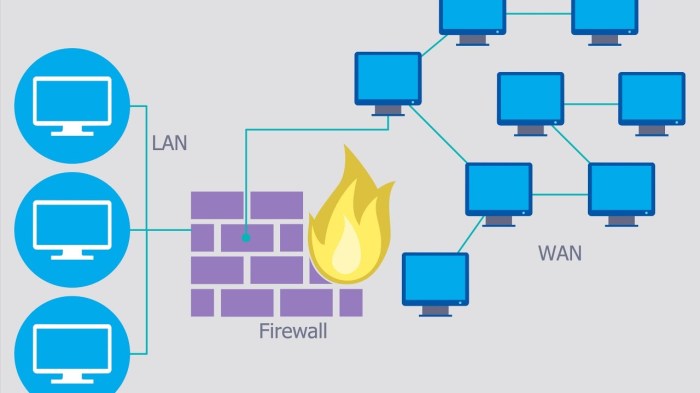
What is a virtual firewall? It’s a powerful tool for securing your network, but understanding its inner workings is crucial. This guide delves into the specifics, from its core functionalities and components to its implementation and management. Learn how virtual firewalls protect against a wide range of network threats and the best practices for securing them.
Virtual firewalls are essentially software-based versions of traditional firewalls, providing network security without the need for dedicated hardware. They analyze and filter network traffic, allowing or blocking connections based on predefined rules. Different types of virtual firewalls, like software-based and hardware-based, each offer their own set of advantages and disadvantages. This in-depth exploration examines the various facets of virtual firewall technology, ensuring a comprehensive understanding.
Defining Virtual Firewalls
A virtual firewall is a security system that acts as a gatekeeper for network traffic, but instead of residing on physical hardware, it operates within a virtualized environment. This approach offers flexibility and scalability, making it ideal for modern, dynamic network architectures. It’s a crucial component in protecting sensitive data and resources from unauthorized access.Virtual firewalls employ sophisticated rules and policies to inspect and control incoming and outgoing network traffic.
A virtual firewall acts like a digital gatekeeper, protecting your network from unwanted intrusions. Thinking about upgrading your phone? Considering the Pixel 9a? A good virtual firewall is crucial for online security, whether you’re using a powerful desktop or a smaller mobile device. Ultimately, a virtual firewall ensures your online activities stay safe and secure, much like a strong defense mechanism for your digital world.
should you upgrade to the pixel 9a might be a factor in your decision, but always prioritize security measures like a virtual firewall.
This inspection process involves evaluating various factors, including source and destination addresses, ports, protocols, and content. By selectively allowing or blocking traffic based on predefined rules, virtual firewalls effectively mitigate security threats.
Core Functionalities of a Virtual Firewall
Virtual firewalls perform a range of tasks to safeguard networks. These include packet filtering, stateful inspection, intrusion prevention, and application-level filtering. Packet filtering examines the headers of network packets to identify and block malicious traffic. Stateful inspection, on the other hand, tracks ongoing connections to identify and prevent attacks that exploit established connections. Intrusion prevention systems actively monitor network traffic for suspicious activities and block malicious behavior.
Application-level filtering inspects the content of applications to detect and prevent malicious code or unauthorized activities.
Key Differences Between Physical and Virtual Firewalls
Physical firewalls are hardware-based devices, often requiring dedicated physical space and potentially high upfront costs. They are generally more robust and can handle high volumes of traffic. Virtual firewalls, however, reside on virtual machines, enabling deployment and management across different platforms. Their configuration is often easier, allowing for quick adjustments and easier scaling. This agility makes virtual firewalls well-suited for dynamic environments.
A key difference lies in their implementation: physical firewalls are dedicated hardware, while virtual firewalls are software running on a virtual machine.
A virtual firewall acts like a gatekeeper for your network, controlling incoming and outgoing traffic. It’s a crucial security measure, like a bouncer at a club, only instead of people, it’s data. Speaking of protecting your digital assets, did you see that awesome deal on a refurbished Eufy RoboVac 11S Slim Self-Charging Robot Vacuum? grab refurb eufy robovac 11s slim self charging robot vacuum sale 120 It’s a steal! Ultimately, a virtual firewall is your digital defense, keeping your sensitive information safe, just like a well-maintained home security system.
Types of Virtual Firewalls
Virtual firewalls are available in various forms, each with its own strengths and weaknesses. Software-based virtual firewalls are often integrated into existing operating systems and virtualized platforms. They typically offer greater flexibility and lower initial costs but may have limitations in handling high traffic loads. Hardware-based virtual firewalls are designed specifically for high-performance environments and offer greater scalability and reliability.
