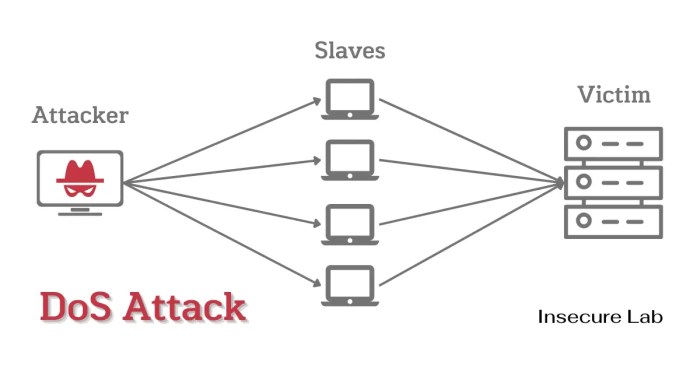
What is a denial of service attack dos – What is a denial of service attack (DoS)? It’s a malicious attempt to disrupt the normal functioning of a website, service, or network by overwhelming it with traffic. Imagine a crowded highway, so congested that legitimate traffic can’t get through. This digital highway robbery is a common tactic employed by hackers to cause havoc and sometimes extort money from their targets.
Understanding the different types of DoS attacks, the techniques they use, and the potential impact is crucial for anyone looking to safeguard their online presence. This post delves into the various facets of DoS attacks, examining their mechanics, consequences, and mitigation strategies. We’ll also look at real-world examples and the mindset of the attackers.
Defining a Denial-of-Service Attack (DoS)
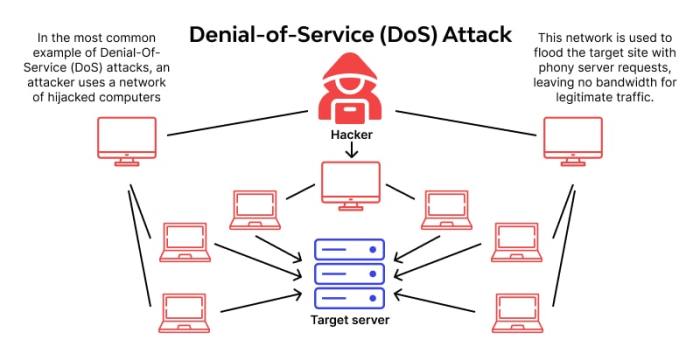
A denial-of-service (DoS) attack is a malicious attempt to disrupt the normal functioning of a network, website, or online service. It aims to overwhelm the target with a flood of requests, rendering it inaccessible to legitimate users. These attacks exploit vulnerabilities in the target’s infrastructure or applications, often aiming to cause significant disruption and financial loss.The fundamental objective of a DoS attack is to deny legitimate users access to a service or resource.
This can range from a simple inconvenience to a complete shutdown, depending on the severity and sophistication of the attack. The attacker’s goal is to overload the target system, exhausting its resources and preventing it from responding to legitimate requests.
A denial-of-service attack (DoS) essentially floods a system with requests, overwhelming it and preventing legitimate users from accessing it. Sometimes, these attacks can be surprisingly simple, like a coordinated effort from many devices. If you’re having similar issues with your PS4, checking out the PlayStation 4 complete troubleshooting guide might offer some helpful hints on common problems.
Ultimately, DoS attacks are designed to disrupt services, making it difficult for anyone to use the targeted system.
Types of DoS Attacks
DoS attacks come in various forms, each targeting different aspects of a system. Understanding these variations is crucial for effective defense strategies. Different types of DoS attacks leverage distinct methods to achieve their goal.
Flooding Attacks
Flooding attacks are a common type of DoS attack, characterized by overwhelming the target with a massive volume of traffic. This flood of requests consumes the target’s resources, making it unresponsive to legitimate users. These attacks often originate from numerous compromised systems, forming a botnet.
