T mobile spam calls call authentication fcc – T-Mobile spam calls call authentication fcc is a critical issue plaguing many customers. These unwanted calls, ranging from telemarketing pitches to fraudulent schemes, often cause financial distress, emotional upset, and a general waste of time. This article delves into the problem, exploring FCC regulations, available authentication methods, and consumer protection measures to help understand the complexities and find solutions.
We’ll examine T-Mobile’s role in addressing the issue and what you can do to combat these persistent calls.
The increasing frequency and sophistication of spam calls targeting T-Mobile customers highlight a growing need for robust call authentication. This article provides an overview of the problem, examining the types of spam calls, the FCC regulations that govern them, and the authentication methods that can help distinguish legitimate calls from fraudulent ones. We will also explore customer protection measures, future trends, and T-Mobile’s support channels.
T-Mobile Spam Call Problem Overview
T-Mobile, like many other major carriers, faces a persistent problem with spam calls targeting its customers. These calls, often automated and disruptive, can cause significant frustration and financial harm. Understanding the nature and impact of these calls is crucial for both customers and the company to address the issue effectively.The issue of spam calls is multifaceted, encompassing various tactics and types of calls.
From seemingly legitimate solicitations to outright scams, the methods employed by spam callers are constantly evolving, making it difficult for individuals and companies to stay ahead of the curve. This article delves into the problem’s core elements, detailing the different types of calls, tactics used, and the significant impact on T-Mobile users.
Types of Spam Calls Targeting T-Mobile Customers, T mobile spam calls call authentication fcc
Spam calls targeting T-Mobile customers are diverse, ranging from robocalls to more sophisticated scams. These calls often aim to defraud, solicit payments, or gain access to personal information.
- Robocalls: These automated calls are frequently used to deliver unwanted advertising, solicitations for products or services, or to initiate fraudulent schemes. They can be intrusive and time-consuming for the recipient, disrupting daily life.
- Pretexting Calls: These calls often involve a caller posing as a representative from a legitimate company, such as a bank or utility company, to gain access to personal information. The caller attempts to create a sense of urgency or authority to manipulate the recipient into revealing sensitive details.
- Fake Surveys or Polls: Often, these calls attempt to gather personal information through seemingly innocuous surveys. The data collected can be used for targeted phishing attacks or identity theft.
- Debt Collection Scams: These calls falsely claim to be debt collection agencies, demanding immediate payment for non-existent debts. They exploit the fear of legal action to coerce individuals into making payments to fraudulent accounts.
Common Tactics Used by Spam Callers
Spam callers employ various tactics to target T-Mobile users. These tactics often exploit the recipient’s vulnerabilities and lack of awareness about common scams.
- Caller ID Spoofing: Callers often use techniques to mask their true identity, making it difficult to identify the source of the call. This tactic makes it harder for recipients to recognize and avoid fraudulent calls.
- Sense of Urgency: Spam callers frequently create a sense of urgency, demanding immediate action or threatening negative consequences. This tactic exploits the recipient’s fear of missing out or facing negative repercussions.
- Social Engineering: Spam callers use psychological manipulation to gain access to personal information. They use techniques like posing as a trusted source or exploiting existing relationships to elicit sensitive details from their victims.
Negative Impacts on T-Mobile Customers
Spam calls can significantly affect T-Mobile customers in various ways. These impacts range from financial losses and wasted time to emotional distress and a general sense of vulnerability.
- Financial Losses: Scams often lead to financial losses for victims. From fraudulent charges to unknowingly paying off non-existent debts, these calls can result in significant financial harm.
- Emotional Distress: The constant barrage of unwanted calls can be emotionally draining. The pressure and anxiety caused by these calls can contribute to stress and mental health concerns.
- Wasted Time: The time spent dealing with spam calls, whether it’s trying to identify the caller, contacting the relevant authorities, or simply ignoring the calls, can be substantial.
