Threats hiding in NSX environment are a significant concern for network security. This deep dive explores the vulnerabilities within NSX, common misconfigurations, and attack vectors, revealing potential risks from third-party integrations and specific component weaknesses like Edge Services and Transport Zones. Real-world incidents are examined, along with a breakdown of how threats propagate, potentially impacting virtual machines and network segments.
We’ll also cover crucial mitigation strategies, threat modeling, and simulation techniques to strengthen NSX security posture.
The complexity of NSX environments often obscures potential security breaches. This exploration delves into practical methods for detecting anomalies, suspicious activities, and hidden threats within the NSX framework, providing insights into log analysis, real-time monitoring, and the setup of intrusion detection systems. Understanding threat propagation, analyzing the impact of compromised virtual machines, and comparing different security protocols are also key aspects of this analysis.
Identifying Potential Threats in NSX Environments
The NSX Data Center platform, while offering robust virtualization capabilities, presents unique security vulnerabilities if not properly configured and managed. Understanding these potential threats is crucial for organizations leveraging NSX to safeguard their infrastructure. Comprehensive security assessments, including vulnerability scans and penetration testing, are essential to proactively mitigate these risks.The complexity of NSX deployments, encompassing various components and integrations, necessitates a thorough understanding of potential attack vectors and misconfigurations.
This includes recognizing the specific risks associated with third-party integrations, different NSX components, and the potential impact of real-world security incidents. Addressing these threats requires a layered approach, encompassing proactive security measures, regular vulnerability assessments, and incident response plans.
Security Vulnerabilities Inherent in NSX Environments
NSX, like any complex networking platform, possesses inherent security vulnerabilities. These stem from the platform’s intricate architecture and the potential for misconfigurations in its various components. Careful attention to configuration details and regular security audits are vital to prevent exploitation.
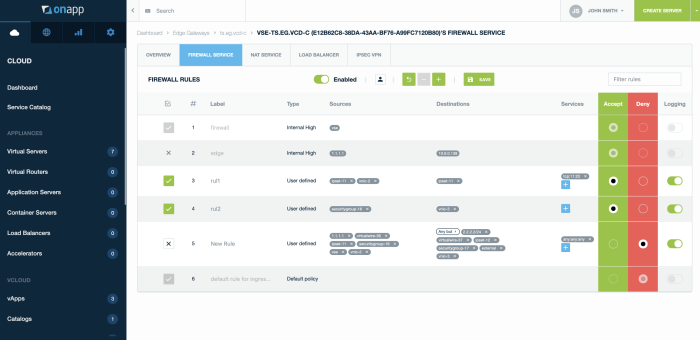
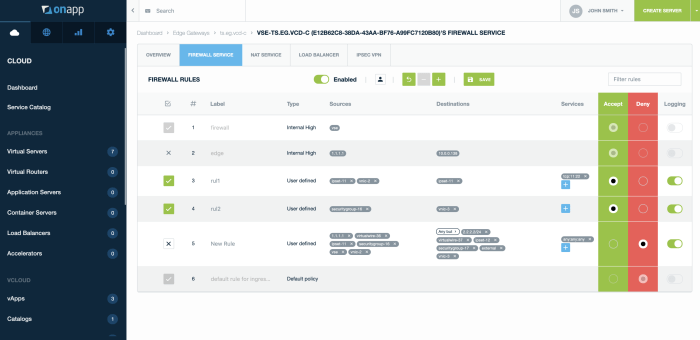
- Improperly configured security policies: Incorrectly defined access controls, firewall rules, and intrusion detection systems can expose the NSX platform to unauthorized access and malicious activity. This includes insufficient logging and monitoring, leading to a lack of visibility into potential threats.
- Weak authentication and authorization mechanisms: Failure to implement strong passwords, multi-factor authentication, or other robust authentication methods creates opportunities for unauthorized users to gain access to sensitive NSX data and functionalities.