Application-Layer Attacks
Application-layer attacks, also known as Layer 7 attacks, target the application level of a network. These attacks exploit vulnerabilities in the application’s logic, often using sophisticated techniques to avoid detection. They can be harder to mitigate than flooding attacks, as they often appear legitimate to security systems.
Comparison of DoS Attack Types
| Attack Type | Method | Impact | Example |
|---|---|---|---|
| SYN Flood | Exploits the TCP three-way handshake by sending numerous SYN packets without completing the connection. The target server reserves resources for these incomplete connections, exhausting its capacity. | Server becomes unresponsive, legitimate users cannot access services. | A botnet flooding a web server with SYN packets. |
| UDP Flood | Sends a massive volume of UDP packets to the target. The target must process each packet, consuming significant bandwidth and processing power. | High bandwidth consumption, network congestion, and server overload. | A large number of compromised devices sending UDP packets to a DNS server. |
| HTTP Flood | Generates a high volume of HTTP requests to the target server, often using compromised systems. | Consumes server resources, rendering it unavailable to legitimate users. | A botnet sending thousands of HTTP GET requests to a web application. |
| Application-Layer Attacks (e.g., Slowloris) | Sustained attacks that send incomplete or slowly-crafted HTTP requests, tying up server resources. | Target server resources are consumed slowly but persistently. | An attacker using a tool like Slowloris to send incomplete HTTP requests to a web application. |
Attack Mechanisms and Techniques
Denial-of-service (DoS) attacks aim to overwhelm a target system, rendering it unavailable to legitimate users. Understanding the diverse mechanisms and techniques behind these attacks is crucial for effective defense strategies. Attackers leverage vulnerabilities in network infrastructure and application logic to disrupt services, often employing sophisticated methods to evade detection.Attackers exploit various weaknesses in target systems to launch DoS attacks.
These exploits often involve manipulating network protocols or system resources to create a flood of illegitimate requests or activities. This barrage overwhelms the target’s capacity to handle legitimate requests, leading to service disruptions.
Common Attack Mechanisms
DoS attacks employ various methods to overwhelm a target. These methods often exploit vulnerabilities in network protocols or application logic, resulting in a deluge of illegitimate requests or activities. This inundation overwhelms the target’s capacity to handle legitimate requests, thereby disrupting services.
SYN Flood
A SYN flood attack is a common type of DoS attack that exploits the TCP three-way handshake. Attackers send a massive number of SYN packets to the target server without completing the handshake. The server allocates resources to handle these incomplete connections, consuming its resources and preventing it from responding to legitimate connections. This type of attack is effective because it ties up server resources without requiring the attacker to maintain a persistent connection.
UDP Flood
UDP flood attacks send a large volume of User Datagram Protocol (UDP) packets to the target. These packets often have random source ports, making it difficult to filter them out. Since UDP is connectionless, the target server has to process each packet, consuming processing power and network bandwidth. This continuous barrage of UDP packets can overwhelm the target’s resources, leading to a denial of service.
HTTP Flood
HTTP flood attacks involve sending a large volume of HTTP requests to the target web server. These requests can be crafted in various ways, often utilizing different HTTP methods. The goal is to consume the server’s resources by overloading its processing capacity and bandwidth. By sending a large number of requests, the attacker can effectively prevent the server from responding to legitimate users.
Other Attack Vectors
Other attack vectors include fragmentation attacks, ping of death attacks, and amplification attacks. Fragmentation attacks exploit the way network packets are broken down and reassembled, potentially overwhelming the target. Ping of death attacks exploit the way network packets are structured and transmitted. Amplification attacks leverage vulnerable systems on the internet to amplify the impact of an attack.
So, a denial-of-service attack (DoS) floods a system with requests, basically overwhelming it and preventing legitimate users from accessing it. It’s like a massive traffic jam on the internet, and 1Password version 8’s new Windows release, with its download features detailed here , offers robust security to protect against such attacks. This makes it crucial to stay safe online, even from these types of digital traffic jams.