They often leverage dedicated hardware resources for improved performance.
Comparison of Virtual Firewall Technologies
| Technology | Strengths | Weaknesses |
|---|---|---|
| Software-Based Virtual Firewalls | Lower initial cost, greater flexibility, easier to deploy and manage, often integrated with existing infrastructure. | Potentially lower performance, limited scalability for high-traffic environments. |
| Hardware-Based Virtual Firewalls | Higher performance, greater scalability for high-traffic environments, improved security through dedicated hardware, increased reliability. | Higher initial cost, less flexible in configuration compared to software solutions, may require specialized expertise for deployment and maintenance. |
| Cloud-Based Virtual Firewalls | Scalability, high availability, simplified management, often included in cloud service offerings. | Dependence on the cloud provider, potential security concerns related to cloud infrastructure. |
Virtual Firewall Components
Virtual firewalls, unlike their physical counterparts, exist entirely within software. Understanding their inner workings, specifically the components that make them tick, is crucial to appreciating their power and versatility in network security. These components are carefully orchestrated to create a robust defense against threats, ensuring a secure digital environment.The core components of a virtual firewall are intricately interconnected, each playing a vital role in the overall security posture.
A virtual firewall acts like a digital gatekeeper, protecting your network from unauthorized access. It’s like a sophisticated security system, constantly monitoring and filtering network traffic. Speaking of impressive deals, this impressive all in one vacuuming and mopping system is back to record low of 540, making it a steal! But back to firewalls, they help ensure only legitimate traffic passes through, keeping your data safe and your devices secure.
These components work in tandem to inspect and filter network traffic, enforcing security policies and safeguarding sensitive data. The synergy between these components is critical to the firewall’s effectiveness, as a weakness in one component can compromise the entire system.
Essential Components
The efficacy of a virtual firewall hinges on the coordinated operation of several key components. These components work together to create a layered security approach. Each component contributes a unique function to the overall security mechanism.
- Packet Inspection Engine: This component is the heart of the firewall. It meticulously examines each packet of data traversing the network. This examination involves verifying the packet’s origin, destination, and payload against predefined security rules. Sophisticated packet inspection engines can identify and block malicious packets even if they use obfuscation techniques. By carefully analyzing the header and payload data, it determines whether to allow or deny access.
- Rule Base Management System: This system houses the set of rules that govern traffic flow. Rules are defined to control which traffic is allowed and which is blocked. These rules are often based on source and destination IP addresses, ports, protocols, and other criteria. The rules can be modified dynamically to adapt to evolving threats or changing network needs. Maintaining an up-to-date rule base is essential to ensure the firewall’s effectiveness.
- Network Address Translation (NAT) Component: This crucial component translates private IP addresses to public IP addresses and vice-versa. This functionality is essential for security, enabling private networks to communicate with the internet. NAT also masks internal network structures, making it more difficult for attackers to identify and target specific devices. It plays a crucial role in both network security and privacy.
- Security Information and Event Management (SIEM) Integration: This integration enables the firewall to gather and analyze security logs. This data helps identify potential threats and suspicious activities. Real-time monitoring and analysis provide critical insights into network behavior, enabling proactive threat detection and response. This integration facilitates a comprehensive security posture.
Interaction and Architecture
A virtual firewall’s architecture can be visualized as a series of interconnected components. Each component communicates with others to process and filter network traffic. The packet inspection engine receives data from the network interface and analyzes it against the rules defined in the rule base. If a packet violates a rule, it is blocked; otherwise, it is allowed to proceed.
The NAT component manages IP address translations, shielding internal networks from direct external access. The SIEM integration collects logs and analyzes them for potential threats. This holistic approach provides comprehensive network protection.
| Component | Role | Interaction with other components |
|---|---|---|
| Packet Inspection Engine | Examines network packets | Consults the rule base and the NAT component |
| Rule Base Management System | Defines security policies | Guides the packet inspection engine |
| NAT Component | Handles IP address translations | Interacts with the packet inspection engine |
| SIEM Integration | Monitors and analyzes security events | Integrates with all other components to provide comprehensive security analysis |
“A well-configured virtual firewall acts as a sophisticated gatekeeper, ensuring only authorized traffic passes through while blocking malicious attempts.”
