Replacing VPN and NAC with NGFW for endpoints is a significant security upgrade, offering a more comprehensive and adaptable approach. This transition involves understanding the nuances of each technology and the potential benefits of a next-generation firewall. We’ll explore the differences, deployment considerations, security enhancements, policy implications, migration strategies, and the critical aspects of monitoring and management.
This in-depth look at replacing VPN and NAC with NGFW for endpoints dives into the technical details, practical considerations, and strategic planning required for a successful migration. We’ll examine the pros and cons of each technology, guiding you through the steps needed to evaluate feasibility and ensure a smooth transition. The comprehensive guide covers everything from initial evaluation to ongoing monitoring and maintenance.
Introduction to Network Security
Protecting endpoints from cyber threats is crucial in today’s interconnected world. Various security technologies are employed to safeguard sensitive data and maintain network integrity. Understanding the roles of Virtual Private Networks (VPNs), Network Access Control (NAC), and Next-Generation Firewalls (NGFWs) is essential for implementing effective endpoint security strategies.
Understanding VPNs, NACs, and NGFWs
VPNs, NACs, and NGFWs are all critical components of a robust endpoint security strategy, each with unique functionalities and limitations. VPNs establish secure connections, NACs control access to the network, and NGFWs act as a central security gate. Understanding their individual strengths and weaknesses is vital to selecting the optimal security solution for specific needs.
Fundamental Differences, Replacing vpn and nac with ngfw for endpoints
The fundamental differences between VPNs, NACs, and NGFWs lie in their core functions and approaches to network security. VPNs focus on creating secure tunnels for remote access, NACs prioritize network access control based on device posture, and NGFWs provide comprehensive security features at the gateway. These differences manifest in their respective capabilities and limitations, leading to distinct use cases and deployment scenarios.
| Technology | Function | Pros | Cons |
|---|---|---|---|
| VPN | Establishes secure connections for remote access to the network. | Provides secure remote access, facilitates secure communication between endpoints. | Limited security beyond the tunnel, doesn’t address network access control, and may be susceptible to vulnerabilities in the VPN implementation. |
| NAC | Controls network access based on device posture and security policies. | Enforces security policies, reduces the risk of unauthorized access, and can improve security posture by enforcing device security standards. | Can be complex to implement and manage, may not be sufficient for all security needs, and may not address advanced threats. |
| NGFW | Provides a central security gate, encompassing multiple security features, including intrusion prevention, application control, and threat intelligence. | Comprehensive security features, deep packet inspection, threat intelligence integration, and unified security management. | Requires significant investment in hardware and expertise for proper implementation and management. Can be more complex than VPNs or NACs. |
Typical Use Cases
VPNs are commonly used for remote access by employees working from home or in different locations. A typical use case for NAC is in a company environment to control access to sensitive data and resources based on device compliance and user authentication. NGFWs are frequently employed as a central security point for a network, controlling traffic, and filtering out malicious threats.
Choosing the appropriate solution depends on the specific security requirements and infrastructure.
Potential Benefits of Replacing VPN and NAC with NGFW
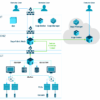
Replacing VPNs and NACs with an NGFW can lead to a more streamlined and efficient security architecture. This centralized approach simplifies management and reduces the complexity of maintaining multiple security systems. An NGFW can often provide more comprehensive security features and better threat detection than individual VPNs and NACs combined.