Frequency and Types of Spam Calls by Demographic
The frequency and types of spam calls received can vary based on several demographics. This table provides a general overview of potential differences.
| Demographic | Spam Call Type | Frequency |
|---|---|---|
| Young Adults (18-25) | Debt Collection Scams, Fake Surveys | High |
| Middle-Aged Adults (35-55) | Pretexting Calls, Investment Scams | Medium |
| Senior Citizens (65+) | Pretexting Calls, Tech Support Scams | High |
| Low-Income Households | Debt Collection Scams, Loan Scams | High |
FCC Regulations and T-Mobile’s Compliance
T-Mobile, like other telecommunication companies, faces the challenge of managing unwanted robocalls and spam. The Federal Communications Commission (FCC) plays a crucial role in regulating these calls, setting standards and enforcing compliance. This section delves into the FCC’s regulations, T-Mobile’s stated policies, and a comparison of their efforts.T-Mobile’s commitment to reducing spam calls aligns with the FCC’s overarching goal of creating a cleaner, safer telecommunications environment.
This involves implementing technologies and procedures to identify and block unwanted calls, ensuring consumers are not subjected to harassing or misleading communications. The effectiveness of these measures is continuously evaluated and adapted to address emerging threats and challenges.
Ugh, those T-Mobile spam calls are driving me crazy! The FCC is finally cracking down on call authentication, but I’m still getting bombarded. It’s getting so frustrating, especially when you want to personalize your phone and move apps to your SD card like you can on a Galaxy Note 8. How to move apps to your SD card on a Galaxy Note 8 is a great solution to free up space and organize your phone.
Hopefully, with the FCC’s new authentication measures, the spam calls will eventually lessen, but until then, I’ll be searching for new ways to improve my phone’s performance.
FCC Regulations Concerning Telemarketing and Robocalls
The FCC has established regulations to combat telemarketing fraud and robocalls. These regulations aim to protect consumers from unwanted and potentially harmful calls. The primary goal is to promote fair and honest practices in telemarketing, minimizing the disruption and distress caused by unsolicited calls. Key areas of regulation include caller identification, disclosure requirements, and restrictions on certain types of calls, such as those made at inconvenient times.
T-Mobile’s Stated Policies and Procedures for Handling Spam Calls
T-Mobile has Artikeld specific policies and procedures to handle spam calls. These policies generally involve identifying and blocking calls that violate their guidelines. Their procedures often include using advanced call filtering technologies and collaborating with industry partners to enhance call authentication and spam detection mechanisms. T-Mobile actively works to update and refine its strategies based on evolving threats and technological advancements.
Comparison of T-Mobile’s Efforts to Combat Spam Calls with FCC Regulations
T-Mobile’s efforts to curb spam calls are assessed against the FCC’s regulations. T-Mobile’s policies, like their use of call filtering, often align with the FCC’s guidelines regarding caller identification and disclosure. Both aim to improve transparency and reduce the incidence of fraudulent or harassing calls. The effectiveness of T-Mobile’s measures in meeting the FCC’s standards is regularly reviewed and improved upon as necessary.
Specific FCC Regulations Related to Robocalls and T-Mobile’s Compliance
This table Artikels key FCC regulations regarding robocalls and how T-Mobile’s practices are intended to address them. Compliance with these regulations is vital to maintaining a clean and secure telecommunications environment.
| FCC Regulation | T-Mobile Compliance |
|---|---|
| Caller ID Accuracy and Transparency | T-Mobile employs technologies to ensure accurate caller ID display, minimizing instances of spoofing or inaccurate identification. |
| Restrictions on Robocalls at Inconvenient Times | T-Mobile utilizes advanced filtering techniques to detect and block robocalls placed during inconvenient hours, adhering to the FCC’s restrictions. |
| Disclosure Requirements for Telemarketing Calls | T-Mobile’s policies mandate the disclosure of the caller’s identity and purpose of the call, ensuring compliance with FCC requirements for telemarketing communications. |
| Prohibition of Unsolicited, Harassing, or Fraudulent Calls | T-Mobile actively works to identify and block calls that violate its policies and the FCC’s regulations, aiming to prevent unwanted and harmful calls. |
Call Authentication Methods: T Mobile Spam Calls Call Authentication Fcc
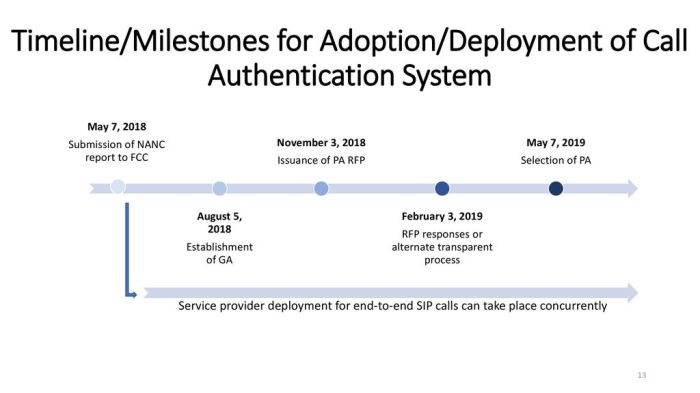
Spam calls are a persistent nuisance, and their prevalence highlights the need for robust call authentication methods. These methods, when effectively implemented, can significantly reduce the volume of unwanted calls, safeguarding both consumers and businesses. Call authentication is the process of verifying the identity of the caller to ensure that the call is legitimate. Different methods have varying degrees of effectiveness, and the best approach often depends on the specific context and resources available.Various technologies and strategies are employed to authenticate calls, ranging from simple caller ID checks to more complex verification systems.
