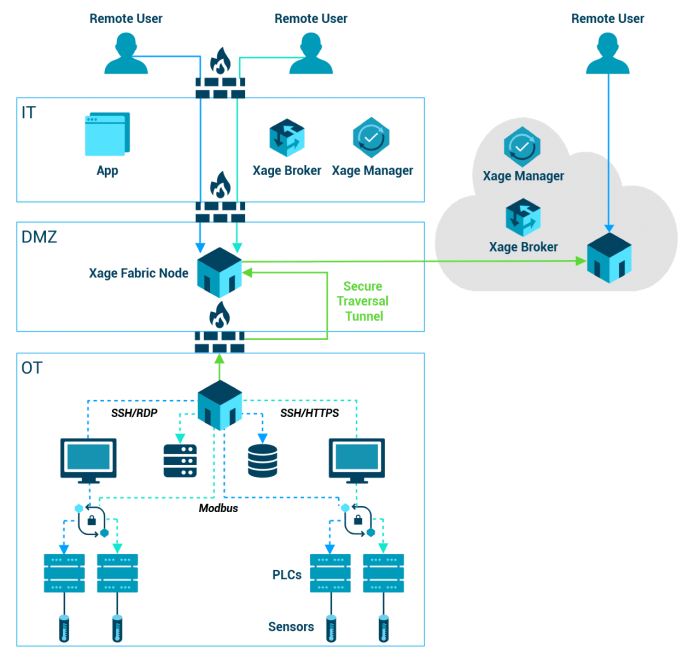
Secure remote workforces with zero trust network access is crucial in today’s digital landscape. It’s not just about securing individual devices; it’s about establishing a comprehensive security strategy that extends to the entire network, protecting sensitive data and resources while enabling flexible work arrangements. This approach addresses the unique challenges of remote work by employing a zero-trust model, verifying every user and device before granting access to resources.
This approach requires a robust understanding of various security considerations and implementation strategies, as well as careful monitoring and management.
This comprehensive guide explores the intricacies of secure remote workforces, delving into the core principles of zero trust network access (ZTNA). We’ll examine the benefits, challenges, and implementation steps required to build a secure and productive remote work environment. We’ll also analyze different ZTNA architectures, security considerations, access control, network segmentation, monitoring, and emerging trends in this ever-evolving field.
Secure Remote Workforces
Remote work has become the new normal, offering flexibility and efficiency. However, securing these remote workforces requires a robust strategy to protect sensitive data and maintain business continuity. A secure remote workforce goes beyond simply allowing employees to work from home; it prioritizes security and trust.
Definition of Secure Remote Workforces
A secure remote workforce is one where employees can work remotely while maintaining the same level of security as if they were working in a traditional office environment. This includes implementing strong security measures, such as robust authentication, data encryption, and access controls, to protect sensitive information. The concept extends to ensuring compliance with relevant regulations and industry best practices, thus minimizing the risk of breaches.
Key Benefits of Secure Remote Workforces
Secure remote workforces offer several advantages. They provide increased flexibility and work-life balance for employees, which can improve morale and productivity. They also allow businesses to tap into a wider talent pool, reducing geographical limitations and attracting top-tier professionals. Further, businesses can potentially lower overhead costs associated with traditional office spaces.
Challenges of Securing Remote Workforces
Securing remote workforces presents unique challenges. One major challenge is the dispersed nature of the workforce, making it harder to monitor and control access to sensitive data. Another challenge is the diverse range of devices and networks used by remote employees, potentially creating vulnerabilities. Furthermore, the need for strong remote access controls and security policies must be established to mitigate these risks.
Securing remote workforces with zero trust network access is crucial, especially in today’s dynamic environment. The US Army’s massive investment in Microsoft HoloLens headsets, a $21.88 billion deal, demonstrates a shift towards advanced tech solutions for enhanced security and operational efficiency. This massive deployment of augmented reality technology highlights the growing importance of robust cybersecurity measures for remote teams, echoing the need for zero trust network access strategies across various sectors.
Importance of Zero Trust Network Access (ZTNA) in Securing Remote Workforces
Zero Trust Network Access (ZTNA) is crucial for securing remote workforces. ZTNA operates on the principle of “never trust, always verify,” which means that every user and device requesting access to the network must be authenticated and authorized. This approach significantly reduces the attack surface by limiting access to only the resources a user needs. ZTNA effectively isolates sensitive data and applications, preventing unauthorized access even if an attacker compromises a single device or network segment.
