Data security mergers acquisitions is crucial in today’s interconnected world. Mergers and acquisitions (M&A) often involve transferring vast amounts of sensitive data, creating unique challenges and risks. This guide delves into the complexities of data security during M&A transactions, covering due diligence, integration strategies, breach preparedness, legal compliance, budgeting, and the use of appropriate technology. Protecting sensitive information throughout the process is paramount.
Understanding the specific risks associated with each stage, from initial due diligence to post-acquisition integration, is vital for successful and secure transactions. This comprehensive approach ensures businesses not only comply with relevant regulations but also maintain the trust and confidence of stakeholders.
Introduction to Data Security in Mergers & Acquisitions

Data security is paramount in mergers and acquisitions (M&A) transactions. The integration of systems and the merging of customer bases create a complex environment where sensitive data is vulnerable. Neglecting data security protocols during M&A can lead to significant financial losses, reputational damage, and legal repercussions. Understanding the intricacies of data security risks and implementing robust safeguards are crucial for a successful and secure transaction.A robust data security framework is essential to mitigate the inherent risks in M&A.
This framework must be carefully considered and implemented throughout the entire transaction lifecycle, from due diligence to post-merger integration. Failing to address data security risks at each stage can expose the combined entity to significant vulnerabilities, potentially jeopardizing the future of the organization.
Importance of Data Security in M&A
Data breaches during M&A can have far-reaching consequences. These breaches can compromise sensitive customer information, intellectual property, and financial data. The potential for reputational damage and legal liabilities is substantial, leading to significant financial losses. A proactive and well-defined data security strategy is critical to minimize the risks associated with data breaches and maintain the trust of stakeholders.
Unique Challenges and Risks in Data Security During M&A
Several challenges and risks are unique to data security during M&A. The merging of different systems and data infrastructures can create inconsistencies and vulnerabilities. The sheer volume of data involved in a large transaction can also present a challenge to effectively secure and manage. Additionally, the integration process itself can introduce new points of entry for malicious actors.
These inherent challenges require meticulous planning and execution to maintain data integrity and prevent breaches.
Consequences of Neglecting Data Security in M&A
Neglecting data security in M&A can lead to severe consequences. Data breaches can result in financial penalties, legal actions, and irreparable damage to the reputation of the merged entity. Financial losses from regulatory fines, legal settlements, and customer churn can be substantial. The loss of trust among customers and stakeholders can have long-term negative effects on the merged company’s future prospects.
Best Practices for Safeguarding Sensitive Information During Due Diligence
Due diligence plays a critical role in identifying and addressing data security vulnerabilities during M&A transactions. Thorough assessments of the target company’s data security practices are essential. This includes examining existing policies, procedures, and security controls. Evaluating the target company’s incident response plan is crucial. A comprehensive review of the target company’s data handling practices, including access controls and data encryption, is also essential.
These best practices will help uncover potential weaknesses and facilitate the development of robust security measures.
Types of Data Impacted in M&A Transactions
The following table Artikels various data types that may be impacted during an M&A transaction, categorized by their sensitivity level, potential risks, and mitigation strategies.
Data security in mergers and acquisitions is a huge concern, especially with the sensitive data often involved. Recent news about the NYT Times tech guild workers winning a tentative union contract here highlights the importance of worker protections in the tech industry. This could potentially influence future negotiations in similar deals, setting a precedent for data security protocols to be prioritized during corporate restructuring.
Stronger worker protections can translate into more robust data security measures.
| Data Type | Sensitivity Level | Potential Risk | Mitigation Strategy |
|---|---|---|---|
| Customer Personally Identifiable Information (PII) | High | Identity theft, financial fraud, reputational damage | Implement robust data encryption, access controls, and secure data storage |
| Financial Data | High | Financial fraud, unauthorized access, data breaches | Employ multi-factor authentication, secure payment gateways, and strict access controls |
| Intellectual Property (IP) | High | Loss of competitive advantage, unauthorized use | Implement robust IP protection measures, data encryption, and access controls |
| Operational Data | Medium | Disruption of operations, loss of productivity | Develop clear data migration plans, conduct thorough system assessments |
| Employee Data | High | Unauthorized access, legal issues, reputational damage | Implement strong access controls, data encryption, and employee training |
Data Security Due Diligence
Data security is paramount in mergers and acquisitions (M&A). A thorough data security due diligence process helps uncover potential risks and vulnerabilities in the target company’s data security posture. This process is crucial to mitigate potential liabilities and ensure a smooth integration of the target company’s data and systems. A comprehensive assessment helps protect sensitive information, maintain compliance, and avoid costly breaches after the acquisition.Data security due diligence is more than just a checklist; it’s a deep dive into the target company’s data security practices.