Steps in Executing a DoS Attack
The steps involved in executing a DoS attack often depend on the chosen method. Generally, it involves the following steps:
- Target Selection: Identifying a vulnerable or critical target is crucial.
- Attack Tool Preparation: Preparing the tools needed for the attack is essential, such as a botnet or a specially crafted script.
- Attack Initiation: Initiating the attack by sending a large volume of requests or data to the target.
- Monitoring and Adjustment: Monitoring the impact of the attack and adjusting the attack strategy as needed to maximize the impact and minimize detection.
Overwhelming the Target System, What is a denial of service attack dos
Attackers employ various strategies to overwhelm a target system, exploiting vulnerabilities and network limitations. This can involve coordinating multiple sources of attack to generate a high volume of traffic, using specialized tools to create massive volumes of traffic, or exploiting vulnerabilities to amplify the impact of the attack. Ultimately, the goal is to overload the target’s resources, preventing it from responding to legitimate requests.
Attack Methods, Resources Consumed, and Effects
| Attack Method | Resources Consumed | Effects on Target |
|---|---|---|
| SYN Flood | Server processing power, network bandwidth | Denial of service to legitimate users, server downtime |
| UDP Flood | Network bandwidth, server processing power | Denial of service to legitimate users, server downtime |
| HTTP Flood | Server processing power, network bandwidth | Denial of service to legitimate users, server downtime |
Impact and Consequences of DoS Attacks
Denial-of-Service (DoS) attacks, while often portrayed as a digital nuisance, can have devastating consequences for individuals, businesses, and even critical infrastructure. The impact extends far beyond simply inconveniencing users; it can cripple operations, damage reputations, and lead to significant financial losses. Understanding the multifaceted nature of these attacks is crucial for effective mitigation and prevention strategies.A successful DoS attack floods a target system with illegitimate requests, overwhelming its resources and rendering it unavailable to legitimate users.
This disruption can manifest in various ways, causing widespread problems depending on the target and the nature of the attack. The consequences are often more significant than the initial disruption, leading to cascading effects that can have long-lasting repercussions.
Financial Losses
DoS attacks inflict significant financial losses on targeted systems. For businesses, downtime directly translates into lost revenue, as online sales, customer service, and other critical operations are halted. The cost of lost productivity, including employee time spent on recovery efforts and the need to hire temporary staff to restore services, adds further to the financial burden. Furthermore, the need for emergency repairs and security upgrades adds significant expense to the recovery process.
Companies might also face penalties for service level violations or have to pay compensation to affected customers. Examples include online retailers experiencing massive sales losses during a prolonged attack, or e-commerce platforms facing hefty compensation demands from customers due to unavailable services.
Operational Disruptions
DoS attacks can completely disrupt the operational flow of targeted systems. Critical services, such as online banking, e-commerce platforms, and emergency services, become inaccessible, causing significant inconvenience and potentially serious problems. In the case of a healthcare organization, a DoS attack could disrupt patient records access, hindering timely medical treatment. For financial institutions, a DoS attack could halt transactions, causing significant financial instability.
The disruption in service also impacts the workflow of employees, creating a chaotic and unproductive environment.
Reputational Damage
A DoS attack can severely damage a company’s reputation. Customers lose trust when they are unable to access vital services or when their personal data is compromised. Negative publicity surrounding the attack can lead to a decline in customer loyalty and a loss of market share. A sustained attack can damage the company’s brand image and make it difficult to regain customer confidence.
The potential for customer loss and the difficulty in rebuilding trust makes reputational damage a significant consequence of a successful DoS attack. For example, a popular social media platform facing a widespread DoS attack might see a significant drop in user engagement and attract negative media attention, leading to long-term damage to its reputation.
Loss of Customer Trust
Loss of customer trust is a significant consequence stemming from the disruptions and security vulnerabilities exposed by a DoS attack. Users who are unable to access critical services or experience delays and frustration are likely to lose confidence in the organization’s ability to provide reliable services. This loss of trust can have a lasting impact on customer loyalty and future business dealings.