NGFW Deployment Considerations
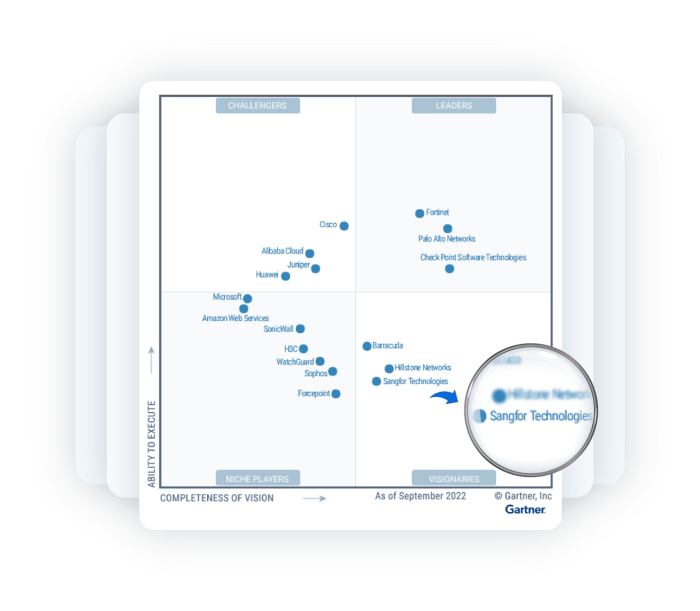
Replacing VPN and NAC with a Next-Generation Firewall (NGFW) for endpoints is a significant security upgrade. Careful planning and evaluation are crucial for a successful transition. This involves assessing the feasibility of the replacement, choosing the right NGFW solution, understanding infrastructure implications, and identifying potential security gaps in the current setup. Understanding the different NGFW deployment models is also essential for a smooth implementation.A thorough evaluation of existing security infrastructure and the desired future state is necessary before proceeding with NGFW deployment.
This includes identifying the specific needs of the endpoints, analyzing current security vulnerabilities, and considering the overall network architecture. Understanding the specific capabilities of the chosen NGFW solution is critical to aligning it with the desired security posture.
Evaluating Feasibility of Replacement
To determine the feasibility of replacing VPN and NAC with NGFW, a detailed assessment of current infrastructure, security policies, and future needs is required. This includes analyzing the current security posture of the network, identifying potential security gaps, and determining the impact of the change on existing workflows and processes. The evaluation must also consider the technical skills and resources available for implementation and ongoing maintenance.
The assessment should also include a cost-benefit analysis to justify the investment in the NGFW solution.
Replacing VPNs and NACs with NGFWs for endpoints is a smart move, especially when considering the broader implications of things like a massive GM EV battery factory investment in Michigan, US. This investment highlights the need for robust cybersecurity solutions to protect sensitive data and infrastructure, and modern NGFWs are perfectly positioned to handle this. Ultimately, shifting to NGFWs offers a more streamlined and secure approach for endpoint protection.
Choosing an NGFW Solution
Several factors influence the choice of an NGFW solution for endpoints. These factors include the specific security requirements of the endpoints, the scalability of the solution to accommodate future growth, the integration capabilities with existing systems, and the vendor support and maintenance offered. Performance and throughput of the NGFW are also important to consider, especially in high-traffic environments.
The ease of management and administration of the NGFW solution should also be evaluated.
Infrastructure Requirements Comparison
The infrastructure requirements for VPN, NAC, and NGFW deployments differ significantly. VPN requires dedicated hardware and software for VPN gateways and client installations. NAC solutions often necessitate additional network access control devices. NGFWs, on the other hand, often integrate security features into existing routers and switches, potentially reducing the need for dedicated hardware. Analyzing the existing infrastructure and its capacity to support the NGFW deployment is critical.
Identifying Security Gaps in Current Solutions
Identifying security gaps in existing VPN and NAC solutions is vital for evaluating the potential benefits of an NGFW. This includes assessing the effectiveness of current security policies, identifying vulnerabilities in the VPN architecture, evaluating the strength of NAC enforcement mechanisms, and checking for compliance with industry standards and regulations. For example, insufficient logging and monitoring capabilities in the VPN and NAC solutions could lead to blind spots in the security posture.
NGFW Deployment Models
NGFW deployment models vary depending on the specific needs and resources of the organization. The most common models include a stand-alone NGFW, a virtual NGFW, and a cloud-based NGFW. Each model has its own strengths and weaknesses, and the best choice depends on the organization’s infrastructure and technical expertise.
Switching from VPNs and NACs to NGFWs for endpoints is a smart move, opening up exciting possibilities. Imagine the potential for enhanced security and streamlined workflows. Plus, you’ll be able to make a custom ChatGPT bot here to automate tasks related to your network configurations, ultimately saving you valuable time and effort. This approach streamlines security management, making it a worthwhile upgrade for modern network environments.
