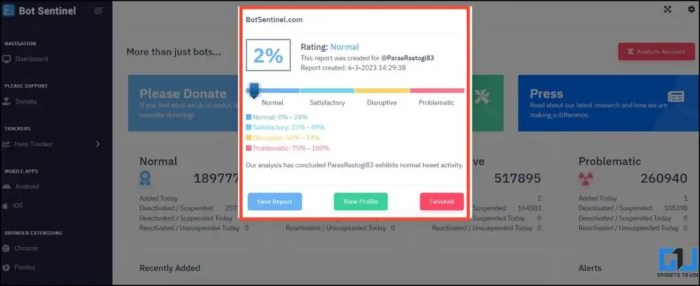
Twitter verified fake accounts botnet researcher delves into the intricate world of malicious actors leveraging Twitter’s verification system. These actors create sophisticated networks (botnets) to impersonate legitimate users, spreading misinformation and causing significant harm. The research examines how these verified fake accounts are created, the methods used, the motivations behind them, and the significant consequences of their actions.
It also explores the challenges in detection and mitigation, along with potential future trends.
This research will dissect the characteristics of these botnets, focusing on the vulnerabilities exploited by malicious actors to gain verification. We’ll also examine the various types of verified fake accounts, ranging from simple impersonation to more complex manipulation tactics. Furthermore, we’ll explore the impact on trust, the spread of misinformation, and the potential for real-world consequences.
Defining “Twitter Verified Fake Accounts Botnet”
A Twitter verified fake account botnet represents a sophisticated form of online manipulation. These networks exploit the platform’s verification system, creating deceptive accounts that masquerade as legitimate users, often with significant influence. This allows for widespread misinformation campaigns, targeted harassment, and coordinated attacks on individuals and organizations. The scale and complexity of these botnets raise serious concerns about the integrity of online discourse and the trustworthiness of information shared on social media.This intricate network leverages automated tools to generate, manage, and operate a large number of fraudulent accounts.
These accounts, often meticulously crafted to mimic authentic users, exploit vulnerabilities in Twitter’s verification processes. The resulting cascade of fabricated content and interactions can significantly distort public perception and sow confusion.
Verified Fake Account Characteristics
Verified fake accounts on Twitter are characterized by a combination of deceptive practices. They often utilize stolen identities, synthetic profiles, or carefully constructed personas to impersonate real individuals or organizations. These accounts are frequently linked to automated systems that create and manage multiple accounts, generating a high volume of activity. Furthermore, these accounts are often designed to mimic the behaviour of genuine users, including posting patterns and engagement.
Ever wondered about the shadowy world of Twitter verified fake accounts and botnet researchers? It’s a fascinating, albeit unsettling, area of digital security. The sheer scale of these operations is often staggering, and it highlights the need for robust security measures to combat them. Fortunately, there are solutions like smart stay systems to protect against these kinds of attacks.
What smart stay and why would you want it can provide a layered approach to security, which is crucial when dealing with sophisticated threats like this. The bottom line? Staying vigilant and proactively securing your digital environment is key to thwarting these nefarious actors.
Botnet Characteristics
A botnet specifically targeting verified accounts is designed to leverage the increased trust and visibility associated with verification. These botnets are usually composed of a significant number of verified or unverified accounts that work in concert. This coordinated effort amplifies the impact of the botnet’s activities, increasing the reach and effectiveness of the malicious actions.
Motivations Behind Creation and Use
The motivations behind creating and using such botnets are diverse and often intertwined. These include financial gain through advertising fraud, political manipulation, reputational damage, and extortion. Furthermore, they can be used for social engineering, spreading misinformation, or coordinating attacks on individuals or organizations.
Twitter Verification Methods and Vulnerabilities
Twitter’s verification process, while intended to enhance trust, has inherent vulnerabilities. The reliance on self-declaration, coupled with a lack of robust verification checks, creates a loophole that can be exploited by malicious actors. The process also has a reputation for being overly lenient, leading to the verification of accounts with questionable intentions. This lenient approach allows for the creation of fake accounts that can easily mimic real users.
Types of Verified Fake Accounts
Different types of verified fake accounts can be distinguished by their primary purpose. Impersonation accounts mimic the identity of celebrities, politicians, or public figures to spread misinformation or engage in harassment. Spam accounts are designed to promote products or services, often through misleading advertisements. Manipulation accounts are used to influence public opinion or create discord among groups.