It’s an investigation into their policies, procedures, technologies, and personnel to identify potential vulnerabilities and areas for improvement. This due diligence process is vital to understanding the target’s existing security measures and their capacity to handle data security after the acquisition.
Importance of Thorough Data Security Due Diligence
A robust data security due diligence process is critical to safeguarding sensitive data and ensuring compliance with regulations. It identifies weaknesses in the target company’s data security, enabling proactive measures to address them before the acquisition. This proactive approach minimizes the risk of costly breaches and legal repercussions. It helps ensure the target company’s security posture aligns with the acquirer’s standards and minimizes potential integration challenges.
Steps Involved in Data Security Due Diligence
The data security due diligence process typically involves several key steps:
- Review of Existing Policies and Procedures: This step involves examining the target company’s documented data security policies, procedures, and compliance certifications. Evaluating their effectiveness and adherence to industry best practices is crucial.
- Assessment of Security Technologies: This includes evaluating the target company’s security infrastructure, including firewalls, intrusion detection systems, encryption protocols, and other security tools. The effectiveness of these technologies and their alignment with current security standards is critical.
- Evaluation of Data Handling Practices: This step focuses on the target company’s procedures for data storage, access control, and disposal. It also assesses their compliance with relevant data protection regulations (e.g., GDPR, CCPA).
- Personnel Evaluation: This includes evaluating the training, experience, and roles of the target company’s data security personnel. Assessing their expertise and capacity to maintain security standards post-acquisition is vital.
- Vulnerability Assessment and Penetration Testing: This step involves simulating real-world attacks to identify vulnerabilities in the target company’s systems. This helps determine the company’s overall security posture and identify areas for improvement.
- Legal and Regulatory Compliance Review: This entails verifying the target company’s adherence to relevant data protection laws and regulations.
Methods for Assessing Data Security Posture
Various methods can be employed to assess the target company’s data security posture. These methods range from interviews and document reviews to penetration testing and vulnerability assessments.
Data security during mergers and acquisitions is crucial. Companies often face challenges integrating systems and ensuring data remains protected. This is where careful planning and robust security protocols are essential. A recent SNL marathon on VH1 Classic, snl marathon vh1 classic , might seem a world away, but the same attention to detail in safeguarding information is paramount in both the entertainment industry and corporate acquisitions.
Ultimately, data security remains a top priority for companies navigating the complexities of mergers and acquisitions.
- Interviews with Key Personnel: Direct interaction with security personnel and key stakeholders provides valuable insights into the target company’s data security practices and potential vulnerabilities. This is often used in conjunction with other assessment methods.
- Review of Documentation: Analyzing the target company’s security policies, procedures, and incident response plans offers a crucial understanding of their existing security framework.
- Security Audits: Independent audits can provide a comprehensive evaluation of the target company’s data security posture, identifying both strengths and weaknesses.
- Penetration Testing: Simulated cyberattacks allow assessment of the target company’s defenses against potential intrusions.
- Vulnerability Assessments: Automated scans can identify vulnerabilities in the target company’s systems and applications.
Crucial Aspects in Assessing Data Security Practices
Several crucial aspects should be considered when evaluating the target company’s data security practices.
- Data Classification and Access Control: Assessing how sensitive data is classified and protected, along with access controls, is vital. This includes verifying that appropriate security measures are in place for different data categories.
- Incident Response Plan: A well-defined incident response plan is essential for mitigating potential data breaches. Evaluation of the plan’s effectiveness and adequacy is crucial.
- Compliance with Regulations: Ensuring compliance with data protection regulations (like GDPR, CCPA) is paramount for avoiding legal issues.
- Third-Party Risk Management: Assessing the security posture of third-party vendors and service providers who handle the target company’s data is critical.