- Vulnerabilities in third-party integrations: Third-party integrations with NSX can introduce vulnerabilities if not properly vetted and secured. These vulnerabilities can provide attackers with entry points into the NSX environment.
Common Misconfigurations that Could Expose the NSX Platform
Misconfigurations in NSX deployments can create significant security gaps. These misconfigurations often stem from insufficient understanding of the platform’s functionalities or lack of regular configuration reviews.
- Default configurations: Utilizing default NSX configurations without proper customization exposes the platform to known vulnerabilities. This can include default passwords, unsecured protocols, or overly permissive access rules.
- Lack of network segmentation: Insufficient network segmentation within the NSX environment can allow attackers to move laterally between different parts of the network, potentially compromising sensitive data and critical systems.
- Insufficient logging and monitoring: Inadequate logging and monitoring mechanisms make it difficult to detect and respond to security incidents. This lack of visibility hinders incident response and can prolong the duration of an attack.
Attack Vectors Exploitable within an NSX Infrastructure
Understanding the attack vectors targeting NSX is crucial for effective security measures. These vectors leverage various vulnerabilities and misconfigurations to compromise the platform.
- Exploiting vulnerabilities in NSX components: Attackers may exploit known vulnerabilities in NSX components such as the Edge Services or Transport Zones. These vulnerabilities can be exploited to gain unauthorized access or control.
- Man-in-the-middle attacks: Attackers might attempt to intercept communication between NSX components or between NSX and other network elements. This can lead to data breaches or unauthorized manipulation of network traffic.
- Denial-of-service attacks: Overwhelming the NSX platform with malicious traffic can disrupt its services and render it unusable for legitimate users.
Risks Associated with Using Third-Party Integrations with NSX
Third-party integrations with NSX can introduce new security risks if not carefully evaluated and managed. A lack of security considerations in third-party integrations can expose the entire NSX environment to potential threats.
- Security vulnerabilities in third-party software: Vulnerabilities in third-party software can be exploited to gain unauthorized access to the NSX environment.
- Lack of integration security policies: Third-party integrations might not adhere to the security policies established for the NSX environment, creating security gaps.
- Lack of visibility and control over integrations: Limited visibility into third-party integrations can hinder security monitoring and response efforts.
Vulnerabilities Specific to Different NSX Components
Different NSX components have varying security considerations. Understanding the specific vulnerabilities associated with each component is crucial for implementing targeted security measures.
| NSX Component | Associated Security Risks |
|---|---|
| Edge Services | Unauthorized access, misconfigurations in routing and firewall rules, and potential vulnerabilities in third-party integrations |
| Transport Zones | Compromised network segmentation, allowing lateral movement within the network, and default configuration vulnerabilities |
| Control Plane | Unauthorized access, denial-of-service attacks, and compromise of critical configuration data |
Examples of Real-World NSX Security Incidents and Their Causes
Real-world security incidents provide valuable lessons in understanding the potential risks associated with NSX deployments.
- Incidents involving misconfigured firewall rules: A security breach might stem from poorly configured firewall rules within NSX, allowing unauthorized traffic to traverse the network.
- Incidents due to vulnerabilities in third-party integrations: Exploiting vulnerabilities in third-party applications or tools integrated with NSX can compromise the entire infrastructure.
- Incidents caused by default configurations: Utilizing default NSX configurations without applying necessary security hardening can expose the platform to common vulnerabilities. This often leads to significant security breaches.
Assessing Threat Visibility
Understanding the hidden threats lurking within your NSX environment requires a proactive approach to threat visibility. Simply having NSX deployed isn’t enough; you need robust mechanisms to identify and respond to anomalies. This involves a multi-faceted strategy, encompassing real-time monitoring, log analysis, and the strategic implementation of intrusion detection systems. A clear understanding of threat visibility is crucial to prevent breaches and maintain the security posture of your network.Effective threat detection in NSX hinges on the ability to discern normal behavior from suspicious activities.