Comparison of Technical Requirements for Different Deployment Models
| Deployment Model | Hardware Requirements | Software Requirements | Management Requirements |
|---|---|---|---|
| Standalone NGFW | Dedicated hardware appliance | NGFW software license | Specialized network administrator skills |
| Virtual NGFW | Virtualization platform (e.g., VMware, Hyper-V) | NGFW virtual appliance | Virtualization expertise and network knowledge |
| Cloud-based NGFW | Cloud infrastructure | Cloud-based NGFW service | Cloud management skills and internet connectivity |
Endpoint Security Enhancements
Moving beyond VPNs and Network Access Controls (NACs) to Next-Generation Firewalls (NGFWs) for endpoint security offers a significant leap forward. Traditional methods often struggle with the evolving threat landscape and the increasing complexity of modern networks. NGFWs provide a more comprehensive and adaptable approach to securing endpoints, enhancing both detection and response capabilities.NGFWs offer a more unified and proactive approach to endpoint security compared to the more segmented solutions provided by VPNs and NACs.
Switching from VPNs and NACs to next-generation firewalls (NGFWs) for endpoints is a major security upgrade, but while we wait for those to be implemented, I’m really excited about the potential of Samsung’s QD OLED TVs. Check out this article on samsungs qd oled tv might be here very soon heres everything we know for all the juicy details.
Ultimately, the shift to NGFWs will be a huge improvement in security, providing a more streamlined and effective approach for endpoint protection.
Instead of relying on isolated security measures, NGFWs integrate security policies across the entire network, creating a more holistic and dynamic defense system. This integration allows for a more streamlined approach to managing and enforcing security policies, which in turn, reduces the risk of vulnerabilities and improves overall network security posture.
NGFWs for Threat Detection and Response
NGFWs significantly enhance threat detection and response compared to VPNs and NACs. Their deep packet inspection capabilities allow them to identify and block malicious traffic in real-time, which significantly reduces the window of vulnerability. This proactive approach minimizes the potential damage caused by cyberattacks, thereby safeguarding critical data and systems. For instance, if a user downloads a malicious file, an NGFW can immediately detect and quarantine it, preventing its spread across the network.
Enhanced Security Features of NGFWs
NGFWs possess features that surpass both VPNs and NACs in terms of security. These advanced features include intrusion prevention systems (IPS), antivirus, and application control. IPS continuously monitors network traffic for malicious activity, while antivirus scans for and neutralizes known threats. Application control restricts access to specific applications, preventing unauthorized use and potentially malicious applications from running on the endpoint.
This layered approach to security strengthens the overall defense against a broader range of threats.
Supported Security Protocols
NGFWs support a wide array of security protocols, providing comprehensive coverage for various network communications. These protocols include but are not limited to: IPsec, SSL/TLS, SSH, and various industry-standard protocols for web traffic. This comprehensive support ensures that the NGFW can handle a variety of network traffic types and applications, reducing the likelihood of vulnerabilities associated with unsupported protocols.
Moreover, NGFWs can be configured to adapt to new protocols as they emerge, maintaining a dynamic security posture.
Performance and Latency Improvements
Using an NGFW for endpoint security can potentially lead to improved performance and reduced latency. By consolidating security functions into a single device, network traffic is streamlined, minimizing bottlenecks and delays. This is particularly beneficial in environments with high volumes of network traffic. The streamlined approach can translate into faster application response times and a smoother user experience, especially for applications that rely on high-speed connectivity.