A damaged reputation can lead to a decreased number of new customers, as users seek out alternatives that are perceived as more secure and reliable. A notable example is a bank experiencing a prolonged DoS attack. Customers may lose faith in the bank’s security measures and transfer their funds to a competitor, leading to significant financial losses for the targeted institution.
Mitigation Strategies and Defenses
Denial-of-service (DoS) attacks pose a significant threat to online services and systems. Effective mitigation strategies are crucial to prevent or minimize the impact of these attacks. Robust defenses are essential for maintaining availability and ensuring the integrity of online resources. This section will delve into common mitigation strategies and defenses against DoS attacks.Comprehensive defense mechanisms often involve a multi-layered approach.
A single strategy may not be sufficient to fully protect against all types of DoS attacks, making a layered approach crucial for effective protection. These methods often involve a combination of network-level, application-level, and cloud-based solutions.
Firewall Implementation
Firewalls are a fundamental line of defense against DoS attacks. They act as gatekeepers, controlling the flow of network traffic and blocking malicious or unwanted connections. By configuring firewall rules to identify and block specific attack patterns, such as IP address spoofing or unusual traffic volumes, organizations can effectively prevent attackers from flooding their systems. Advanced firewalls can also perform deep packet inspection, enabling them to identify malicious payloads within network traffic.
This layered approach significantly enhances security.
Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play a vital role in detecting and responding to malicious activities, including DoS attacks. IDS systems monitor network traffic for suspicious patterns and alert administrators to potential threats. IPS systems, a more proactive approach, actively block malicious traffic identified by the system. These systems can analyze traffic volume, identify patterns indicative of DoS attacks, and take action to mitigate the impact.
They often complement firewall configurations to provide a more comprehensive security solution.
Traffic Filtering and Rate Limiting
Traffic filtering and rate limiting are crucial techniques in mitigating DoS attacks. Traffic filtering involves examining network traffic based on predefined rules. Malicious traffic can be identified and blocked, allowing legitimate traffic to pass through. Rate limiting controls the rate at which requests are processed from a single source. By limiting the number of requests per unit of time, organizations can prevent attackers from overwhelming their systems.
Denial-of-service attacks (DoS) are basically designed to overwhelm a system, like trying to flood a store with customers until it can’t handle any more orders. This can affect everything from your online gaming experience to crucial infrastructure. Imagine if the Playstation 5 beta 3D audio profiles remote play feature playstation 5 beta 3d audio profiles remote play was targeted with a DoS attack; the service would likely grind to a halt, making it impossible for anyone to access it.
So, essentially, a DoS attack is meant to disrupt a service by clogging it up.
For example, a server might allow a maximum of 10 requests per second from a single IP address. This technique is particularly effective against SYN flood attacks. These techniques often work in conjunction with other mitigation strategies.
Load Balancing and Redundancy
Distributing traffic across multiple servers through load balancing can effectively mitigate the impact of DoS attacks. If one server is targeted, the load can be distributed to other servers, preventing a complete outage. Redundancy is another key component, with multiple servers acting as backups. If one server is compromised or overwhelmed, another can seamlessly take over, ensuring continued service.
This approach is vital for maintaining high availability, even under attack.
Table of Mitigation Strategies
| Mitigation Strategy | Pros | Cons |
|---|---|---|
| Firewalls | Basic defense, relatively inexpensive, easy to implement | Limited effectiveness against sophisticated attacks, may require extensive configuration |
| IDS/IPS | Proactive detection and prevention, can identify various attack patterns | Can generate false positives, may require significant resources for implementation and maintenance |
| Traffic Filtering | Effective in blocking malicious traffic, improves performance by removing non-essential data | Requires careful configuration to avoid blocking legitimate traffic, may not detect all attack types |
| Rate Limiting | Simple and effective against many DoS attacks, can significantly reduce attack impact | Requires careful tuning to avoid blocking legitimate users, may need to be adapted to different attack patterns |
| Load Balancing and Redundancy | High availability, increased resilience to attacks, improved performance under normal conditions | Complex to implement and maintain, requires careful planning and resource allocation |
Case Studies and Real-World Examples
Denial-of-service (DoS) attacks are a persistent threat to online systems and services. Understanding past attacks provides valuable insights into their tactics and helps in developing effective mitigation strategies. This section examines significant DoS attacks, highlighting their technical aspects, impacts, and the methods used to combat them. By analyzing real-world examples, we can better anticipate and defend against future threats.Real-world DoS attacks often exploit vulnerabilities in network infrastructure or application design.