Security threats can lurk in unexpected places, even within a seemingly secure network like an NSX environment. For instance, a new handheld gaming device like the Ayaneo Next Lite, a potential Steam Deck competitor, ayaneo next lite steam deck competitor steamos , might introduce vulnerabilities if not properly configured. These potential security gaps in the NSX environment highlight the importance of regular security audits and proactive threat hunting.
This requires sophisticated monitoring tools capable of analyzing the massive amount of data generated by the NSX platform. Early detection of anomalous patterns and swift responses are paramount to mitigating potential damage.
Detecting Anomalies and Suspicious Activities
Identifying anomalies in NSX requires a combination of pattern recognition and established security best practices. Regularly monitoring network traffic patterns, analyzing flow characteristics, and scrutinizing access attempts are essential components of this process. Deep packet inspection, combined with machine learning algorithms, can detect unusual data transmissions or protocol violations that might indicate malicious activity.
Real-Time Monitoring and Alerting Systems
Real-time monitoring is vital for swift responses to threats. Monitoring tools that provide real-time alerts for unusual network activities, unauthorized access attempts, and suspicious traffic patterns are critical. This allows security teams to act immediately and contain potential threats before they escalate. These systems must be configurable to prioritize alerts based on severity, ensuring that critical issues are addressed first.
Log Analysis Techniques
Analyzing NSX logs is a critical component of threat detection. Tools should enable efficient searching and filtering of logs to pinpoint specific events. Correlation of events across multiple logs (e.g., firewall logs, network logs) is essential for identifying patterns indicative of malicious activity. Regularly reviewing logs for unusual activities and unusual user behavior can reveal subtle signs of intrusions.
Sophisticated log aggregation and analysis tools are essential for this process.
Identifying and Categorizing Potential Threats, Threats hiding in nsx environment
Threats should be categorized based on severity and potential impact. This allows for prioritized responses and appropriate resource allocation. A standardized categorization system is crucial to ensure consistency and efficiency in threat handling. This might include categorizations like high-severity threats (e.g., denial-of-service attacks), medium-severity threats (e.g., unauthorized access attempts), and low-severity threats (e.g., minor configuration errors).
Comparison of Monitoring Tools for NSX
| Tool | Features | Pros | Cons |
|---|---|---|---|
| NSX Manager | Built-in monitoring capabilities | Integrated with NSX, easy setup | Limited customization, potentially insufficient for advanced use cases |
| Splunk | Versatile log aggregation and analysis | Comprehensive analysis, high scalability | Steeper learning curve, higher cost |
| Elasticsearch, Logstash, Kibana (ELK Stack) | Open-source, flexible, and scalable | Cost-effective, high customization | Requires more technical expertise for setup and maintenance |
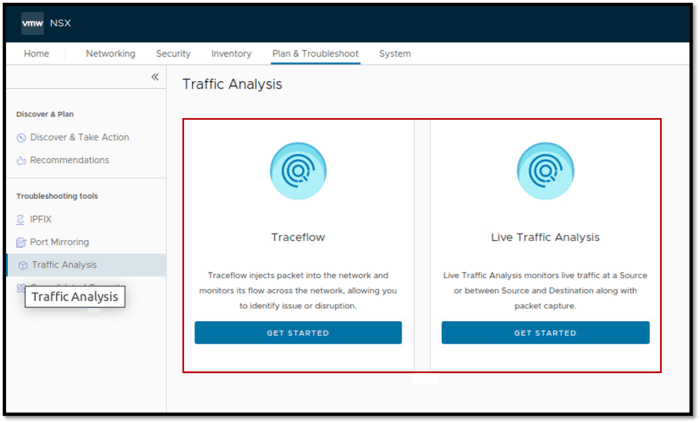
Setting Up Intrusion Detection and Prevention Systems (IDS/IPS)
Implementing IDS/IPS within the NSX framework requires careful configuration. These systems should be designed to detect and block malicious network traffic in real-time. Properly configured IDS/IPS can proactively prevent attacks by identifying and blocking malicious traffic before it reaches sensitive resources. Integration with existing security infrastructure is crucial for efficient threat management.