Virtual Firewall Functions
Virtual firewalls are crucial for safeguarding networks from a multitude of threats. They act as a gatekeeper, inspecting and controlling network traffic to prevent unauthorized access and malicious activity. This sophisticated layer of defense is essential in today’s interconnected digital landscape.Virtual firewalls provide a flexible and scalable security solution, adapting to the dynamic needs of modern organizations. They operate by analyzing network packets, comparing them against predefined security rules, and making decisions about whether to allow or deny access.
This dynamic process ensures that authorized users and applications can communicate securely while blocking harmful traffic.
Security Functions of a Virtual Firewall
Virtual firewalls offer a comprehensive set of security functions, including packet filtering, intrusion prevention, and application control. These functions work together to create a robust defense against a wide array of network threats.
Protecting Against Network Threats
Virtual firewalls protect against various network threats by actively monitoring and controlling network traffic. They identify and block malicious activities like denial-of-service attacks, malware distribution, and unauthorized access attempts. This proactive approach significantly reduces the risk of network compromise.
Examples of Mitigated Network Threats
Virtual firewalls effectively mitigate a range of network threats. For instance, they can prevent distributed denial-of-service (DDoS) attacks by identifying and blocking malicious traffic flooding a network. They can also prevent unauthorized access to sensitive data by blocking connections from suspicious IP addresses. Furthermore, they can stop the spread of malware by blocking infected files and connections.
Mechanisms for Controlling Network Traffic
Virtual firewalls utilize various mechanisms to control network traffic. These include packet filtering, stateful inspection, and application awareness. Packet filtering examines the headers of network packets, while stateful inspection maintains a record of active connections to detect malicious activity. Application awareness identifies applications communicating across the network, allowing for more granular control over traffic.
Supported Security Protocols
Virtual firewalls support a wide array of security protocols, ensuring compatibility with various network applications and services. This comprehensive support allows for seamless integration with existing infrastructure and applications.
| Protocol | Description | Security Features |
|---|---|---|
| TCP (Transmission Control Protocol) | A connection-oriented protocol that guarantees reliable data delivery. | Ensures ordered delivery and error checking, preventing data loss. |
| UDP (User Datagram Protocol) | A connectionless protocol that provides faster data transmission, sacrificing reliability. | Offers faster data transmission, useful for applications like streaming media where speed is critical. |
| HTTP (Hypertext Transfer Protocol) | The protocol used for transferring web pages. | Can be secured with HTTPS (HTTP Secure) for encrypting communication. |
| HTTPS (HTTP Secure) | A secure version of HTTP using SSL/TLS encryption. | Provides secure communication by encrypting data transmitted between web browsers and servers. |
| SSH (Secure Shell) | A protocol for secure remote login and command execution. | Provides secure remote access to servers and systems. |
Virtual Firewall Implementation

Implementing a virtual firewall involves a series of steps and configurations tailored to the specific network environment. Careful planning and execution are crucial to ensure the firewall effectively protects the network resources while allowing authorized traffic to flow unimpeded. This process involves configuring the firewall’s components, defining security policies, and deploying the solution in the target network.
Step-by-Step Implementation Procedure
A systematic approach is essential for a successful virtual firewall implementation. The procedure involves several key stages.
- Assessment and Planning: This initial phase focuses on understanding the network infrastructure, identifying potential security threats, and determining the required security policies. The assessment should identify existing security measures and evaluate their effectiveness. Thorough network mapping and analysis are critical to determine the scope of protection needed.
- Firewall Selection and Deployment: Choosing the right virtual firewall solution is crucial. Consider factors such as scalability, performance, and compatibility with existing network infrastructure. The deployment phase involves installing and configuring the virtual firewall on the chosen platform. This may include setting up virtual machines (VMs) or leveraging cloud-based solutions. The choice will depend on factors such as available resources and desired level of control.
- Configuration of Security Policies: Security policies define the rules that govern network traffic. These rules specify which traffic is allowed or blocked. The policies must align with the organization’s security requirements and risk tolerance. Example policies include allowing access to specific web servers while blocking malicious traffic originating from known threat actors.
- Network Integration and Testing: Integrating the virtual firewall into the existing network involves configuring routing and firewall rules. Comprehensive testing is crucial to ensure the firewall functions as expected. Tests should cover various scenarios, including authorized traffic flow and attempts to access restricted resources. This step is vital for detecting potential vulnerabilities or misconfigurations.
- Monitoring and Maintenance: Continuous monitoring and maintenance are essential to ensure the firewall’s effectiveness. Monitoring tools track network traffic, identify security breaches, and provide insights for improving policies. Regular maintenance includes updating the firewall’s software and reviewing security policies to adapt to evolving threats.