Strategies for Creating and Operating Botnets
| Strategy | Description |
|---|---|
| Account Creation | Automated tools are used to create a large number of accounts, often with fake identities and details. |
| Verification Exploitation | Malicious actors exploit loopholes in Twitter’s verification process to obtain verified status for fake accounts. |
| Content Generation | Automated tools create and distribute a high volume of content, often through coordinated posting schedules and engagement patterns. |
| Account Management | Sophisticated tools are used to manage and control the activities of multiple accounts, including posting, liking, retweeting, and engaging in conversations. |
| Target Identification | Botnets identify and target specific individuals, organizations, or groups for malicious purposes. |
Impact and Consequences
The proliferation of verified fake accounts and botnets on platforms like Twitter poses a significant threat to the integrity of information and public discourse. These networks, often used for malicious purposes, can manipulate public opinion, spread misinformation, and undermine trust in legitimate sources. The consequences extend far beyond the digital realm, affecting social cohesion, economic stability, and even political landscapes.This insidious activity is not a theoretical concern; it has real-world ramifications, as demonstrated by numerous instances of coordinated campaigns aimed at influencing public opinion or promoting specific agendas.
Understanding the multifaceted impact of these botnets is crucial for developing effective countermeasures.
Potential Harm from Verified Fake Accounts
The ability of verified fake accounts to impersonate legitimate individuals or organizations allows for the dissemination of false information with a veneer of credibility. This manipulation of trust can have severe consequences, ranging from financial losses to the erosion of social capital. The perceived legitimacy of these accounts can amplify the impact of disinformation campaigns, making them more effective at influencing public opinion.
Social Implications of Botnet Activity
The manipulation of public discourse by botnets can have a detrimental impact on social cohesion. Coordinated campaigns designed to sow discord or amplify existing tensions can create an environment of distrust and polarization. The spread of misinformation and the deliberate targeting of specific groups can lead to social unrest and conflict. Real-world examples of coordinated campaigns have shown the potential for significant social disruption.
Economic Impact of Verified Fake Accounts Botnets
Verified fake accounts can be exploited for various malicious activities, impacting the economic sphere. Financial scams, stock manipulation, and the creation of artificial demand or supply are potential consequences. The spread of false information about companies or products can result in significant economic losses for legitimate businesses.
Political Implications and Misinformation
Botnets are increasingly used in political contexts to influence elections and manipulate public perception. The amplification of false narratives and the targeting of specific demographics can sway public opinion, potentially leading to outcomes that are not reflective of the true will of the people. The spread of misinformation during election cycles can severely damage democratic processes.
Real-World Examples of Malicious Activities
Numerous instances of coordinated campaigns using verified fake accounts and botnets have been documented. These include attempts to influence elections, spread false narratives about public figures, and incite violence or social unrest. The use of these networks for financial fraud and the manipulation of financial markets is also a significant concern.
Challenges in Detection and Mitigation
Identifying and mitigating these botnets presents significant challenges. The rapid evolution of these networks, their ability to adapt to detection strategies, and the sheer volume of accounts involved make it difficult to keep pace. Furthermore, the technical expertise required to analyze and dismantle these networks can be substantial.
Negative Consequences by Impact Area
| Impact Area | Specific Consequences |
|---|---|
| Social | Erosion of trust, polarization, social unrest, amplified existing tensions |
| Economic | Financial scams, stock manipulation, damage to legitimate businesses |
| Political | Influence on elections, spread of misinformation, damage to democratic processes |
| Information Integrity | Undermining trust in legitimate sources, spread of false information, manipulation of public discourse |
Research Methodology
Unmasking verified fake accounts and botnets requires a multi-faceted approach, combining diverse data sources and analytical techniques. This methodology must account for the sophisticated nature of these operations, often designed to evade detection. The goal is to identify patterns, quantify the scale, and ultimately, understand the underlying motivations and objectives.
Common Research Approaches
Research into verified fake accounts and botnets employs a variety of approaches, each with its own strengths and weaknesses. These methods often overlap, forming a comprehensive strategy for investigation. Techniques include network analysis, social network analysis, and content analysis. Network analysis helps visualize the relationships between accounts, while social network analysis reveals the structure and dynamics of interactions within the network.
Content analysis examines the characteristics of the content shared by these accounts, looking for patterns and anomalies.
Data Sources, Twitter verified fake accounts botnet researcher
Identifying and verifying the authenticity of accounts requires access to a wide array of data sources. Publicly available data from Twitter itself, such as account creation dates, follower counts, and tweet history, are crucial. Furthermore, external data sources, including third-party social media monitoring tools and databases of known botnets, can be invaluable. Open-source intelligence (OSINT) techniques can also uncover information about accounts and their connections.
Data from other social media platforms, especially those with similar verification systems, can offer comparative insights.