Understanding Threat Propagation
Navigating the intricate network pathways of NSX environments requires a keen understanding of how threats can propagate. A single compromised element can quickly escalate into a widespread security breach if not addressed effectively. This understanding is crucial for proactively mitigating risks and fortifying the overall network security posture.Threats in NSX environments, like in traditional networks, exploit vulnerabilities in various components to spread laterally.
This often involves exploiting weaknesses in virtual machines (VMs), network segments, or the NSX infrastructure itself. Comprehending the flow of traffic and potential entry points is critical for building robust security measures.
Threat Propagation within NSX
Understanding how threats spread within an NSX environment requires a detailed look at the traffic flow. Threats can leverage the interconnected nature of virtual networks and the various components of NSX to propagate rapidly. A compromised VM, for example, could potentially gain access to other VMs within the same segment, or even to VMs in different segments, through the virtual networking infrastructure.
Impact of Compromised Virtual Machines
A compromised VM within an NSX environment can have significant repercussions. A malicious actor gaining control of a VM can potentially leverage its resources to launch further attacks, such as scanning other VMs for vulnerabilities or exfiltrating sensitive data. The impact extends beyond the compromised VM, as the attack can spread to other connected VMs within the same segment or across different segments, depending on the access granted.
This can lead to a cascade of compromised systems, significantly impacting the overall network security posture.
Impact of Compromised Virtual Network Segments
A successful attack on a virtual network segment can have severe consequences. The attacker gains access to a group of VMs, allowing for lateral movement and potential access to sensitive data within the segment. This could involve data exfiltration, denial-of-service attacks, or even manipulation of the virtual network configuration, jeopardizing the functionality and integrity of the entire environment.
The specific impact depends on the criticality of the data and the nature of the compromised segment.
Security Protocols for Preventing Threat Propagation
Various security protocols can be implemented to mitigate the risk of threat propagation within NSX environments. These protocols include network segmentation, access control lists (ACLs), intrusion detection and prevention systems (IDS/IPS), and security information and event management (SIEM) systems.
- Network Segmentation: Isolating virtual networks into smaller, more manageable segments reduces the impact of a successful attack. This isolates compromised segments, preventing lateral movement. This is a fundamental approach to limiting the spread of a threat.
- Access Control Lists (ACLs): ACLs define which traffic is allowed or denied based on source, destination, and other criteria. Applying strict ACLs within the virtual network restricts unauthorized access and limits the potential for a threat to spread.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity, detecting and potentially preventing intrusions. IDS/IPS solutions provide early detection and mitigation capabilities to stop or slow the spread of threats.
- Security Information and Event Management (SIEM) Systems: These systems collect and analyze security logs from various sources to identify patterns and potential threats. They enable centralized monitoring and threat correlation across the NSX environment.
Flowchart of a Potential Threat
The following flowchart illustrates a potential path a threat might take within an NSX environment. It highlights the critical steps and components involved in the propagation of a threat.
+-----------------+ +-----------------+ +-----------------+
| Compromised VM | --> | Network Segment | --> | Other VMs in Seg|
+-----------------+ +-----------------+ +-----------------+
| |
|------------------------------------|
| |
| NSX Security Protocols (ACLs, IDS)|
| |
|------------------------------------|
| |
| Potential Spread to Other VMs |
| across different Segments |
+---------------------------------+
Mitigation Strategies: Threats Hiding In Nsx Environment
Identifying and understanding potential threats within an NSX environment is crucial, but effective mitigation strategies are equally important.