The severity of these attacks can range from minor inconveniences to major disruptions, impacting businesses, governments, and individuals. Studying these cases reveals critical information for strengthening security measures and developing proactive defense mechanisms.
Notable DoS Attacks Targeting Specific Industries
DoS attacks aren’t indiscriminate; they often target specific industries or organizations. Understanding the motivations behind these attacks is crucial for developing effective countermeasures. Financial institutions, e-commerce platforms, and online gaming services are frequently targeted due to their high transaction volumes and reliance on online infrastructure.
- Financial Institutions: Financial institutions are attractive targets due to the significant financial impact of service disruptions. Attacks often involve flooding servers with traffic, making legitimate transactions impossible. This can result in significant financial losses and reputational damage.
- E-commerce Platforms: Online retailers are vulnerable to DoS attacks during peak seasons, such as Black Friday or Cyber Monday, when high traffic volumes are expected. Attacks can overwhelm servers, leading to website outages and lost sales. Mitigation strategies for these types of attacks often involve implementing robust load balancing and traffic filtering mechanisms.
- Online Gaming Services: Online gaming platforms are also susceptible to DoS attacks, often motivated by competitive advantage or disrupting gameplay. These attacks can disrupt player experiences, causing frustration and potentially impacting player retention.
Technical Aspects of DoS Attacks
Understanding the technical methods behind DoS attacks is critical for developing effective countermeasures. These attacks exploit vulnerabilities in network protocols or application design.
- SYN Flood: A common DoS attack that exploits the TCP handshake process. Attackers send a large number of SYN requests to the target server, overwhelming its resources. The server responds to each SYN request, but never receives the corresponding acknowledgment (ACK), leaving connections in a half-open state. This consumes server resources and prevents legitimate connections.
- UDP Flood: This attack floods the target server with UDP packets, often using spoofed source IP addresses. The server responds to each packet, consuming bandwidth and resources, and eventually crashing the service. Because UDP connections are connectionless, they are often used for this type of attack.
- HTTP Flood: Attackers send a massive number of HTTP requests to the target website. The target server struggles to handle the requests, leading to website outages or performance degradation. This method can involve a distributed network of compromised machines to increase the attack’s impact.
Mitigation Strategies and Defenses
Effective mitigation strategies are crucial for defending against DoS attacks. These include network-level defenses, application-level controls, and proactive security measures.
- Traffic Filtering: Filtering out malicious traffic based on IP addresses, ports, or patterns can prevent attacks from reaching the target server.
- Load Balancing: Distributing traffic across multiple servers can help absorb the impact of an attack, preventing a single server from being overwhelmed.
- Rate Limiting: Restricting the rate at which requests are processed can help mitigate attacks that flood the server with requests.
Example of a Recent Impactful DoS Attack
In 2023, a large e-commerce platform experienced a significant DoS attack during the holiday shopping season. The attackers used a sophisticated combination of SYN floods and HTTP floods, targeting the platform’s web servers. The attack effectively brought the platform’s website down for several hours, resulting in substantial lost revenue and damaged customer trust. The platform mitigated the attack by implementing more robust load balancing and traffic filtering mechanisms, and by working with internet service providers to block malicious traffic.
This case highlights the importance of proactive security measures and the need for a layered defense approach to mitigate DoS attacks.