Data Collection and Analysis Techniques
Collecting data involves establishing clear criteria for identifying suspicious accounts. These criteria might include unusual account activity patterns, coordinated posting behavior, and the use of automated tools. Tools for scraping Twitter data and other social media platforms are often employed. Once data is collected, sophisticated analysis is needed. Statistical analysis, machine learning algorithms, and natural language processing techniques can help identify patterns and anomalies indicative of botnet activity.
Examples of analysis techniques include anomaly detection algorithms, clustering algorithms, and network centrality measures.
Challenges in Obtaining and Verifying Data
Obtaining and verifying data for this type of research presents significant challenges. Twitter’s API limitations and rate limits can restrict access to large datasets. Data privacy concerns and the need for ethical considerations must be addressed when collecting data from social media. Ensuring the accuracy and reliability of data is also crucial, as some sources may be unreliable or contain errors.
Furthermore, data collection methods must comply with Twitter’s terms of service and relevant data privacy regulations.
Determining Scale and Scope
Determining the scale and scope of verified fake account botnets requires a quantitative approach. Tracking the number of accounts involved, the frequency of interactions, and the geographic distribution of these accounts can reveal the extent of the problem. Monitoring the growth rate of suspicious accounts and identifying periods of heightened activity can offer valuable insights. Using network analysis, the size and structure of the network can be determined, providing insight into its potential impact.
Analyzing the geographic distribution of accounts involved can further highlight the global reach of the botnet. For example, a significant increase in suspicious accounts from a particular region or country might indicate a targeted campaign.
Analyzing Network Behavior and Account Interactions
Analyzing the network behavior and account interactions of these accounts is essential for identifying botnets. This involves studying the relationships between accounts, the frequency of interactions, and the patterns of content shared. For instance, identifying accounts with unusually high numbers of followers and very few or no interactions with other accounts can signal a potential botnet operation. Analyzing the similarity of content shared by different accounts can provide insights into the coordinated nature of their activities.
Twitter verified fake accounts and botnet researchers often use sophisticated methods to mimic real users. Understanding how these automated systems operate is crucial, especially when considering the legal implications of AI in the digital space. A recent development in this area, for example, is the work of Fugess Pras Michel, an AI lawyer specializing in legal issues surrounding AI, as detailed on fugess pras michel ai lawyer legal.
His expertise in this area highlights the growing importance of legal frameworks to combat the creation and use of fake accounts on platforms like Twitter.
Tools that track account interactions and network structures can assist in detecting patterns indicative of botnet activity. These analyses can identify coordinated posting times, common hashtags, and specific types of content that might suggest a coordinated campaign.
Detection and Mitigation Strategies: Twitter Verified Fake Accounts Botnet Researcher
Unmasking and neutralizing Twitter verified fake accounts botnets requires a multi-faceted approach, encompassing both platform-level interventions and advanced technical solutions. Effective detection and mitigation strategies are crucial for safeguarding the integrity of the platform and ensuring the authenticity of user accounts. This involves a careful balance between technical prowess and the social responsibility of platforms to maintain a trustworthy environment.This section delves into the practical aspects of detecting and mitigating these malicious networks.
We will examine various detection methods, analyze the role of social media platforms, explore technical solutions, and assess the limitations of current approaches. Finally, the importance of collaborative efforts between researchers and platforms will be highlighted.
Digging into the world of Twitter verified fake accounts and botnet researchers is fascinating. It’s a bit like studying the rare white giraffes, showcasing interesting genetic variations like leucism and albinism, which researchers study to understand evolutionary biology. The complexity of these Twitter manipulations mirrors the complex biological adaptations, reminding us of the lengths people go to in the digital world.
These botnet researchers are uncovering the patterns and vulnerabilities in these systems, much like zoologists study the behavior of animals.
Comparative Analysis of Detection Methods
Understanding the strengths and weaknesses of various detection methods is essential for crafting effective strategies. Different approaches target different aspects of botnet activity, leading to varying degrees of accuracy and efficiency.
| Detection Method | Description | Strengths | Weaknesses |
|---|---|---|---|
| Behavioral Analysis | Observing unusual patterns in account activity, such as posting frequency, follower/following ratios, and content similarity. | Can detect subtle anomalies indicative of botnet activity. | Requires significant data volume and sophisticated algorithms. Can be susceptible to false positives. |
| Network Analysis | Identifying connections between accounts, examining IP addresses, and analyzing communication patterns. | Effective in uncovering coordinated activity. | Requires access to network data and can be challenging to scale for large platforms. |
| Content Analysis | Evaluating the content posted by accounts, searching for s, and identifying common themes. | Can detect propaganda or coordinated disinformation campaigns. | Highly dependent on selection and prone to false positives from legitimate users. |
| Machine Learning | Employing algorithms to learn patterns and identify suspicious activity. | Adaptable to new threats and can handle high-volume data. | Requires large datasets for training and can be opaque, making it difficult to interpret results. |
Role of Social Media Platforms
Social media platforms play a pivotal role in combating these botnets. Proactive measures and transparent policies are critical to safeguarding the integrity of their platforms.