NGFW vs. VPN and NAC Comparison
| Feature | NGFW | VPN | NAC |
|---|---|---|---|
| Threat Detection | Advanced, real-time, deep packet inspection | Limited, primarily focused on secure communication | Limited, primarily focused on network access |
| Security Features | Comprehensive (IPS, Antivirus, Application Control) | Focuses on secure tunnels | Focuses on network access and compliance |
| Performance | Potentially improved due to centralized security | Can introduce latency due to tunnel establishment | Can introduce latency due to access control checks |
| Flexibility | Highly adaptable to evolving threats | Less adaptable to changing network requirements | Limited flexibility in response to emerging threats |
| Scalability | Easily scalable to handle increasing network traffic | Scalability is often limited by VPN infrastructure | Scalability can be a concern depending on implementation |
Security Policy Considerations
A robust security policy is the bedrock of any successful NGFW implementation. It defines the rules and guidelines for how the firewall will operate, ensuring that sensitive data and resources are protected while allowing legitimate access. This policy must be meticulously crafted to align with the organization’s overall security posture and business objectives. Furthermore, it should be regularly reviewed and updated to address emerging threats and evolving security needs.Effective NGFW implementation requires a comprehensive security policy framework that encompasses user and device authentication, access control, and policy change management.
This framework ensures consistent security across all endpoints, while enabling administrators to effectively manage and maintain a secure network environment. A well-defined policy provides a clear roadmap for the organization’s security posture.
Security Policy Framework
A comprehensive security policy framework for NGFW implementation must address various aspects of network security. This framework will dictate how the NGFW manages traffic, enforces security rules, and responds to security events. It should encompass the organization’s overall security goals and risk tolerance. The policy must be clear, concise, and easily understood by all stakeholders.
User and Device Authentication
User and device authentication are crucial for maintaining the integrity and confidentiality of network resources. Strong authentication mechanisms verify the identity of users and devices attempting to access the network. This verification process helps to prevent unauthorized access and malicious activities. Implementing multi-factor authentication (MFA) significantly strengthens security by requiring multiple verification methods. This is a critical component of any modern security policy, as it adds an extra layer of protection against credential compromise.
Access Control Policy
A strong access control policy is essential for regulating network access. This policy defines which users and devices are permitted to access specific resources and services within the network. Granular access control ensures that only authorized users and devices can interact with sensitive data and critical infrastructure. The policy should clearly define user roles and privileges to enforce the principle of least privilege.
Impact of Policy Changes on Existing Infrastructure
Policy changes can have a significant impact on existing infrastructure. Careful planning and thorough testing are critical before implementing any changes. Potential disruptions to services and data integrity should be anticipated and mitigated through a structured approach to policy implementation. Comprehensive testing should encompass all aspects of the policy, ensuring that existing infrastructure can adapt and function correctly.
This includes thoroughly testing the impact on legitimate user access and network performance.
Sample Security Policy Document Structure
A sample security policy document structure should include sections outlining the organization’s mission, scope, and security goals. It should clearly define the responsibilities of different stakeholders, establish rules for acceptable use, and Artikel the escalation procedures for security incidents. The policy should include detailed descriptions of user roles, access rights, and authentication methods. Specific details about the NGFW’s configuration should also be addressed.
- Policy Overview: Describes the policy’s purpose, scope, and applicability. It includes high-level security objectives and principles.
- Authentication and Authorization: Details the authentication mechanisms (e.g., username/password, MFA) and authorization rules for users and devices. It Artikels access levels and privileges based on user roles.
- Access Control Lists (ACLs): Defines the rules governing network traffic flow. It specifies permitted and denied traffic based on criteria like source/destination IP addresses, ports, and protocols.
- Incident Response: Artikels procedures for handling security incidents, including reporting, escalation, and remediation steps. It should detail who is responsible for handling incidents at different severity levels.
- Monitoring and Auditing: Describes the mechanisms for monitoring the network and logging security events. It Artikels how security logs will be reviewed and analyzed.