By applying this principle, ZTNA offers a layer of security that traditional network security approaches lack. For example, a company implementing ZTNA will only allow employees to access specific applications and data relevant to their job function, thereby limiting the damage potential in the event of a security breach. ZTNA enforces granular access controls, limiting the damage caused by a potential compromise.
Understanding Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) is a paradigm shift in network security, moving away from the traditional “trust but verify” approach to a “never trust, always verify” model. It recognizes that the perimeter of a network is no longer a physical boundary, but rather a constantly evolving digital landscape where threats can originate from anywhere. ZTNA is crucial for organizations that want to protect their sensitive data and systems in this new era of remote and hybrid workforces.ZTNA relies on strong authentication, granular access controls, and continuous monitoring to ensure that only authorized users and devices can access specific resources.
This approach is not about trusting users, but about controlling the access paths and limiting the potential damage from a breach. It allows organizations to securely enable remote access while drastically reducing the attack surface.
Core Principles of ZTNA
ZTNA is built upon four fundamental principles:
- Least Privilege Access: Users are granted only the necessary access to resources. This principle minimizes the potential impact of a security breach.
- Continuous Verification: ZTNA continuously validates the identity and authorization of users and devices, ensuring that only authenticated and authorized entities can access resources.
- Micro-segmentation: Network resources are segmented into smaller, isolated units. This limits the impact of a compromise to a specific segment, preventing lateral movement.
- Zero Trust Posture: ZTNA assumes no inherent trust in any user, device, or network location. All access attempts are subject to strict authentication and authorization checks.
ZTNA vs. Traditional Network Security Models
Traditional network security models often rely on a perimeter-based approach. They treat the network perimeter as a secure boundary, trusting users and devices inside the perimeter. This model becomes increasingly vulnerable in a remote work environment where the perimeter is blurred and the attack surface expands. ZTNA, in contrast, operates on the principle that no user, device, or network location should be implicitly trusted.
| Feature | Traditional Network Security | ZTNA |
|---|---|---|
| Trust Model | Trust but verify | Never trust, always verify |
| Perimeter | Physical network boundary | Dynamic and evolving digital landscape |
| Access Control | Broad-based, often based on IP address | Granular, based on user and device identity |
| Security Depth | Typically layered but can be less comprehensive | Comprehensive, with constant verification |
ZTNA Architectures
ZTNA architectures vary depending on the specific needs and implementation strategies of an organization. However, they typically leverage cloud-based platforms and services to facilitate remote access. Some common architectures include:
- Cloud-based ZTNA: Security is handled in the cloud, with resources accessed through secure gateways. This architecture is often scalable and flexible, allowing for easy updates and modifications.
- On-premises ZTNA: Security infrastructure remains on-site, providing a degree of control over the security implementation. This approach can be more suitable for organizations with stringent compliance requirements.
- Hybrid ZTNA: This approach combines elements of both cloud-based and on-premises ZTNA, allowing organizations to leverage the benefits of each architecture.
ZTNA Implementation Strategies, Secure remote workforces with zero trust network access
Implementing ZTNA involves careful planning and execution. Successful implementations often follow these strategies:
- Phased Approach: Begin with pilot programs in specific departments or locations, gradually expanding the implementation across the organization. This approach allows for testing and refinement before full deployment.
- Comprehensive Security Posture Assessment: Evaluate existing security infrastructure and identify areas for improvement to align with ZTNA principles. This assessment helps in determining the specific requirements and needs for implementation.
- Integration with Existing Systems: ZTNA solutions should be seamlessly integrated with existing systems and workflows to minimize disruption to operations.
Implementing ZTNA for Remote Workforces
Zero Trust Network Access (ZTNA) is no longer a futuristic concept but a crucial element for modern remote work environments. Its implementation is critical for safeguarding sensitive data and maintaining security as employees connect from various locations and devices. This approach ensures that only authorized users and devices can access specific resources within the network, regardless of their location.
This granular control is paramount in today’s dispersed work models.Implementing ZTNA requires a structured approach that addresses both technical and organizational aspects. A clear understanding of the specific needs and limitations of the remote workforce, along with a well-defined implementation strategy, is key to success. Careful planning, thorough testing, and ongoing monitoring are essential to ensure the long-term effectiveness of the ZTNA solution.