Understanding how these methods work and their potential limitations is key to evaluating their overall impact on reducing spam. These methods are crucial in the fight against the deluge of unwanted calls, ultimately leading to a more secure and reliable communication environment.
Current Call Authentication Methods
A variety of methods are currently in use for call authentication, each with its own strengths and weaknesses. These methods vary in complexity and cost, influencing their widespread adoption. A crucial factor is their effectiveness in differentiating between legitimate and fraudulent calls.
Methods and Effectiveness
- Caller ID Verification: This is a basic method that checks the caller’s phone number against a database of known legitimate numbers. Effectiveness is limited; many spam calls use spoofed caller IDs, making this method alone insufficient for robust authentication. While it’s a simple initial filter, its effectiveness is often low, as spammers frequently use stolen or generated caller IDs to mask their identities.
- Number Portability and Historical Data: Tracking historical number usage and portability patterns can help identify potentially fraudulent calls. This method is particularly effective in conjunction with other authentication strategies, as it adds a layer of context to caller ID verification. By analyzing the history of a phone number, potential patterns of suspicious activity can be detected, thereby raising a red flag for potential spam.
- Voice Biometrics: Using voice recognition technology to verify the caller’s voice against a registered profile can provide a higher degree of authentication accuracy. This method can be effective in preventing spoofing and verifying the caller’s identity, but it requires users to register their voice profiles, potentially adding a step for wider adoption. It is more reliable than simply checking caller IDs, as it verifies the voice of the caller, not just the number.
- Reverse Phone Lookup Services: These services use databases to match phone numbers to known spammers, helping identify potentially fraudulent calls. This method is effective in identifying known spam numbers but is less effective in identifying new or unregistered spammers.
- Call Center Verification: By verifying the caller’s identity through an interaction with a live agent at a call center, this method provides the highest level of authentication. This method, while effective, is resource-intensive, and often impractical for widespread use. It typically requires human intervention, making it costly and potentially slower in handling a large volume of calls. However, it is the most secure way to verify the identity of a caller.
Potential of Call Authentication Methods
Call authentication methods hold significant potential for reducing spam calls. By implementing a multi-layered approach that combines different methods, service providers can significantly decrease the volume of unwanted calls reaching consumers. The effectiveness of these methods depends heavily on the level of cooperation and investment in technology from telecom providers, call centers, and potentially even individuals. This combined effort can significantly impact the spam call problem, enhancing user experience and security.
Consumer Protection Measures
Spam calls, a persistent nuisance, can be frustrating and even harmful. Understanding how to protect yourself is crucial in navigating this modern annoyance. This section details actionable steps consumers can take to safeguard themselves from these unwanted calls.Protecting yourself from spam calls requires a multi-faceted approach. Consumers need to be proactive in identifying and avoiding these calls, as well as reporting them effectively.
Effective reporting mechanisms and the utilization of available tools are key to minimizing the impact of spam.
Caller ID and Other Consumer Protection Tools
Caller ID, a ubiquitous feature on modern phones, serves as a vital first line of defense against spam calls. By displaying the caller’s number, Caller ID helps users assess the legitimacy of a call. Many phone services now provide enhanced Caller ID features, identifying numbers associated with high spam rates or known telemarketing campaigns.