Key Policy Components and Configurations
This table Artikels the key policy components and their respective configurations within the NGFW.
| Policy Component | Configuration Details |
|---|---|
| User Roles | Define user roles (e.g., administrator, employee, guest) and assign corresponding access rights. |
| Authentication Methods | Configure supported authentication methods (e.g., username/password, MFA, RADIUS). |
| Access Control Lists (ACLs) | Define rules based on source/destination IP addresses, ports, protocols, and applications. |
| Application Control | Specify allowed and blocked applications based on their signatures or characteristics. |
| Intrusion Prevention System (IPS) | Configure IPS rules to detect and prevent malicious activities. |
| Logging and Reporting | Configure logging and reporting mechanisms for security events. |
Migration Strategy and Planning
Replacing VPN and NAC with NGFW requires a well-defined migration strategy. A phased approach minimizes disruption and allows for thorough testing and validation at each step. This structured approach ensures a smooth transition, maximizing the benefits of the new NGFW while mitigating potential risks.A phased approach ensures that the transition to the new security infrastructure is done in a manageable and controlled way, allowing for adjustments and improvements as needed during each stage.
This approach reduces the overall risk of issues by separating the changes into distinct steps, making troubleshooting and adjustments easier.
Phased Approach to Migration
A phased approach is crucial for a successful migration. Breaking down the migration into smaller, manageable steps minimizes disruption to operations and allows for more focused testing and validation. This approach also facilitates better risk management and reduces the potential for unexpected problems. The phases typically include:
- Assessment and Planning Phase: This initial phase focuses on thoroughly assessing the current network infrastructure, identifying potential compatibility issues, and creating a detailed migration plan. Detailed inventory of existing VPN and NAC systems, network topology, and endpoints is essential. The plan should Artikel specific timelines, resource allocation, and communication protocols.
- Pilot Testing Phase: Deploy the NGFW in a non-production environment, mirroring the production network as closely as possible. This allows for thorough testing of the NGFW’s functionality, performance, and compatibility with existing systems. Testing scenarios should include expected network traffic patterns, including peak usage, to assess performance under load.
- System Validation Phase: Verify the compatibility of the NGFW with existing applications, services, and endpoints. This phase should involve testing security policies, access controls, and user authentication to ensure the new system aligns with security requirements. Testing should include verifying that the NGFW integrates properly with existing monitoring and logging systems.
- Production Deployment Phase: Execute the migration of all endpoints to the NGFW, gradually decommissioning the VPN and NAC systems. Strict adherence to the established plan and rollback procedures is vital. Continuous monitoring and evaluation of the NGFW’s performance are critical to ensure its effectiveness and identify any necessary adjustments.
Testing NGFW Deployment in Non-Production
Testing the NGFW in a non-production environment is essential for ensuring a smooth and risk-free migration. This involves replicating the production network topology, including network devices, endpoints, and application servers.
- Network Topology Replication: The non-production environment should closely mimic the production network to accurately reflect the actual traffic patterns and interactions.
- Endpoint Simulation: Replicate production endpoints, including their configurations and software versions, to accurately test NGFW functionality.
- Security Policy Testing: Implement and test security policies within the non-production environment, including access controls, user authentication, and network segmentation, to ensure proper functioning.
- Performance Evaluation: Evaluate the NGFW’s performance under various conditions, including peak network traffic and specific application usage patterns, to identify potential bottlenecks or issues.
Compatibility Verification Checklist
A comprehensive checklist is crucial for verifying compatibility with existing systems.
| System Category | Compatibility Verification Items |
|---|---|
| Applications | Ensure applications can connect to the network using the NGFW’s access controls. |
| Endpoints | Verify endpoints can communicate with the network after the NGFW deployment. |
| Existing Security Tools | Ensure seamless integration with existing security tools like SIEM and vulnerability scanners. |
| Network Devices | Verify the NGFW’s compatibility with existing routers, switches, and other network equipment. |
Decommissioning VPN and NAC Systems
A structured approach to decommissioning VPN and NAC systems is crucial.
- Phased Shutdown: Gradually decommission the VPN and NAC systems to minimize disruption to network operations.
- Data Backup and Transfer: Backup any critical data associated with the old systems and transfer it to the new system.
- User Training and Communication: Train users on the new security procedures and provide clear communication about the migration process.
- Monitoring and Support: Establish a monitoring process to detect any issues and provide support to users during the transition period.
Migration Process Documentation
Documenting the migration process is essential for future reference and troubleshooting.
- Detailed Plan: Maintain a detailed document of the migration plan, including timelines, responsibilities, and specific tasks.