Necessary Configurations and Settings, What is a virtual firewall
The configuration settings for a virtual firewall significantly impact its functionality.
- Network Interfaces: Defining the network interfaces the firewall will monitor and control is paramount. This includes specifying which physical or virtual interfaces the firewall will use for inbound and outbound traffic. This step directly impacts the firewall’s scope of protection.
- Security Policies: These policies dictate which traffic is allowed or blocked. These rules are crucial for establishing a robust security posture. Examples include permitting access to specific web servers or blocking access from known malicious IP addresses.
- Authentication Mechanisms: Implementing authentication mechanisms like username/password or certificates ensures that only authorized users or devices can access the network. This enhances the firewall’s ability to prevent unauthorized access.
- Logging and Reporting: Enabling comprehensive logging and reporting mechanisms allows for analysis of network traffic and identification of potential security breaches. This data can help administrators understand security events, identify trends, and improve security policies.
Configuring Security Policies in a Virtual Firewall
Configuring security policies is crucial for defining the rules governing network traffic.
- Rule Creation: Rules specify which traffic is allowed or blocked based on criteria like source and destination IP addresses, ports, protocols, and applications. Clear and precise rule definitions are essential to avoid conflicts and unintended consequences.
- Rule Prioritization: Ordering rules based on priority is essential for handling complex traffic patterns. This ensures that more critical rules are evaluated first. This ensures the most crucial security measures are implemented first.
- Rule Testing: Thorough testing of rules is essential to verify their effectiveness and identify any potential issues. This process can include simulating various scenarios and observing the firewall’s response.
Considerations for Different Network Environments
The deployment of a virtual firewall must consider the specific characteristics of the network environment.
- Cloud Environments: Virtual firewalls in cloud environments must handle dynamic IP addresses and network configurations. This requires robust mechanisms for adapting to changes in the cloud infrastructure.
- On-Premise Networks: On-premise virtual firewalls need to be integrated with the existing network infrastructure, taking into account static IP addresses and fixed network topologies. This requires careful consideration of existing routing protocols and network devices.
- Hybrid Environments: Hybrid environments combining on-premise and cloud components require virtual firewalls that can seamlessly manage traffic across both domains. This necessitates careful configuration and monitoring of traffic flowing between the two environments.
Flow Chart for Virtual Firewall Setup
A flow chart visually represents the steps involved in setting up a virtual firewall. The chart details the stages from initial assessment to final maintenance.
(A visual flow chart is not possible in this text-based format. A flow chart would typically use boxes, arrows, and text to depict the steps and their relationships.)
Virtual Firewall Management
Virtual firewalls, while offering robust security, require diligent management to maintain optimal performance and security posture. Effective management encompasses monitoring performance, troubleshooting issues, implementing regular updates, and utilizing security logs. This ensures the firewall remains a reliable barrier against threats and effectively protects the network.
Monitoring Virtual Firewall Performance
Regular monitoring of key metrics is crucial to identify potential performance bottlenecks or security breaches early. This involves tracking CPU utilization, memory consumption, network throughput, and packet drop rates. Monitoring tools often provide graphical representations of these metrics, allowing for quick identification of trends and anomalies. This proactive approach allows for swift intervention to prevent potential issues from escalating.
Troubleshooting Virtual Firewall Issues
Troubleshooting virtual firewall problems requires a systematic approach. Detailed logs, system diagnostics, and thorough understanding of firewall configurations are essential. Identifying the source of the issue is paramount to effective resolution. This involves examining firewall rules, analyzing network traffic patterns, and reviewing security logs for suspicious activity.
Importance of Regular Updates and Maintenance
Regular updates and maintenance are vital for a virtual firewall’s security and stability. Updates often include security patches to address vulnerabilities, performance improvements, and new features. Implementing these updates promptly mitigates the risk of exploitation by malicious actors. Proactive maintenance schedules minimize the potential for downtime and ensure optimal performance.
Role of Security Logs in Virtual Firewall Management
Security logs provide invaluable insights into the firewall’s activity. They document all network traffic, access attempts, and security events. Analyzing these logs helps identify malicious activity, assess security breaches, and track user behavior. This detailed record is essential for incident response and compliance audits.