Practical Steps to Avoid Spam Calls
Several practical steps can significantly reduce the likelihood of receiving spam calls. Avoid answering unknown numbers, particularly those with unfamiliar or unusual area codes. Be wary of calls promising free gifts or services. Critically evaluate the legitimacy of any call requesting personal information, especially financial details.
Reporting Spam Calls to T-Mobile and the FCC
Reporting spam calls is crucial for combating the issue. T-Mobile provides avenues for reporting these calls, enabling them to identify and address spammer patterns. The FCC also offers channels for reporting spam calls, collecting data to understand the prevalence and nature of these calls.
- T-Mobile Reporting: T-Mobile often has a dedicated spam call reporting feature within its customer portal or app. Consult T-Mobile’s support documentation or contact customer service for specific instructions. The steps usually involve providing details about the call, such as the number, time, and nature of the call.
- FCC Reporting: The FCC maintains an online portal for reporting spam calls. This allows users to file complaints, helping the FCC track and address these calls. Details such as the number, time, and type of call are often requested.
Effectiveness of Consumer Protection Measures
The effectiveness of consumer protection measures varies. While Caller ID and other tools can significantly reduce the number of spam calls received, they don’t eliminate the problem entirely. Reporting mechanisms, when used consistently, can help T-Mobile and the FCC identify patterns and potentially block or filter future spam calls. This approach can improve the overall effectiveness of consumer protection strategies.
| Consumer Protection Measure | Effectiveness | Explanation |
|---|---|---|
| Caller ID | High | Caller ID helps identify potentially spam calls. |
| Avoiding unknown numbers | Moderate | Reduces the chance of answering spam calls. |
| Reporting spam calls | Moderate | Helps T-Mobile and FCC identify and block spam calls. |
Future Trends and Technological Solutions
The fight against spam calls is an ongoing battle, requiring constant innovation and adaptation. Future trends will likely center around more sophisticated authentication methods and proactive detection techniques. These advancements are crucial to protect consumers from increasingly sophisticated robocallers and ensure the continued integrity of the telecommunications network.
Potential Future Trends in Call Authentication
Advanced call authentication methods will play a crucial role in preventing spam calls. Expect a shift towards a more decentralized and secure approach to verifying caller identity. This will involve the integration of multiple authentication factors beyond traditional phone numbers.
T-Mobile’s spam calls are a real pain, and the FCC’s call authentication efforts are definitely needed. While I’m researching that, I stumbled upon some killer deals on tech gadgets like Samsung Galaxy Buds, Fujifilm Instax Link, Roku Stick, and Catan, plus some Anker deals. Checking out those awesome sales at this link might distract me from the spam calls, but I’ll get back to that pesky T-Mobile issue soon enough.
Emerging Technologies for Enhanced Call Authentication
Several emerging technologies hold the potential to significantly enhance call authentication. One such technology is the widespread adoption of blockchain-based solutions for call verification. These systems can provide immutable records of caller identity, making it extremely difficult for fraudsters to impersonate legitimate numbers. Additionally, advancements in machine learning algorithms can analyze vast amounts of call data to identify patterns indicative of spam calls, enabling more precise detection.
Impact on T-Mobile’s Approach to Spam Call Prevention
T-Mobile can leverage these advancements to refine its existing spam call prevention strategies. By integrating blockchain-based call verification, T-Mobile can build a more resilient system against fraudulent calls, potentially creating a new standard for the industry. Furthermore, machine learning algorithms can be used to analyze call patterns and identify anomalies, enabling more proactive detection of spam calls. This would allow T-Mobile to implement more efficient spam call filtering systems, providing better protection for its customers.
Innovative Approaches to Spam Call Detection and Prevention
Innovative approaches to spam call detection and prevention are constantly emerging. One approach is the development of AI-powered caller identification tools that can analyze voice patterns, speech recognition, and call characteristics to detect potential spam calls. This level of analysis goes beyond simply checking the caller ID, offering a deeper level of security. Another innovative approach involves leveraging social media and online forums to identify spam call campaigns.
T-Mobile’s spam call problem is getting a lot of attention, and the FCC is looking into call authentication. Meanwhile, it’s interesting to see how Microsoft is handling app support for Windows on ARM64-bit systems. This innovative approach to compatibility might offer some insights into new security protocols that could be applied to the issue of spam calls.