Security threats can lurk in unexpected places, even within an NSX environment. While exploring the intricacies of network security, I stumbled upon the need to know how long the Google Pixel 9 Pro Fold battery lasts. Finding out how long is the Google Pixel 9 Pro Fold battery life is a great example of how seemingly unrelated topics can have a surprising impact on our overall security approach.
Ultimately, understanding these potential vulnerabilities in NSX environments is crucial for effective protection.
Implementing robust security measures is vital to prevent exploitation and maintain the integrity of the network. This section details key strategies for mitigating identified threats, focusing on strong access controls, network segmentation, patching, API security, and incident response procedures.
Implementing strong security measures within the NSX environment is paramount to protect sensitive data and infrastructure from malicious actors. The goal is to create a layered defense that addresses various potential attack vectors, making the environment as resilient as possible.
Strong Access Controls and User Authentication
Robust access controls and user authentication are fundamental to securing any network, including NSX. Properly configured user roles and permissions prevent unauthorized access to critical resources. Implementing multi-factor authentication (MFA) adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access. Strong passwords and regular password rotations are equally important for protecting accounts.
Regular audits of user permissions and access logs are essential for identifying potential security breaches.
Network Segmentation and Isolation
Network segmentation and isolation are essential for containing threats within NSX. This strategy divides the network into smaller, isolated segments, limiting the impact of a security breach. Each segment should be carefully defined, based on the specific functions and resources it contains. This approach restricts the propagation of malicious code or attacks within the network. The implementation of firewalls and virtual network segments (VNS) is key to achieving this segmentation.
Security threats lurking within NSX environments are a serious concern, especially when considering geopolitical events like the recent Russia-Roscosmos-OneWeb Soyuz launch demands Ukraine invasion. These kinds of global tensions can inadvertently create new attack vectors, potentially impacting the very security protocols we’re trying to maintain within our NSX infrastructure. The vulnerabilities in these environments need careful monitoring and proactive mitigation strategies to prevent exploitation.
Patching and Updating NSX Components
Regular patching and updating of NSX components is critical to address vulnerabilities and security flaws. This involves staying current with the latest security updates from VMware. Failure to apply updates leaves the system vulnerable to known exploits. Maintaining a documented patch management process, including a schedule for applying updates, is essential. This will help ensure that the NSX environment is always running on the most secure versions of the software.
Best Practices for NSX Security Hardening
| Category | Best Practice |
|---|---|
| Access Control | Implement strict role-based access control (RBAC) and multi-factor authentication (MFA) for all NSX users. |
| Network Segmentation | Divide the NSX network into isolated segments based on business function and data sensitivity. |
| Security Monitoring | Implement robust logging and monitoring to detect and respond to suspicious activity. |
| Vulnerability Management | Regularly scan for vulnerabilities and apply necessary patches and updates to all NSX components. |
| API Security | Employ strong authentication and authorization mechanisms for all NSX APIs. |
| Incident Response | Develop and regularly test a comprehensive incident response plan for NSX. |
Securing NSX APIs and Configurations
Securing NSX APIs and configurations involves implementing strong authentication mechanisms for API access. Restricting access to specific API endpoints and configurations based on user roles is vital. Regularly reviewing and auditing API access logs helps to detect suspicious activity. Using secure configuration management tools and regularly reviewing NSX configurations for vulnerabilities is equally important.
Incident Response Procedure
Developing a comprehensive incident response procedure for the NSX environment is essential. This should include clear roles and responsibilities for handling security incidents. The procedure should Artikel steps for detecting, containing, and recovering from a security breach. This procedure should also involve the communication and coordination between relevant teams, such as network operations, security teams, and management.
Regularly testing the incident response plan is critical for verifying its effectiveness.
Threat Modeling and Simulation
Understanding the potential threats within your NSX environment is crucial for proactive security. Threat modeling and simulation are essential components of this process, enabling you to identify vulnerabilities, assess your security posture, and refine your security controls. This approach allows you to predict and prepare for potential attacks, ensuring the resilience of your network infrastructure.