Step-by-Step Procedure for Implementing ZTNA
This phased approach ensures a smooth and secure transition to a ZTNA model. Initial steps involve defining the scope and requirements for ZTNA. Next, thorough assessment of existing network infrastructure and security policies is crucial. This allows for a detailed analysis of existing assets and data flow, ensuring ZTNA’s compatibility with existing systems. This stage also involves identifying the specific ZTNA solution that aligns with the organization’s needs.
Careful selection is critical for future scalability and support. After solution selection, the implementation phase involves configuring the chosen ZTNA solution, including access policies, user roles, and device authentication. A final step is rigorous testing and validation to ensure the integrity and security of the deployed ZTNA solution.
Key Components of a ZTNA Solution
A robust ZTNA solution incorporates several key components to achieve comprehensive security and seamless user experiences. These components typically include:
- Identity and Access Management (IAM) System: This system verifies user identities and grants or denies access to specific resources based on predefined policies. A strong IAM system is essential for enforcing Zero Trust principles.
- Network Access Control (NAC) system: NAC enforces policies for user and device access to the network, ensuring only authorized users and devices gain access to specific resources.
- Micro-segmentation: This allows for the segmentation of network resources into smaller, isolated segments. This restricts access to only the necessary resources for specific users or roles, minimizing the impact of security breaches.
- Security Information and Event Management (SIEM) system: SIEM tools monitor network activity, detect anomalies, and provide alerts about potential security threats, enabling proactive response to potential incidents.
Examples of Successful ZTNA Deployments
Several organizations have successfully implemented ZTNA solutions, demonstrating the positive impact on remote work security and productivity. One example is a global financial institution that transitioned to ZTNA to enhance security while maintaining business continuity for remote employees. Another instance is a healthcare provider who deployed ZTNA to protect sensitive patient data accessed by remote clinicians. These successful deployments showcase the practicality and effectiveness of ZTNA in diverse sectors.
ZTNA Vendor Comparison
The following table Artikels various ZTNA vendors and their key features, security protocols, and deployment complexity:
| Vendor | Key Features | Security Protocols | Deployment Complexity |
|---|---|---|---|
| Example Vendor 1 | Multi-factor authentication, granular access controls, real-time threat detection | TLS, IPsec | Moderate |
| Example Vendor 2 | Cloud-based management, automated policy enforcement, seamless user experience | OAuth 2.0, SAML | Low |
| Example Vendor 3 | Strong identity verification, advanced threat protection, flexible policy management | S/MIME, VPN | High |
Security Considerations in Remote Work
Remote work has become the new normal, but this shift presents unique security challenges. Employees working from home, coffee shops, or other locations outside the traditional office environment introduce new vulnerabilities to an organization’s network and data. Understanding these risks and implementing robust security measures is critical to safeguarding sensitive information and maintaining productivity.
Common Security Threats Faced by Remote Workers
Remote workers face a variety of security threats that differ from those in a traditional office setting. These threats exploit the increased reliance on personal devices, less controlled network environments, and often less secure internet connections. Criminals are always looking for opportunities to exploit vulnerabilities, and remote workers are a prime target. Common threats include phishing attacks, malware infections, and social engineering tactics.
- Phishing Attacks: Phishing emails and websites impersonate legitimate organizations to trick employees into revealing sensitive information, such as usernames, passwords, and credit card details. These attacks are highly sophisticated and can easily target remote workers with personalized messages.
- Malware Infections: Malicious software, including viruses, spyware, and ransomware, can infect personal devices used for work. This can compromise confidential data, disrupt operations, and potentially lead to financial losses.
- Social Engineering: Attackers use manipulation and deception to gain access to sensitive information or systems. This includes impersonating colleagues, exploiting trust, or leveraging psychological tactics to trick employees into revealing confidential information.
Importance of Strong Passwords and Multi-Factor Authentication
Strong passwords and multi-factor authentication (MFA) are essential to protect remote workers’ accounts and the organization’s sensitive data. Weak passwords are easily cracked, leaving accounts vulnerable to unauthorized access. Robust authentication methods are crucial to prevent unauthorized access to systems and sensitive information.
- Strong Passwords: Use a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable words or personal information. Change passwords regularly and use a password manager to store and manage them securely.