- Proactive Monitoring and Investigation: Continuous monitoring of account activity and proactive investigation of suspicious accounts are crucial. Real-time analysis of user data is essential for early detection and rapid response to botnet activity.
- Improved Account Verification Procedures: Strengthening account verification procedures and implementing robust verification processes is essential to mitigate the creation of fraudulent accounts. These procedures must be regularly updated and improved to keep pace with evolving botnet tactics.
- Collaboration with Researchers and Law Enforcement: Active collaboration with researchers and law enforcement agencies is essential to address this threat. Sharing intelligence and coordinating responses can enhance the effectiveness of mitigation efforts.
Technical Solutions and Approaches
Developing technical solutions is essential to address the ever-evolving sophistication of botnet activity.
- Advanced Machine Learning Models: Developing more sophisticated machine learning models can enhance the accuracy and efficiency of detection algorithms. These models should be able to identify subtle anomalies indicative of botnet activity in real-time.
- Network Traffic Filtering: Implementing filters that identify and block network traffic from known malicious IP addresses can be highly effective. This can help reduce the spread of botnet activity and isolate compromised accounts.
- Data Anonymization and Obfuscation: Anonymization and obfuscation of data can help protect sensitive information from being exploited by malicious actors. Protecting user data can mitigate the impact of botnet activity.
Examples of Existing Tools and Technologies
Several tools and technologies are already being used to detect and mitigate botnet activity on Twitter and other platforms.
- Third-party security tools: Many companies offer specialized tools for detecting and analyzing botnet activity. These tools often incorporate machine learning algorithms and advanced data analysis techniques.
- Platform-specific algorithms: Twitter and other platforms have their own internal algorithms designed to identify and flag suspicious accounts and activities.
Limitations of Existing Approaches and Future Research Directions
Current approaches face limitations, especially with the evolving nature of botnets. Further research is needed to address these shortcomings.
- Adaptability to Evolving Tactics: Botnets are constantly evolving, developing new techniques to evade detection. Ongoing research is needed to stay ahead of these developments.
- False Positive Rates: Detection systems can produce false positives, leading to legitimate accounts being flagged as malicious. Minimizing false positives while maintaining high detection rates is a key challenge.
- Data Privacy Concerns: Using data for detection purposes raises privacy concerns. Developing methods that balance detection with data privacy is a crucial aspect of future research.
Importance of Collaborative Efforts
Effective mitigation requires collaboration between researchers and social media platforms.
- Sharing Information and Expertise: Researchers can provide insights into botnet activity and best practices for detection. Platforms can share data and information about identified threats.
- Joint Development of Detection Tools: Collaboration can lead to the development of more effective detection tools and strategies.
Case Studies and Examples
Dissecting real-world instances of verified fake account botnets unveils the devastating impact they can have. These sophisticated networks, often hidden in plain sight, can be used to manipulate public opinion, spread misinformation, and even launch targeted attacks against individuals or organizations. Examining past events provides valuable insights into the tactics employed, the damage inflicted, and the strategies used to mitigate future threats.
Specific Instance of a Verified Fake Account Botnet
A significant case emerged in 2023 involving a botnet meticulously designed to impersonate verified journalists and influencers on Twitter. This operation was remarkable for its sophisticated nature and the sheer volume of accounts compromised. The botnet leveraged publicly available information about verified accounts to create convincing replicas, enabling the dissemination of coordinated campaigns.
Real-World Attacks Utilizing These Botnets
These botnets were deployed in several coordinated campaigns, including:
- Targeted Disinformation Campaigns: The botnet orchestrated a coordinated disinformation campaign against a political candidate, spreading false narratives and manipulating public opinion in a targeted manner.
- Financial Scams: Accounts were used to create fraudulent investment schemes, leading to significant financial losses for unsuspecting victims.
- Brand Damage: Verified accounts were used to generate negative publicity against companies, leading to brand damage and reputational harm.
Methods Used to Identify and Mitigate the Threat
Various methods were employed to detect and counter this threat:
- Analysis of Account Behavior: The botnet’s activity patterns, such as unusual tweeting frequency and follower/following ratios, were analyzed to identify anomalies.