Data Security Due Diligence Methodologies Comparison
| Methodology | Strengths | Weaknesses | Use Cases |
|---|---|---|---|
| Document Review | Cost-effective, quick to implement | Limited scope, may miss undocumented risks | Initial screening, preliminary assessments |
| Interviews | Gain insights into operational aspects, uncover hidden issues | Reliance on honesty, potential for bias | Understanding internal processes, building trust |
| Penetration Testing | Identify vulnerabilities, assess system defenses | Can be costly, time-consuming, may require specialized expertise | Assessing overall security posture, identifying weaknesses |
| Security Audits | Comprehensive evaluation, independent perspective | More expensive, may require significant time investment | Detailed analysis, validating internal controls |
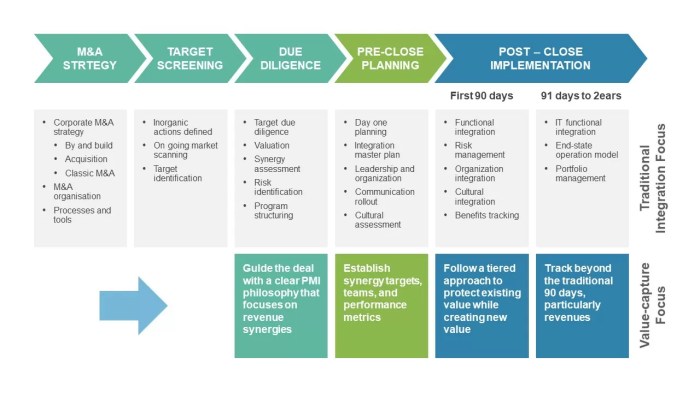
Data Security Integration Strategies
Post-acquisition integration of data security practices is critical for a smooth transition and to mitigate potential risks. A poorly executed integration can lead to security gaps, compliance violations, and reputational damage. A proactive and well-defined strategy is essential to ensure a secure and compliant environment for both the acquired and acquiring organizations.Effective data security integration isn’t just about merging systems; it’s about aligning security policies, procedures, and personnel to create a unified and robust security posture.
This requires careful planning, thorough assessment, and a clear understanding of the unique security needs of each entity. A comprehensive approach that considers the entire lifecycle of data, from storage to disposal, is crucial for maintaining security.
Importance of Integrating Data Security Practices
Data security practices must be integrated seamlessly during the post-acquisition phase to avoid security gaps. A unified security posture ensures compliance with industry regulations and minimizes risks associated with disparate systems and policies. This proactive approach strengthens the overall security posture and safeguards sensitive information.
Data security during mergers and acquisitions is crucial, but sometimes, real-world issues like the recent Ford Expedition and Lincoln Navigator recall for engine fires highlight the importance of thorough due diligence. These recalls, detailed in this informative article about Ford Expedition Lincoln Navigator recall engine fires , show how a seemingly unrelated issue can quickly become a significant factor in the evaluation process for potential buyers.
Ultimately, a strong data security posture is critical in ensuring a smooth and successful transaction.
Strategies for Seamless Integration of Data Security Policies and Procedures
A phased approach to integration is recommended, beginning with a thorough assessment of existing security policies and procedures. This assessment identifies areas for improvement and alignment between the acquired and acquiring organizations. Standardizing security protocols, access controls, and incident response procedures is vital. Implementing consistent training programs for all employees ensures a unified understanding of security best practices.
Comparison and Contrast of Various Data Security Integration Methodologies
Different methodologies exist for data security integration. A common approach involves a phased integration, starting with a detailed assessment and gradually implementing unified policies and procedures. Another approach focuses on a parallel integration, maintaining separate systems for a certain period while concurrently establishing a unified security framework. The chosen methodology depends on the specific needs and resources of each organization.
Challenges in Aligning Disparate Data Security Systems
Integrating disparate data security systems presents significant challenges. Differences in technologies, platforms, and security tools require careful consideration and a detailed plan for migration and standardization. Ensuring data consistency and avoiding data loss during the transition is crucial. Addressing cultural differences in security practices and establishing a common understanding of security responsibilities are important aspects to consider.
Benefits of a Comprehensive Data Security Integration Strategy
A comprehensive data security integration strategy offers several key benefits. Improved security posture, compliance with industry regulations, and reduced risk of security breaches are significant advantages. Increased efficiency and cost savings are achieved by streamlining security operations. Enhanced data protection, which leads to increased confidence and trust from stakeholders, is also a key benefit.
Data Security Integration Models
| Model Type | Benefits | Drawbacks | Implementation Steps |
|---|---|---|---|
| Phased Integration | Reduced risk of disruption, gradual adaptation to new systems, allows for thorough testing | Can be time-consuming, may require significant resources, potential for inconsistencies during transition | Assessment of current security posture, identification of common standards, implementation of standardized policies and procedures in phases |
| Parallel Integration | Minimizes disruption, allows for concurrent operation of systems, facilitates easier assessment of new systems | Can be more costly in the long run, potential for data inconsistencies, requires careful planning for data synchronization | Maintain separate systems for a transitional period, establish parallel procedures, integrate systems gradually while maintaining separate operations |
| Big Bang Integration | Faster implementation, reduced transition time | High risk of disruption, potential for significant data loss, requires extensive planning and testing | Complete overhaul of systems, simultaneous implementation of unified policies and procedures |
Data Breach Preparedness and Response
A robust data breach preparedness and response plan is crucial for any organization, especially during mergers and acquisitions (M&A). A well-defined plan can minimize damage, mitigate legal liabilities, and restore trust with stakeholders in the event of a data security incident. This is particularly critical in M&A as the combined data environment of the merging entities can be significantly more complex and vulnerable.Effective data breach preparedness and response planning is essential for minimizing disruption and reputational damage.