- Multi-Factor Authentication (MFA): Implement MFA wherever possible. This adds an extra layer of security by requiring a second verification method, such as a code sent to a mobile device, in addition to a password. This significantly reduces the risk of unauthorized access even if a password is compromised.
Significance of Secure Communication Channels
Secure communication channels, such as Virtual Private Networks (VPNs) and encrypted email, are vital for protecting sensitive data transmitted over public networks. These channels encrypt communications, preventing eavesdropping and unauthorized access.
- VPNs: Virtual Private Networks (VPNs) create a secure connection between a remote worker’s device and the organization’s network. They encrypt the data transmitted over public networks, ensuring confidentiality and integrity.
- Encrypted Email: Use encrypted email services to protect sensitive information transmitted via email. This ensures that only authorized recipients can access the content of the message.
Importance of Endpoint Security Solutions
Endpoint security solutions, including antivirus software, firewalls, and intrusion detection systems, are crucial for protecting remote workers’ devices from malware and other threats. These solutions provide a crucial layer of defense against malicious software and unauthorized access attempts.
- Antivirus Software: Antivirus software scans files and applications for malware and other threats. Regular updates are critical to ensure the software can detect the latest threats.
- Firewalls: Firewalls control network traffic, blocking unauthorized access attempts to devices and networks. They are essential for preventing unauthorized connections and protecting sensitive data.
- Intrusion Detection Systems (IDS): IDS monitor network traffic for suspicious activity and alert administrators to potential threats. These systems help proactively identify and mitigate potential security breaches.
Data Loss Prevention (DLP) Strategies for Remote Work Environments
Data Loss Prevention (DLP) strategies are essential for protecting sensitive data in remote work environments. Implementing DLP measures ensures that sensitive data is not accidentally or maliciously disclosed or lost.
- Data Classification: Classify data based on sensitivity and implement access controls accordingly. This helps restrict access to sensitive data based on user roles and responsibilities.
- Data Encryption: Encrypt sensitive data both in transit and at rest. This ensures that even if data is intercepted, it remains unreadable to unauthorized individuals.
- Monitoring and Logging: Implement monitoring and logging solutions to track data access and usage. This allows for the identification of suspicious activity and helps in incident response.
Access Control and User Management in ZTNA
Zero Trust Network Access (ZTNA) is fundamentally built on the principle of least privilege. This means users are granted only the access they absolutely need to perform their job functions. This granular control significantly enhances security posture by limiting the potential impact of a compromised account. ZTNA implements this by meticulously controlling user access to resources, eliminating unnecessary exposure points.ZTNA’s core strength lies in its ability to dynamically adjust access based on context.
A user’s location, device, time of day, and even the specific application they are trying to access all influence the level of authorization they receive. This dynamic control, combined with robust authentication, creates a layered defense against unauthorized access attempts.
User Access Control Mechanisms
ZTNA employs various mechanisms to control user access to resources. These include authentication methods, user roles, and granular permissions. These mechanisms ensure that only authorized users can access specific applications and data. Properly configured access control is critical for preventing data breaches and maintaining business continuity.
Securing remote workforces with zero trust network access is crucial these days. It’s all about verifying every user and device, no matter where they are. This approach is similar to the careful authentication Apple likely considers when designing its products. For example, thinking about how Apple might be revisiting the television market is an interesting thought experiment, is apple considering making a tv again ?
Ultimately, secure remote workforces need this same level of robust security to thrive.
User Authentication Methods
ZTNA supports diverse authentication methods to verify user identities. This flexibility allows organizations to choose the method that best suits their security needs and user base.
- Multi-factor Authentication (MFA) strengthens security by requiring multiple verification steps, such as a password and a code from a mobile device. This significantly reduces the risk of unauthorized access.
- Password-based Authentication, while simple to implement, remains vulnerable to password breaches and social engineering attacks. Strong password policies and regular password changes are crucial for mitigating this risk.
- Biometric Authentication leverages unique physical characteristics for authentication, such as fingerprints or facial recognition. This method provides a high level of security but requires specialized hardware and infrastructure.
User Roles and Permissions
ZTNA facilitates the creation and management of user roles and permissions, enabling organizations to assign specific access rights to different user groups. This allows for precise control over what data and applications users can access.
- User roles define a set of permissions and responsibilities for a group of users. For instance, a “marketing team” role might grant access to specific marketing tools and data, but not to financial records.
- Granular permissions allow for fine-tuned control over individual resources. A user with a “marketing team” role might be granted read access to customer data but only write access to specific marketing campaigns.