- Configuration Logs: Record all NGFW configurations and changes made during the migration process.
- Testing Results: Document the results of all testing performed in the non-production environment.
- Troubleshooting Logs: Record any issues encountered during the migration and their resolutions.
Migration Timeline
A realistic timeline for the complete migration process is essential.
- Phase 1: Assessment and Planning (2 weeks)
- Phase 2: Pilot Testing (3 weeks)
- Phase 3: System Validation (2 weeks)
- Phase 4: Production Deployment (1 week)
- Phase 5: Decommissioning (1 week)
Monitoring and Management
Replacing VPNs and NACs with a Next-Generation Firewall (NGFW) for endpoints requires a robust monitoring and management strategy. Effective oversight ensures the NGFW operates optimally, security threats are promptly addressed, and performance is consistently maintained. This crucial aspect allows for proactive identification of issues, enabling swift resolution and maintaining a secure network environment.
NGFW Monitoring Tools
Monitoring the NGFW’s performance and security posture is essential for effective management. Various tools provide insight into traffic patterns, security events, and overall system health. These tools facilitate proactive identification of issues and streamline troubleshooting.
- Network Performance Monitor Tools: These tools track key performance indicators (KPIs) like throughput, latency, and packet loss, providing insights into network health and identifying bottlenecks that could impact NGFW performance. For example, a significant increase in latency could indicate a network congestion issue, prompting investigation and mitigation efforts.
- Security Information and Event Management (SIEM) Systems: SIEM systems aggregate security logs from various sources, including the NGFW, to identify and correlate security events. They provide a centralized view of security threats, enabling faster incident response and analysis. This allows for rapid identification of malicious activities, providing critical information for proactive security measures.
- NGFW Management Console: Most NGFWs offer a comprehensive management console. This provides real-time visibility into firewall rules, traffic flow, and security events. Detailed reporting capabilities offer valuable insights into system performance, enabling proactive maintenance and optimization.
Key Performance Indicators (KPIs)
Tracking key performance indicators (KPIs) is crucial for assessing NGFW effectiveness. These metrics provide a quantitative measure of the NGFW’s performance and security posture.
- Firewall throughput: Measures the rate at which the NGFW can process network traffic. High throughput ensures efficient handling of network traffic. Lower throughput may indicate an issue with the NGFW or network infrastructure.
- Packet drop rate: Measures the rate at which packets are dropped by the NGFW. Low drop rates signify effective network management and minimal packet loss.
- Security event log analysis: Monitoring the number and types of security events logged by the NGFW helps to understand the security posture and identify potential threats. This metric provides a real-time measure of the NGFW’s effectiveness in blocking and detecting malicious activities.
Troubleshooting Common Issues
Troubleshooting common NGFW issues requires a systematic approach. Understanding the root cause of problems enables the development of effective solutions.
- Performance degradation: When the NGFW experiences performance issues, the first step is to examine the CPU usage, memory consumption, and network traffic patterns. If the NGFW is overloaded, adjusting rules or upgrading hardware might be necessary.
- Connectivity issues: Connectivity problems can arise from various sources, including incorrect configurations, network outages, or device failures. Carefully review the firewall configuration, network settings, and system logs to pinpoint the cause. This requires meticulous analysis of logs and configurations.
Security Incident Reporting
Establishing a clear incident reporting process is critical for effective response and prevention. The reporting process should include specific details and escalate events as necessary.
- Clear reporting procedures: Establish clear procedures for reporting security incidents and events. This should include defining roles and responsibilities, documenting procedures, and outlining escalation protocols. This involves creating a formal process for reporting incidents, detailing reporting responsibilities, and establishing escalation paths for severe incidents.
Continuous Monitoring and Maintenance
Continuous monitoring and maintenance of the NGFW are vital for long-term security and optimal performance. Proactive measures ensure timely detection and resolution of potential issues.
- Regular security audits: Conduct regular security audits to identify vulnerabilities and ensure the NGFW’s configuration aligns with security policies. This involves a periodic review of the firewall’s rules, logs, and performance metrics to identify any potential vulnerabilities.