A comprehensive strategy needs to be in place to address the unique challenges posed by the integration of disparate data systems and security protocols.
Necessity of a Robust Data Breach Plan
A proactive approach to data breach preparedness is vital. A well-structured plan is essential to mitigate the significant financial, reputational, and legal risks associated with data breaches. These plans must address the specific vulnerabilities introduced by the merger, such as the integration of different security systems, protocols, and data storage practices. Thorough planning will enable swift and effective response, minimizing the impact of a potential breach.
Key Elements of a Comprehensive Data Breach Plan
A comprehensive data breach plan should encompass several key elements:
- Risk Assessment: Identify potential data breach risks specific to the combined organization, including vulnerabilities in legacy systems, integration points, and employee training gaps. This should consider the unique risks presented by the acquisition.
- Incident Response Team: Establish a dedicated team with clearly defined roles and responsibilities for handling data breaches. This team should include representatives from IT, legal, communications, and senior management.
- Data Inventory: Create a detailed inventory of all sensitive data, including location, access controls, and security measures. This inventory must encompass all data from both merging organizations.
- Security Protocols: Establish and maintain up-to-date security protocols, including access controls, encryption, and regular security audits. These protocols must be harmonized across the merged entities.
- Communication Plan: Develop a clear and concise communication plan to inform stakeholders (employees, customers, regulators) about the breach and the response. This plan should detail the steps for disseminating information effectively.
Steps to Take in the Event of a Data Breach
A structured approach to data breach response is essential for minimizing damage and ensuring legal compliance. These steps should be clearly defined and rehearsed to ensure smooth execution during a crisis:
- Confirmation and Containment: Immediately confirm the breach, isolate affected systems, and prevent further data compromise. The goal is to contain the incident quickly.
- Notification: Notify relevant stakeholders, including affected individuals, regulatory bodies, and law enforcement. Timing and clarity are critical in notification.
- Investigation: Conduct a thorough investigation to determine the cause, scope, and extent of the breach. This includes examining system logs, reviewing access points, and potentially involving forensic experts.
- Remediation: Implement measures to remediate the breach, such as restoring affected systems, patching vulnerabilities, and strengthening security controls. This phase requires careful coordination and execution.
- Post-Incident Review: Conduct a thorough review of the incident response process to identify areas for improvement and prevent future breaches. Lessons learned should be incorporated into future security practices.
Legal and Regulatory Implications of Data Breaches in M&A
Data breaches during M&A transactions can trigger significant legal and regulatory consequences. These implications can vary significantly based on jurisdiction, the type of data compromised, and the size of the organization.
Step-by-Step Guide for Handling a Data Breach During an M&A Transaction
A step-by-step approach to handling a data breach in an M&A transaction is essential for managing the process effectively. Each step is crucial for ensuring compliance and minimizing negative impact.
- Immediate Containment: Contain the breach and prevent further data exposure.
- Assessment: Assess the scope and impact of the breach.
- Notification: Notify relevant stakeholders.
- Investigation: Investigate the root cause.
- Remediation: Implement measures to restore affected systems and strengthen security.
- Legal Counsel: Consult legal counsel on regulatory compliance and potential liabilities.
Data Breach Response Procedures, Data security mergers acquisitions
| Breach Stage | Actions | Communication Plan | Legal Considerations |
|---|---|---|---|
| Confirmation | Contain the breach, isolate affected systems, prevent further compromise | Initial notification to relevant parties | Document all actions, preserve evidence |
| Investigation | Determine cause, scope, and extent of the breach | Keep stakeholders informed of investigation progress | Compliance with data breach notification laws |
| Remediation | Restore affected systems, strengthen security, implement patches | Inform stakeholders of remediation efforts | Ensure compliance with data security regulations |
| Post-Incident Review | Analyze the incident, identify weaknesses, implement preventive measures | Share lessons learned and improvements with stakeholders | Document findings for future prevention |
Legal and Regulatory Compliance
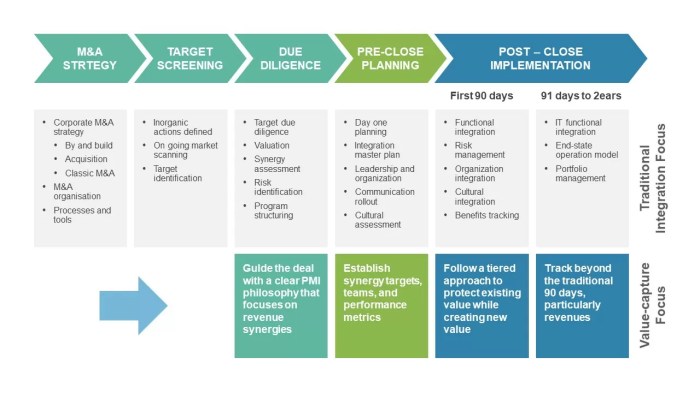
Navigating the legal landscape of mergers and acquisitions (M&A) requires meticulous attention to data security regulations. Compliance is not just a best practice; it’s a critical component of a successful transaction, directly impacting the financial and reputational well-being of the merging entities. Failure to anticipate and address these legal obligations can lead to significant penalties and disruptions, potentially jeopardizing the entire deal.Data protection regulations are increasingly stringent across the globe.