Tools and Techniques for Monitoring and Managing Virtual Firewalls
Effective management of virtual firewalls relies on appropriate tools and techniques. The following table highlights some common options:
| Tool/Technique | Description | Use Case |
|---|---|---|
| SolarWinds Network Performance Monitor | Provides comprehensive network performance monitoring, including virtual firewall metrics. | Identifying bottlenecks, tracking throughput, and monitoring CPU utilization. |
| Wireshark | Powerful network protocol analyzer for deep packet inspection. | Troubleshooting connectivity issues, analyzing suspicious traffic, and verifying firewall rules. |
| Firewall Management Console | Built-in tools for configuring, monitoring, and managing the virtual firewall. | Configuring firewall rules, monitoring performance, and generating security reports. |
| Security Information and Event Management (SIEM) Systems | Centralized system for collecting and analyzing security logs from various sources, including virtual firewalls. | Identifying security threats, correlating events, and generating comprehensive security reports. |
| Regular Vulnerability Scans | Automated scans to identify potential vulnerabilities in the firewall and network infrastructure. | Proactively mitigating potential security risks. |
Virtual Firewall Use Cases

Virtual firewalls have revolutionized network security, offering a flexible and adaptable approach to protecting sensitive data. Their ability to integrate seamlessly into various environments, from traditional on-premises networks to dynamic cloud deployments, makes them a critical component of modern security architectures. This adaptability extends to diverse use cases, addressing specific needs across a wide spectrum of organizations.Virtual firewalls are not just a theoretical concept; they’re actively deployed in numerous scenarios to bolster security.
From safeguarding corporate data centers to protecting sensitive information in cloud-based applications, virtual firewalls provide a crucial layer of defense. This adaptability allows for tailored security policies and rapid response to emerging threats.
Examples of Virtual Firewall Deployments
Virtual firewalls are versatile tools that find applications in diverse scenarios. They can be deployed in a variety of environments, such as small businesses and large enterprises, and for various purposes. A few examples include:
- Protecting cloud-based applications: Virtual firewalls can be deployed within virtualized environments to safeguard applications hosted on cloud platforms like AWS, Azure, or Google Cloud. This ensures that only authorized users and devices can access the applications, preventing unauthorized access and data breaches.
- Securing remote access networks: Virtual firewalls can control access to internal networks for remote users. This enables secure access while preventing unauthorized individuals from accessing sensitive information. A crucial aspect of this use case is ensuring the integrity of the network connection, especially in environments where users connect from diverse locations and devices.
- Creating isolated network segments: Virtual firewalls can create isolated segments within a network. This is particularly useful in preventing unauthorized access between different departments or applications. This is especially critical in organizations handling sensitive data, where strict segregation of networks is crucial to prevent breaches.
Protecting Sensitive Data with Virtual Firewalls
Virtual firewalls play a pivotal role in safeguarding sensitive data. They provide a controlled and secure pathway for data access, preventing unauthorized individuals from gaining access. This is achieved through granular control over network traffic, allowing administrators to define specific rules to permit or deny access based on various criteria, such as source IP address, destination port, or application type.
- Data loss prevention: Virtual firewalls can be configured to block specific types of data from leaving the network. This helps prevent sensitive data from falling into the wrong hands, particularly in situations where data is being transmitted to external partners or clients.
- Compliance with regulations: Many industries are subject to strict data protection regulations (e.g., HIPAA, PCI DSS). Virtual firewalls can help organizations meet these compliance requirements by enforcing strict access controls and monitoring network traffic.
- Threat detection and response: Virtual firewalls often include intrusion detection and prevention systems (IDS/IPS). These systems can detect malicious activity and take immediate action to mitigate the threat, reducing the risk of data breaches.
Virtual Firewalls in Cloud Environments
Virtual firewalls are ideally suited for cloud environments due to their flexibility and scalability. They can be easily provisioned and scaled up or down as needed to accommodate fluctuating demand. This adaptability is a significant advantage in dynamic cloud environments.
- Scalability: Virtual firewalls can scale to meet the needs of a growing organization or application, automatically adjusting to changes in network traffic.
- Flexibility: Virtual firewalls allow for rapid deployment and configuration changes, enabling organizations to quickly respond to evolving security threats.
- Cost-effectiveness: Virtual firewalls often offer a more cost-effective solution compared to traditional firewalls, especially in cloud environments where resources can be provisioned and scaled as needed.
Advantages over Traditional Firewalls
Virtual firewalls offer several advantages over traditional firewalls, including flexibility, scalability, and cost-effectiveness.
- Flexibility: Virtual firewalls can be easily moved and reconfigured within a network, offering greater flexibility in adapting to changing security needs.
