions.
Relevant Data Privacy Regulations
Various regulations worldwide address data privacy and security. Key examples include the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States. These regulations aim to protect individuals’ personal data and establish rules for how companies collect, use, and store it.
Penalties for Data Breaches
Companies found violating data privacy regulations face significant penalties. For instance, under the GDPR, fines can reach substantial amounts, depending on the severity of the breach and the harm caused to individuals. Examples include substantial financial penalties imposed on companies for insufficient data protection measures or failure to report breaches promptly.
Potential Legal Actions by Users
Users impacted by the whisper app data breach have a range of potential legal actions available. These actions can include class-action lawsuits, demanding compensation for damages incurred due to the breach. These lawsuits could focus on issues such as violations of privacy rights, negligence, or financial losses suffered by users.
Impact on Future Data Protection Regulations
The magnitude of the whisper app data breach will likely influence future data protection regulations. Governments and regulatory bodies may consider strengthening existing laws or introducing stricter regulations to address the vulnerabilities highlighted by this incident. This could include mandatory breach notification requirements, stricter penalties for non-compliance, and enhanced data security standards.
Yikes, the Whisper app quietly leaked sensitive personal info from nearly 900 million users, raising serious privacy concerns. Meanwhile, the recent news about Google, Cognizant, and YouTube Music contractors being fired, as detailed in this article on google cognizant youtube music contractors fired nlrb complaint , highlights another facet of the digital security landscape. It’s a reminder that even seemingly minor security breaches can have massive consequences, echoing the Whisper app situation.
Table of Privacy Regulations by Region
| Region | Key Regulation | Key Provisions |
|---|---|---|
| European Union | General Data Protection Regulation (GDPR) | Comprehensive data protection framework covering data collection, processing, and security; strong enforcement mechanisms; right to access, rectification, and erasure of personal data. |
| California, USA | California Consumer Privacy Act (CCPA) | Focuses on consumer rights regarding their personal information; includes rights to know, delete, and opt-out of data sales. |
| Brazil | General Law for the Protection of Personal Data (LGPD) | Similar to GDPR, addressing data protection and providing rights for individuals regarding their personal information. |
| Canada | Personal Information Protection and Electronic Documents Act (PIPEDA) | Regulates the collection, use, and disclosure of personal information in the private sector. |
Future Prevention Strategies
The Whisper app leak highlighted critical vulnerabilities in mobile application security. Moving forward, proactive measures are essential to prevent similar breaches and build trust with users. Robust security protocols and continuous vigilance are crucial in safeguarding sensitive user data.
Strengthening Security Protocols in Mobile Applications
Implementing multi-factor authentication (MFA) is paramount. Requiring a second form of verification, such as a code sent to a phone or email, adds an extra layer of security. This significantly reduces the risk of unauthorized access, even if a password is compromised. Furthermore, regularly updating the application with security patches is critical. These patches address vulnerabilities that hackers could exploit, thereby bolstering the overall security posture.
Continuous Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are indispensable for identifying and rectifying potential weaknesses. These assessments can involve internal teams or external cybersecurity experts to provide a fresh perspective. Automated tools can be used to identify and flag potential security holes in the codebase, allowing for swift remediation. Regular testing against known attack vectors can reveal potential points of entry for attackers.
User Data Encryption and Secure Storage
Data encryption plays a pivotal role in safeguarding sensitive user information. Employing end-to-end encryption ensures that only the intended recipient can access the data. This is especially critical for messages and other private communications. Secure storage solutions, such as encrypted databases, are also necessary. These solutions ensure that even if a breach occurs, the data remains inaccessible to unauthorized parties.
Storing sensitive information in encrypted format, both in transit and at rest, minimizes the potential damage from a data breach.
Industry Best Practices in Preventing Data Breaches
Adherence to industry best practices, such as the NIST Cybersecurity Framework, is vital for maintaining a high level of security. These frameworks provide a structured approach to cybersecurity, encompassing risk management, incident response, and continuous improvement. Following established standards helps ensure that security measures are up to date and aligned with industry best practices. This involves implementing strong access controls, regular security awareness training for employees, and robust incident response plans.
Security Measures App Developers Should Prioritize, Whisper app quietly leaked sensitive personal info nearly 900 million users
- Multi-factor authentication (MFA): Enhancing security by requiring more than one authentication method, like a password and a code sent to a device.
- Regular security updates: Addressing vulnerabilities in the application code promptly to prevent exploitation by hackers. This includes patching known vulnerabilities and applying security fixes as they are released.