Authentication Method Comparison
| Authentication Method | Pros | Cons |
|---|---|---|
| Multi-factor Authentication (MFA) | Enhanced security by requiring multiple verification steps | Can be cumbersome for users, requiring additional devices or software. |
| Password-based Authentication | Simple to implement and widely used | Highly vulnerable to password breaches and social engineering attacks. |
| Biometric Authentication | High security due to reliance on unique physical characteristics | Requires specialized hardware and infrastructure. |
Network Segmentation and Micro-segmentation in ZTNA
Network segmentation and micro-segmentation are crucial components of a robust zero trust network access (ZTNA) strategy. These techniques isolate sensitive data and resources, limiting the impact of potential breaches. By dividing the network into smaller, more manageable segments, organizations can restrict access to specific resources only to authorized users and devices. This approach is essential for maintaining the confidentiality, integrity, and availability of data in a remote work environment.Network segmentation is the logical division of a computer network into smaller, isolated subnetworks.
Think of it like creating separate rooms in a house. Each room has its own security system, and unauthorized access to one room doesn’t automatically grant access to the entire house. This principle applies to computer networks as well.
Network Segmentation: Enhancing Security
Network segmentation enhances security by creating barriers between different parts of the network. This limits the potential damage from a security breach. If a malicious actor gains access to one segment, they are restricted from accessing other segments without additional vulnerabilities. This containment is a critical aspect of a layered security approach.
Micro-segmentation: A Refined Approach
Micro-segmentation takes network segmentation a step further. It breaks down network segments into even smaller, more granular units, often down to individual servers or applications. This is like further dividing the rooms in the house into separate sections, such as a bedroom or living room. This level of detail isolates resources, creating even more barriers to unauthorized access.
This level of granularity allows for fine-grained access controls and significantly reduces the attack surface.
How ZTNA Facilitates Network Segmentation
ZTNA plays a critical role in facilitating network segmentation. By controlling access based on user identity and device posture, ZTNA allows administrators to define which resources a user can access. This granular control is essential for enforcing the principle of least privilege and restricting access to only the resources a user needs. ZTNA inherently supports micro-segmentation by enabling network administrators to define and enforce rules for segment-level access.
Securing remote workforces with zero trust network access is crucial these days. Think about how much easier it is to share files and stream content like with Apple SharePlay, FaceTime, music, Hulu videos, TikTok, and even the stuff shown at WWDC here. But the same principles apply to protecting sensitive data and systems in a remote environment.
Strong network security is still paramount for all companies.
Benefits of Implementing Micro-segmentation
Implementing micro-segmentation offers several advantages, including:
- Reduced attack surface: By isolating resources, the potential damage from a security breach is minimized. If one segment is compromised, the attacker’s reach is limited.
- Improved security posture: A more granular approach to access control and resource isolation creates a stronger security posture.
- Enhanced compliance: Micro-segmentation helps organizations meet regulatory requirements by providing a more controlled and secure network environment.
- Simplified security management: Managing access to smaller segments is often easier and more efficient than managing access to larger, more complex segments.
Monitoring and Management of ZTNA
Zero Trust Network Access (ZTNA) offers enhanced security for remote workforces, but its effectiveness hinges on robust monitoring and management. Without proper oversight, potential vulnerabilities and performance bottlenecks can go unnoticed, leading to security breaches and user frustration. A proactive approach to monitoring and managing ZTNA deployments is crucial for maintaining a secure and efficient remote work environment.Effective ZTNA deployments require constant vigilance to identify and address potential issues.
Real-time monitoring provides critical insights into user activity, application usage, and network performance, enabling timely intervention and proactive security measures. This allows organizations to quickly identify and resolve issues before they escalate into significant problems.
Importance of Monitoring ZTNA Deployments
Monitoring ZTNA deployments is critical for maintaining a secure and reliable remote access environment. Comprehensive monitoring allows organizations to detect and respond to security threats promptly. This includes identifying unauthorized access attempts, unusual network traffic patterns, and application performance issues. Furthermore, monitoring enables organizations to optimize resource allocation and user experience, ultimately improving productivity and cost-effectiveness.
Key Performance Indicators (KPIs) for ZTNA
Several key performance indicators (KPIs) are essential for assessing the health and effectiveness of ZTNA deployments. These KPIs provide insights into various aspects of the system, such as security posture, user experience, and resource utilization.