Hopefully, a combination of technical solutions and regulatory action will eventually help curb the annoying spam calls.
By monitoring online chatter, T-Mobile could proactively identify new and emerging spam call trends.
Examples of Innovative Spam Call Prevention Techniques
Numerous examples demonstrate the efficacy of innovative spam call prevention techniques. For instance, companies are now using advanced audio analysis to distinguish between human voices and automated systems. This helps identify and filter out robocalls more effectively. Another example involves leveraging caller reputation databases, combining historical call data and user reports to identify potentially fraudulent numbers. This approach creates a dynamic, continuously updating system to identify and block spam calls.
How Blockchain Technology Could Revolutionize Call Verification
Blockchain technology offers a unique opportunity to create a tamper-proof and secure system for call verification. By recording each call’s origin and authentication details on a decentralized ledger, the risk of fraud is significantly reduced. This eliminates the possibility of fraudulent modifications to call records, enhancing transparency and trust.
T-Mobile’s Customer Support

T-Mobile, like many other major telecommunication providers, recognizes the growing problem of spam calls and is committed to helping customers. A robust customer support system is crucial in addressing this issue effectively. This section delves into T-Mobile’s support channels for reporting spam calls, the complaint process, and the overall effectiveness of their approach.T-Mobile understands that spam calls can be incredibly frustrating and disruptive.
Providing clear and efficient support channels is vital for customers to feel heard and supported in their efforts to combat this growing problem.
T-Mobile Support Channels for Spam Call Reporting
T-Mobile offers several avenues for customers to report spam calls. These channels aim to streamline the process and provide various options for different customer preferences.
- Online Portal:
- T-Mobile’s website features a dedicated online portal for reporting spam calls. This portal allows customers to submit detailed information about the calls, including the caller’s number, timestamps, and any other relevant details. This method allows for comprehensive record-keeping and easy access to the information for investigation.
- Customer Service Phone Line:
- Customers can report spam calls through T-Mobile’s dedicated customer service phone line. This option allows for immediate interaction with a representative, facilitating a more personalized and direct resolution. Representatives can address immediate concerns and provide tailored support.
- Mobile App:
- A dedicated mobile app might be available for reporting spam calls. This provides a convenient way for customers to report calls on the go, offering flexibility and ease of access.
Process for Filing a Complaint with T-Mobile
The process for filing a complaint with T-Mobile regarding spam calls is designed to be as straightforward as possible.
- Identify the Caller Information:
- Gather all available information about the spam call, including the caller’s phone number, the date and time of the call, and any specific details from the call (e.g., messages or prompts).
- Utilize Reporting Channels:
- Choose a suitable reporting channel from the options Artikeld above (website portal, phone line, or app). Each channel provides a dedicated form or process for submitting the complaint.
- Provide Necessary Details:
- Complete the necessary fields with accurate and detailed information about the call. This step is crucial for T-Mobile to effectively investigate and address the complaint.
- Follow Up (If Necessary):
- T-Mobile may follow up with the customer to gather additional information or clarify any points. This step ensures accuracy and efficiency in addressing the complaint.
Effectiveness of T-Mobile’s Customer Support
The effectiveness of T-Mobile’s customer support in addressing spam call issues is a multifaceted aspect. While T-Mobile strives to provide efficient support, the success depends on several factors, including the completeness of reported information, the promptness of resolution, and the long-term impact of implemented measures.
Flow Chart of Reporting a Spam Call to T-Mobile
The following flowchart illustrates the general process for reporting a spam call to T-Mobile. This visual representation simplifies the steps involved in the process.“`[Start] –> [Gather Caller Information] –> [Select Reporting Channel] –> [Complete Complaint Form] –> [Submit Report] –> [T-Mobile Investigation] –> [Resolution (if applicable)] –> [End]“`
Ending Remarks
In conclusion, the issue of spam calls targeting T-Mobile customers requires a multifaceted approach. While T-Mobile and the FCC strive to combat these calls, consumers must also take proactive steps to protect themselves. The various authentication methods, combined with informed consumer choices and diligent reporting, offer a path toward mitigating the negative impacts of spam calls. By understanding the problem, the regulations, and the available tools, we can work together to create a more secure and reliable telecommunications environment.