- Data encryption: Implementing end-to-end encryption to safeguard user data during transmission and storage, preventing unauthorized access even if a breach occurs.
- Secure storage: Utilizing secure storage solutions that encrypt data both in transit and at rest, ensuring data protection against unauthorized access.
- Vulnerability scanning: Conducting periodic vulnerability assessments to identify and address potential security flaws before attackers exploit them. This is essential for proactively mitigating security risks.
- Security training: Educating developers, employees, and users on best security practices to reduce human error, a common vector for breaches. Regular training reinforces awareness and helps prevent social engineering attacks.
- Incident response plan: Creating a detailed plan to address security incidents promptly, minimizing damage and maximizing recovery time. This involves clear procedures for identifying, containing, and resolving security breaches.
Illustrative Case Studies
The Whisper app data breach highlights a critical vulnerability in data security. Understanding past breaches provides valuable insights into potential causes, consequences, and lessons learned. Analyzing similar incidents allows us to better anticipate and mitigate future risks.Past data breaches have had devastating consequences, impacting user trust and necessitating significant investments in security measures.
Examples of Similar Data Breaches
Numerous data breaches have occurred across various sectors, impacting millions of users. These breaches reveal common vulnerabilities and highlight the importance of proactive security measures.
- Yahoo (2013-2014): This massive breach exposed the personal information of billions of users, including passwords, email addresses, and other sensitive data. The cause was attributed to a combination of factors, including weak security practices, inadequate monitoring systems, and a failure to patch vulnerabilities. The consequences included financial losses, reputational damage, and legal actions. Users lost significant trust in Yahoo’s ability to protect their data.
The breach served as a stark reminder of the importance of robust security protocols and regular vulnerability assessments.
- Equifax (2017): This breach exposed the personal information of over 147 million consumers, including names, addresses, social security numbers, and credit report information. The cause was a critical vulnerability in a third-party application. The consequences were far-reaching, with individuals facing identity theft, financial fraud, and the emotional toll of compromised personal information. The breach underscored the risk of third-party dependencies and the importance of thorough vendor due diligence.
- Colonial Pipeline (2021): This incident involved a ransomware attack that disrupted fuel supplies across the southeastern United States. The breach highlighted the vulnerabilities of critical infrastructure to cyberattacks. The consequences included significant financial losses, operational disruption, and public anxiety. This breach demonstrated the growing threat of cyberattacks against vital infrastructure and the need for enhanced cybersecurity measures for such systems.
Lessons Learned from Past Breaches
Analyzing these breaches reveals critical lessons for both individuals and organizations.
- Proactive Security Measures: Implementing robust security protocols, such as multi-factor authentication, regular security audits, and penetration testing, is essential to prevent breaches. This includes not just the technical aspects, but also policies and procedures.
- Data Minimization: Collecting only the necessary data and implementing strong access controls are vital for protecting user privacy. Storing less sensitive data reduces the risk of exposure.
- Third-Party Risk Management: Thoroughly vetting and managing third-party vendors is critical. This ensures that dependencies do not create security vulnerabilities.
Comparative Analysis of Data Breaches
A table summarizing key characteristics of different data breaches can provide a clearer picture of their scope and impact.
| Breach | Affected Users | Cause | Consequences |
|---|---|---|---|
| Yahoo (2013-2014) | Billions | Weak security practices, inadequate monitoring | Financial losses, reputational damage, legal actions |
| Equifax (2017) | Over 147 million | Vulnerability in a third-party application | Identity theft, financial fraud, emotional distress |
| Colonial Pipeline (2021) | Millions (indirectly) | Ransomware attack | Significant financial losses, operational disruption, public anxiety |
Impact on User Trust
Data breaches erode user trust in organizations and the overall digital ecosystem. The long-term impact can be substantial.
The loss of trust can lead to reduced user adoption, decreased revenue, and reputational damage.
- Long-term Impact: The damage to trust can linger for years, potentially affecting customer loyalty and brand perception.
- Customer Retention: Users who have experienced a breach may be less likely to trust or use the affected service in the future.
Illustrative Examples of Data Breaches
Visual representations can aid in understanding the various types of data breaches.
Closure
The Whisper app data breach, impacting nearly 900 million users, serves as a stark reminder of the vulnerabilities inherent in handling sensitive personal information. The potential ramifications, including financial losses, reputational damage, and legal repercussions, are significant. Ultimately, this incident emphasizes the importance of robust security measures, user education, and stringent regulations to safeguard user data and prevent similar breaches in the future.
Users must also take proactive steps to protect themselves, including password changes and account monitoring.