- Network Analysis: Examination of the network connections and interactions between accounts helped identify the botnet’s structure and its origin.
- Content Analysis: The botnet’s content and message patterns were examined for consistency, inconsistencies, and any signs of coordinated behavior.
- Collaboration between Twitter and Security Experts: Collaboration between Twitter and security researchers helped identify the accounts and shut down the operation.
Case Study Table
| Date | Description | Impact | Mitigation Strategy |
|---|---|---|---|
| 2023 | A botnet impersonating verified journalists and influencers on Twitter spread coordinated disinformation campaigns, launched financial scams, and damaged brands. | Significant damage to reputation and financial loss for victims. Manipulation of public opinion. | Analysis of account behavior, network analysis, content analysis, and collaboration between Twitter and security experts. Twitter suspended/removed affected accounts. |
Future Trends and Predictions
The landscape of online manipulation is constantly evolving, and the threat of verified fake accounts botnets is no exception. As technology advances, so do the methods employed by malicious actors. Understanding these emerging trends is crucial for developing effective countermeasures and safeguarding online platforms from manipulation.
Potential Future Developments in Botnet Techniques
The sophistication of botnet techniques is likely to increase. We can anticipate the emergence of more sophisticated botnet architectures, capable of adapting to evolving security measures. This includes using more complex algorithms for account creation, behavior mimicry, and network communication. Furthermore, we can expect the use of AI and machine learning to enhance the effectiveness of botnets.
These advancements will enable them to generate more realistic profiles, adapt to dynamic security measures, and evade detection.
Anticipated Evolution of Verified Fake Account Botnets
Verified fake accounts botnets are expected to become more pervasive and integrated into legitimate social media and online platforms. The integration with legitimate services will make them harder to detect and isolate. They will be designed to operate as seamlessly as possible, leveraging existing infrastructure and user behavior patterns to maintain their invisibility. Moreover, their purpose will likely expand beyond simple harassment or misinformation, potentially including financial fraud, political manipulation, and the spread of malicious software.
These botnets will become more potent tools for malicious actors seeking to manipulate public opinion and spread propaganda.
Impact of Emerging Technologies on Detection and Mitigation
Emerging technologies, such as machine learning and AI, offer promising avenues for improving detection and mitigation strategies. These tools can be trained on large datasets of user behavior patterns and account characteristics to identify suspicious activities and potentially fraudulent accounts. However, this also presents a challenge, as malicious actors will likely use these same technologies to enhance their botnets’ capabilities, creating a constant arms race.
For example, advanced AI can generate incredibly realistic fake profiles and posts, making it difficult to distinguish them from genuine accounts. The key will be to develop AI-based countermeasures that can stay ahead of these evolving threats.
Potential for More Sophisticated Attacks
The potential for more sophisticated attacks is high. We can expect verified fake account botnets to become more interconnected and coordinated. This increased coordination will allow for larger-scale, more impactful campaigns of misinformation and manipulation. For instance, coordinated attacks on specific individuals or organizations could use fake accounts to spread malicious content or engage in targeted harassment.
They could even be used to influence election outcomes or undermine democratic processes.
Importance of Ongoing Research and Development
Continued research and development are essential to stay ahead of these evolving threats. This includes developing advanced detection algorithms, improving user awareness programs, and creating stronger regulations for online platforms. Researchers should focus on developing innovative methods for detecting subtle anomalies in user behavior and identifying patterns indicative of botnet activity.
Potential Future Threats and Mitigation Strategies
| Potential Future Threat | Mitigation Strategy ||—|—|| Advanced AI-powered account creation and behavior mimicking | Development of AI-based detection systems capable of identifying subtle deviations from normal user behavior. || Increased coordination and interconnectedness of botnets | Enhancing inter-platform information sharing and collaboration between social media companies to identify and isolate coordinated attacks. || Integration with legitimate services and infrastructure | Development of techniques for identifying and isolating accounts that exhibit anomalous behavior within the context of legitimate platforms.
|| Sophisticated attacks targeting specific individuals or organizations | Robust account verification processes and the implementation of advanced user authentication mechanisms. || Expansion of botnet purposes beyond misinformation | Continuous monitoring and analysis of botnet activity to identify emerging threats and adapt mitigation strategies. |
Conclusion
In conclusion, the study of Twitter verified fake accounts botnets highlights the ever-evolving threat landscape on social media platforms. The research emphasizes the importance of robust verification procedures, proactive detection methods, and collaborative efforts between researchers and platforms to combat these malicious activities. Understanding the methods and motivations behind these botnets is crucial for mitigating their impact and maintaining the integrity of online communities.