Threat modeling, in the context of NSX, involves identifying potential attack vectors, analyzing the impact of successful exploits, and outlining defensive strategies. This detailed approach empowers you to effectively mitigate risks and build a robust security framework. Simulating attacks within a controlled environment allows you to evaluate the effectiveness of security controls and fine-tune your defenses before a real-world incident occurs.
Creating a Threat Model for NSX
A comprehensive threat model for NSX begins with a thorough inventory of all components, including virtual machines, network segments, and security policies. This inventory should also include dependencies and interconnections within the environment. Identifying potential attack vectors, such as unauthorized access, misconfigurations, and vulnerabilities in third-party integrations, is paramount. The model should document potential threats, the likelihood of occurrence, and the potential impact on the network.
Finally, the model should include mitigation strategies and incident response plans.
Examples of Simulated Attacks
Simulating attacks against NSX should encompass various scenarios. Examples include:
- Denial-of-Service (DoS) attacks: Simulate flooding network segments with excessive traffic to disrupt service availability. This tests the resilience of the NSX firewall and load balancing mechanisms.
- Man-in-the-Middle (MitM) attacks: Simulate an attacker intercepting communication between virtual machines. This tests the effectiveness of encryption and network segmentation policies implemented within NSX.
- Unauthorized access attempts: Simulate attempts to gain unauthorized access to virtual machines or network resources. This evaluates the strength of authentication mechanisms and access control policies enforced by NSX.
- Vulnerability exploitation: Simulate exploits targeting known vulnerabilities in NSX components or guest operating systems. This exercise tests the effectiveness of patching and security updates within your environment.
Evaluating Security Control Effectiveness
Evaluating the effectiveness of security controls requires careful monitoring and analysis during simulated attacks. Metrics like latency, packet loss, and system response time can be measured to gauge the impact of simulated attacks. Detailed logs from NSX and other security tools should be reviewed to identify any security breaches or vulnerabilities. Regular audits and penetration tests are crucial to identify vulnerabilities and assess the effectiveness of your security controls.
Developing a Comprehensive Security Testing Strategy for NSX
Developing a comprehensive security testing strategy requires a phased approach. The initial phase involves defining specific objectives and scope for testing. The second phase involves choosing appropriate tools and methodologies for testing, including penetration testing tools and NSX’s built-in security features. The final phase involves analyzing the results, documenting findings, and implementing remediation steps.
Threat Simulation Scenarios for NSX
| Scenario | Description | Potential Impact |
|---|---|---|
| DoS Attack on Management Plane | Overwhelm the NSX Manager with traffic | Service disruption, management plane unavailability |
| Exploiting a Vulnerability in a Guest VM | Target known vulnerabilities in virtual machines | Data breaches, unauthorized access |
| Egress Filtering Bypass | Attempt to bypass egress filtering rules | Unauthorized data exfiltration |
| Insider Threat Simulation | Emulate malicious actions by a privileged user | Data breaches, system compromise |
Flowchart for Simulating a Threat
(Start) –> [Define Threat Model] –> [Select Attack Vector] –> [Configure Simulation Environment] –> [Initiate Simulation] –> [Monitor and Analyze Results] –> [Document Findings] –> [Implement Remediation Steps] –> (End)
The flowchart illustrates the sequential steps involved in simulating a threat in an NSX environment.
Ending Remarks
In conclusion, threats hiding in NSX environments demand proactive security measures. By identifying vulnerabilities, assessing visibility, understanding propagation, implementing mitigation strategies, and utilizing threat modeling and simulation, organizations can significantly improve their NSX security posture. This comprehensive guide provides actionable insights for bolstering network defenses and safeguarding against potential attacks within the NSX infrastructure. The exploration of potential risks and suggested mitigation strategies underscores the critical need for robust security protocols within NSX deployments.