- Scalability: Virtual firewalls can be easily scaled up or down to accommodate fluctuating network traffic, ensuring optimal performance and security even under heavy load.
- Cost-effectiveness: Virtual firewalls can often be more cost-effective than traditional firewalls, especially in cloud environments, where resources can be provisioned as needed.
Real-World Case Studies
Several organizations have successfully implemented virtual firewalls to bolster their security posture. While specific case studies are often confidential, the positive impact of virtual firewalls on security is widely recognized.
- Improved security posture: Virtual firewalls have proven effective in reducing security breaches and improving the overall security posture of organizations.
- Reduced operational costs: Virtualization often leads to reduced operational costs associated with hardware and maintenance, making virtual firewalls a more economical choice.
- Enhanced agility: The agility of virtual firewalls allows organizations to quickly adapt to evolving security threats and changing business needs.
Virtual Firewall Security Best Practices: What Is A Virtual Firewall
Virtual firewalls, while offering robust security, require diligent management to maintain their effectiveness. Proper implementation of security best practices is crucial to prevent unauthorized access and maintain the integrity of the network they protect. These practices encompass a range of measures, from strong passwords and access controls to regular audits and configuration hardening. Implementing these best practices minimizes the risk of vulnerabilities and ensures the virtual firewall remains a reliable security shield.A well-secured virtual firewall is a vital component of any robust cybersecurity strategy.
By understanding and adhering to best practices, organizations can significantly reduce the likelihood of security breaches and maintain the confidentiality, integrity, and availability of their data and systems.
Strong Passwords and Access Controls
Effective password management and strict access control are foundational to a secure virtual firewall. Weak passwords are a common point of vulnerability. Implementing strong password policies, including mandatory complexity requirements and regular password changes, mitigates this risk. Furthermore, implementing multi-factor authentication (MFA) adds another layer of security, making unauthorized access significantly harder. Enforcing least privilege access control principles ensures that users only have the necessary permissions to perform their tasks, limiting the potential impact of a compromised account.
Regular Security Audits
Regular security audits are essential to identify vulnerabilities and weaknesses in the virtual firewall configuration. These audits should assess the firewall’s rules, policies, and configurations for potential misconfigurations, outdated protocols, and other weaknesses. This proactive approach helps organizations stay ahead of potential threats and ensure the firewall remains a reliable security mechanism. By regularly reviewing logs and system events, organizations can identify anomalies and respond swiftly to potential security incidents.
Hardening the Virtual Firewall
Hardening a virtual firewall involves implementing measures to reduce the attack surface and make it more resistant to exploits. This includes disabling unnecessary services and protocols, restricting access to management interfaces, and configuring appropriate logging mechanisms. Regularly updating the firewall’s firmware and software is essential to patch known vulnerabilities. This proactive approach ensures the firewall is equipped with the latest security features and safeguards against emerging threats.
Using strong, well-documented rulesets is a critical aspect of this hardening process.
Security Best Practices for Managing Virtual Firewall Configurations
Managing virtual firewall configurations effectively is critical to maintaining security. A well-documented configuration allows for easier troubleshooting and modification. Creating a detailed configuration manual and following a consistent change management process are crucial for maintaining a secure and predictable environment. Regular backups of firewall configurations and logs are important for disaster recovery and incident response. Furthermore, implementing automated tools for configuration management can help to streamline the process and minimize errors.
Adherence to industry best practices and established security standards, like NIST guidelines, can further enhance the security posture of the firewall.
- Configuration Documentation: Thorough documentation of firewall rules, policies, and configurations is essential for future troubleshooting and maintenance. This documentation should be readily accessible to authorized personnel and updated regularly.
- Change Management Procedures: Implementing a formal change management process for modifying firewall configurations ensures that all changes are documented, reviewed, and tested before implementation. This minimizes the risk of unintended consequences and errors.
- Regular Backups: Regularly backing up firewall configurations and logs is vital for disaster recovery and incident response. These backups should be stored securely in an offsite location to protect against data loss.
- Automated Configuration Management: Implementing automated tools for configuration management can streamline the process and reduce the risk of errors. These tools can also help to ensure consistency and compliance with security policies.
End of Discussion
In conclusion, understanding virtual firewalls is essential for anyone responsible for network security. From defining their role to implementing and managing them effectively, this guide has provided a comprehensive overview. By understanding the components, functions, and best practices, you can confidently deploy and manage a virtual firewall that protects your network effectively. This comprehensive exploration of virtual firewalls equips you with the knowledge to navigate the complex world of network security.