- Authentication Failure Rate: This KPI tracks the percentage of failed authentication attempts. A high failure rate may indicate a potential security vulnerability or a problem with the authentication process itself.
- User Session Duration: Monitoring average user session durations provides insights into user activity and potential security risks. Abnormally short or long sessions can indicate unauthorized access or issues with application performance.
- Application Performance Metrics: Measuring application response times and throughput enables identification of performance bottlenecks. Slow application performance can lead to user frustration and reduced productivity.
- Network Traffic Volume and Patterns: Monitoring network traffic volume and patterns helps detect unusual activity, such as unauthorized data exfiltration. Anomalies in traffic patterns can signal potential security breaches or application misuse.
- Compliance Violations: Tracking instances of compliance violations, such as unauthorized access or policy breaches, allows for prompt remediation and prevents potential security incidents.
Troubleshooting Common ZTNA Issues
Effective troubleshooting requires a systematic approach to identify the root cause of problems. This involves examining logs, analyzing user activity, and verifying network connectivity.
- User Access Issues: If users experience difficulty accessing applications, verify network connectivity, authentication credentials, and application configurations.
- Application Performance Problems: If applications are slow or unresponsive, investigate network latency, server load, and application configurations.
- Security Alert Management: Establish a process for investigating and resolving security alerts, including logging, analysis, and remediation.
- Network Segmentation Issues: Ensure proper configuration and monitoring of network segments to prevent unauthorized access and maintain security controls.
ZTNA Security Posture Dashboard Design
A well-designed dashboard provides a consolidated view of ZTNA security posture. This dashboard should display key metrics in a clear and concise format, allowing for easy identification of potential problems.
| KPI | Metric | Threshold |
|---|---|---|
| Authentication Failures | Number of failed login attempts | > 10 per hour per user |
| Application Response Time | Average time to load an application | > 5 seconds |
| Network Traffic Anomalies | Deviation from baseline traffic patterns | > 20% |
Tools for Managing ZTNA Deployments
Various tools are available for managing ZTNA deployments. These tools provide centralized control, automated reporting, and simplified troubleshooting.
- Security Information and Event Management (SIEM) tools: SIEM tools consolidate security logs from various sources, enabling comprehensive analysis and threat detection.
- Network Management Tools: These tools provide visibility into network performance, identifying potential bottlenecks and ensuring optimal user experience.
- ZTNA Management Consoles: Dedicated ZTNA management consoles offer centralized control over policies, access, and user management.
Future Trends in Secure Remote Workforces with ZTNA: Secure Remote Workforces With Zero Trust Network Access

The landscape of remote work security is constantly evolving, driven by the increasing sophistication of cyber threats and the ever-expanding adoption of cloud-based services. Zero Trust Network Access (ZTNA) is at the forefront of this evolution, and understanding future trends is crucial for organizations seeking to safeguard their remote workforces. ZTNA, by its very nature, demands a proactive approach to security, requiring continuous adaptation to new threats and technological advancements.The future of secure remote workforces hinges on the ability to anticipate and address evolving security challenges.
This involves not only strengthening existing ZTNA architectures but also integrating emerging technologies to enhance security posture and user experience. Predicting the exact future is impossible, but analyzing current trends and considering emerging technologies allows for proactive security strategies.
Emerging Trends in Remote Work Security
Remote work security trends are heavily influenced by the rapid pace of technological advancement. The constant development of new tools and services creates new attack vectors, necessitating a continuous evaluation and enhancement of security protocols. These evolving threats require a proactive and adaptive approach to security. Increased reliance on cloud services, the rise of IoT devices in the workplace, and the increasing use of artificial intelligence for both legitimate and malicious purposes all contribute to the complex security landscape.
New Technologies Enhancing ZTNA Capabilities
Several emerging technologies are poised to enhance ZTNA capabilities and improve the security of remote workforces. These technologies are often integrated with existing ZTNA solutions to provide a more comprehensive security posture.
- Software-Defined Perimeter (SDP): SDP extends the zero-trust model beyond the network perimeter, providing granular control over access to applications and data regardless of location. This approach offers more flexible and fine-grained access controls, strengthening security posture in remote work environments. For example, a company might use SDP to restrict access to sensitive financial data to only authorized employees, regardless of their physical location.