Understanding the Attacker’s Perspective: What Is A Denial Of Service Attack Dos
Denial-of-service (DoS) attacks are not simply acts of malice; they often stem from a complex interplay of motivations and objectives. Understanding the attacker’s mindset is crucial for developing effective defenses and mitigating the impact of these attacks. This section delves into the driving forces behind these attacks, the tools they employ, and the factors fueling their increasing sophistication.Attackers are not a monolithic group.
Their motivations range from personal vendettas to financial gain, political agendas, or even simple ego gratification. Comprehending these varied motivations is essential to anticipate and counter the ever-evolving tactics of these individuals.
Motivations Behind DoS Attacks
A wide spectrum of motivations drives attackers to launch DoS attacks. These range from personal grievances and online disputes to more organized attempts at disrupting services or causing reputational damage.
- Financial Gain: DoS attacks can be used to extort money from organizations. By disrupting services, attackers may demand payment to cease the attack, or they might target specific companies to cause financial loss through downtime or lost sales. This is often a motivating factor in attacks against e-commerce platforms or online gaming sites.
- Political Motivations: DoS attacks are occasionally used as tools for political expression or to target entities perceived as adversaries. These attacks can be part of broader campaigns to disrupt online services or communications. A notable example might be attacks against government websites or those of political opponents.
- Hacktivism: Hacktivists may use DoS attacks to express their political or social views, often targeting organizations or individuals they perceive as acting against their beliefs. These attacks are often intended to generate publicity or disruption rather than immediate financial gain.
- Ego and Status: The act of successfully disrupting a large network or website can be a source of pride for some attackers. The challenge of overcoming security measures and the resulting notoriety can serve as a powerful motivator.
Attacker Tools and Techniques
The arsenal of tools available to attackers has evolved significantly, enabling them to launch increasingly sophisticated and powerful DoS attacks.
- Simple Flooding Attacks: These involve overwhelming a target system with a massive volume of requests, typically from multiple sources. This can be achieved using tools that automate the generation of traffic. These are often the most basic forms of DoS attacks, but they can still be effective.
- Distributed Denial-of-Service (DDoS) Attacks: DDoS attacks leverage multiple compromised systems (a botnet) to flood the target with traffic. This amplifies the impact of the attack, making it far more difficult to mitigate. The scale of DDoS attacks can be enormous, rendering a service completely inaccessible.
- Application Layer Attacks: These attacks target specific vulnerabilities in applications, rather than overwhelming the network infrastructure. They can exploit weaknesses in the application’s logic or design to disrupt its functionality, often with a smaller number of requests than a simple flooding attack.
- Amplification Attacks: These attacks leverage vulnerable services to amplify the attack’s impact. By sending a small request to a vulnerable server, the attacker can trigger a much larger response directed at the target, overwhelming it with amplified traffic.
Factors Contributing to Attack Sophistication
Several factors contribute to the rising sophistication of DoS attacks. This includes the increasing accessibility of tools, the growth of botnets, and the development of more advanced attack techniques.
- Ease of Access to Attack Tools: The availability of readily accessible tools and scripts has lowered the barrier to entry for attackers, allowing even individuals with limited technical skills to launch attacks.
- Growth of Botnets: The scale and sophistication of botnets have increased significantly, enabling attackers to command vast networks of compromised systems to generate enormous amounts of malicious traffic.
- Advancement of Attack Techniques: Attackers are continually developing new and more sophisticated attack techniques, making existing defenses less effective. These techniques often target vulnerabilities in applications and network infrastructure that are not easily identified or mitigated.
- Increased Availability of Resources: The internet provides attackers with readily available resources, including information, tools, and support communities, making the learning curve shorter and easier to develop new attacks.
End of Discussion

In conclusion, DoS attacks are a significant threat in today’s digital landscape. Understanding the nuances of these attacks, from their methods to their consequences, is essential for protecting systems and networks. By comprehending the attacker’s perspective and implementing robust mitigation strategies, we can better defend against these increasingly sophisticated threats. Ultimately, knowledge is power in the face of digital aggression.