- Regular firmware updates: Keeping the NGFW’s firmware up-to-date is essential for patching vulnerabilities and enhancing functionality. This minimizes the risk of exploitation and improves security posture.
Monitoring Tools and Functionalities
This table illustrates common monitoring tools and their functionalities:
| Monitoring Tool | Functionality |
|---|---|
| Network Performance Monitor | Tracks throughput, latency, and packet loss |
| SIEM System | Aggregates security logs, identifies and correlates events |
| NGFW Management Console | Provides real-time visibility into rules, traffic, and events |
Potential Challenges and Mitigation Strategies
Migrating from VPN and NAC to NGFW for endpoint security presents exciting opportunities for enhanced security posture. However, potential challenges must be anticipated and proactively addressed. Careful planning and execution are crucial to minimize disruptions and ensure a smooth transition. This section Artikels potential roadblocks and effective mitigation strategies.
User Adoption Challenges
User acceptance and compliance with new security protocols are critical for a successful migration. Resistance to change, lack of training, or misunderstanding of new processes can hinder adoption. Implementing a comprehensive user training program, providing clear communication about the changes, and offering ongoing support can effectively address these concerns. This includes demonstrations, FAQs, and regular check-ins to address user concerns and ensure understanding.
A phased rollout, starting with smaller groups or departments, allows for testing and feedback before wider implementation, improving overall acceptance.
Disruptions to Existing Network Services
Potential disruptions to existing network services are a significant concern during a migration. Careful planning and testing are crucial to identify and mitigate these issues. Network monitoring tools and simulations of the migration process can help pinpoint potential problems before they impact users. Implementing a phased rollout, allowing for concurrent operation of the old and new systems, minimizes the risk of service interruptions.
Detailed service level agreements (SLAs) and contingency plans should be in place to address any unforeseen issues.
Importance of Change Management
Change management is paramount for a successful migration. A well-defined change management plan Artikels the steps, timelines, and communication channels for informing and educating stakeholders. This plan should address potential resistance to change, ensuring smooth transition by proactively addressing concerns. Regular communication with users and stakeholders, including updates on progress and anticipated impacts, fosters transparency and trust.
Open communication channels and feedback mechanisms facilitate collaboration and minimize anxieties.
Minimizing Downtime During Migration
Minimizing downtime during the migration is essential to maintain productivity and minimize disruptions. A phased approach, where segments of the network are migrated in stages, allows for parallel operation and avoids complete service outages. Thorough testing of the new infrastructure before full deployment is crucial to identify and fix potential issues. Redundancy in network components and backup systems should be in place to address unexpected failures.
Detailed testing protocols should cover all aspects of the transition, from application compatibility to user access.
Potential Challenges and Mitigation Strategies
| Potential Challenge | Mitigation Strategy |
|---|---|
| User resistance to change | Comprehensive training programs, clear communication, and ongoing support. Phased rollout to allow for feedback and testing. |
| Disruptions to existing network services | Thorough testing of the new infrastructure, network monitoring, phased rollout, concurrent operation of old and new systems, detailed SLAs and contingency plans. |
| Lack of change management | Well-defined change management plan outlining steps, timelines, and communication channels. Proactive addressing of potential resistance to change. Regular communication with stakeholders. |
| Extended downtime during migration | Phased approach, parallel operation, thorough testing, redundancy in network components, backup systems, detailed testing protocols. |
| Compatibility issues with existing applications | Thorough testing of application compatibility with the new NGFW, updating applications as needed. Testing different scenarios with existing applications. |
End of Discussion: Replacing Vpn And Nac With Ngfw For Endpoints
In conclusion, replacing VPN and NAC with NGFW for endpoints represents a powerful step towards enhanced security and network efficiency. While the transition presents challenges, the potential benefits—from improved threat detection to streamlined management—often outweigh the hurdles. Thorough planning, careful consideration of existing infrastructure, and a phased approach are crucial to a successful implementation. Ultimately, the shift to NGFW provides a more robust and future-proof security solution for your endpoints.