- SASE (Secure Access Service Edge): SASE consolidates security and networking functions into a single platform, simplifying management and improving the security of remote access. SASE solutions often integrate ZTNA functionalities to provide comprehensive security for remote workers. This approach streamlines security management, reduces complexity, and enables more efficient security operations.
- Advanced Threat Protection (ATP): ATP solutions incorporate machine learning and AI to identify and respond to sophisticated threats in real-time. This capability can be integrated into ZTNA solutions to provide proactive threat detection and mitigation for remote workers, proactively addressing sophisticated attacks.
The Role of AI and Machine Learning in ZTNA
AI and machine learning (ML) are transforming the security landscape. These technologies offer the potential to significantly enhance ZTNA capabilities, particularly in areas of threat detection, user behavior analysis, and automated response. They offer a powerful tool for identifying and mitigating threats, thereby improving the security posture of remote workforces.
- Predictive Threat Detection: AI algorithms can analyze network traffic patterns and user behavior to identify anomalies that may indicate malicious activity. By identifying patterns and anomalies, these systems can proactively identify and address potential threats before they cause significant damage. For example, unusual access requests from an employee’s device could be flagged and investigated, potentially preventing a data breach.
- Adaptive Access Policies: ML can analyze user behavior and device characteristics to dynamically adjust access policies in real-time. This allows for a more responsive and secure access control system, ensuring only authorized users and devices can access resources, regardless of location.
- Automated Incident Response: AI can be used to automate incident response procedures, allowing for faster and more effective handling of security breaches. This can be critical in remote work environments where response time is critical. An example could be an automated response to a suspicious login attempt, blocking the access and notifying the security team immediately.
A Forecast for the Future of ZTNA and Secure Remote Workforces
The future of ZTNA and secure remote workforces will be characterized by a shift toward a more dynamic and automated approach to security. Organizations will rely more heavily on integrated security solutions that leverage AI, ML, and emerging technologies to enhance threat detection and response.
- Increased Automation: Automation of security tasks, such as threat detection, access control, and incident response, will become increasingly common. This will reduce the burden on security teams and improve response times. Automation will also allow for quicker and more consistent responses to threats, reducing potential damage.
- Greater Integration: Security solutions will become more integrated, allowing for a holistic approach to security management. This will enable more seamless and efficient security operations.
- Emphasis on User Experience: While security will remain paramount, the future will see a greater emphasis on providing a positive user experience for remote workers. ZTNA solutions will need to balance security with ease of access to resources.
Outcome Summary
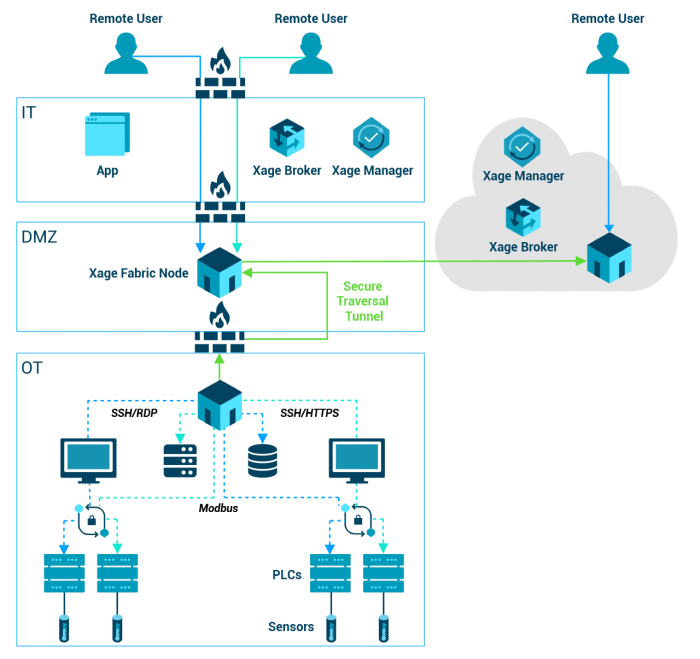
In conclusion, securing remote workforces with zero trust network access is not just a best practice, but a necessity. By understanding the core principles of ZTNA, implementing robust security measures, and continuously monitoring and adapting to emerging threats, organizations can create a secure and productive remote work environment that empowers employees while safeguarding sensitive information. This guide provides a practical framework for navigating the complexities of remote work security and building a secure, future-proof solution.