This necessitates a proactive approach to understanding and adhering to these regulations, which often vary significantly by jurisdiction. Thorough due diligence, comprehensive integration strategies, and robust preparedness for potential data breaches are all directly linked to successful legal compliance.
Crucial Legal and Regulatory Requirements
Data security in M&A transactions is governed by a multitude of regulations, primarily focusing on data privacy and protection. These regulations often mandate specific procedures for data handling, security, and transparency, encompassing the entire lifecycle of data from collection to disposal. Key areas include the handling of personal data, ensuring the security of sensitive information, and maintaining appropriate records.
Implications of Non-Compliance
Failure to comply with data security regulations can result in substantial penalties, ranging from hefty fines to legal repercussions. Breaches can damage reputation, leading to loss of customer trust and significant financial losses. Furthermore, non-compliance may impede future transactions and operations. Examples include the significant fines levied against companies for data breaches in violation of GDPR, demonstrating the severity of the consequences.
Role of Legal Counsel
Legal counsel plays a pivotal role in ensuring data security compliance throughout the M&A process. They advise on relevant regulations, identify potential risks, and guide the development of policies and procedures to address these risks. Counsel can also assist in conducting due diligence, ensuring compliance with contractual obligations, and managing potential legal disputes related to data breaches. This expertise is invaluable in navigating the complexities of data protection laws.
Ensuring Adherence to Data Privacy Regulations
Adherence to data privacy regulations requires a multi-faceted approach. This includes conducting comprehensive data mapping exercises to identify all relevant data assets and their locations. Implementing robust security controls to protect data from unauthorized access, use, disclosure, or alteration is crucial. Regularly reviewing and updating data security policies and procedures is essential to address evolving regulatory landscapes.
Furthermore, establishing clear communication channels for data security incidents and incidents management processes are vital.
Key Data Protection Regulations Globally
| Region | Key Regulations | Enforcement Mechanisms | Penalties |
|---|---|---|---|
| EU | GDPR | Data Protection Authorities (DPAs) at the national level | Significant fines; potentially up to 4% of global annual turnover |
| USA | CCPA, HIPAA, GLBA | Federal Trade Commission (FTC), state Attorneys General | Varying, depending on the specific violation and the governing law |
| Canada | PIPEDA | Office of the Privacy Commissioner of Canada | Fines and other enforcement actions |
| Brazil | LGPD | National Data Protection Authority (ANPD) | Fines and other enforcement actions |
| Japan | Act on the Protection of Personal Information | Ministry of Internal Affairs and Communications, local authorities | Varying, depending on the specific violation |
Data Security Budget Considerations: Data Security Mergers Acquisitions
Securing data in mergers and acquisitions (M&A) is paramount. A robust data security strategy needs a well-defined budget, reflecting the unique risks and opportunities presented by each transaction. A well-planned budget not only protects sensitive information but also demonstrates a commitment to data integrity to stakeholders. Ignoring data security during M&A can lead to substantial financial losses and reputational damage.Effective data security in M&A goes beyond simply purchasing the latest software.
It demands a comprehensive approach encompassing people, processes, and technology. This requires meticulous planning, clear allocation of resources, and ongoing monitoring to adapt to emerging threats. A thorough data security budget helps ensure that the necessary resources are available to address all aspects of data protection, from due diligence to post-merger integration.
Allocating Resources for Data Security in M&A
Data security should be treated as a critical investment, not a cost. Sufficient resources dedicated to data security measures are crucial for a successful M&A integration and minimize the risk of a data breach. A comprehensive approach to data security must be planned and integrated from the initial stages of due diligence to the post-integration phase. The budget should be flexible to accommodate potential unforeseen challenges or changes in the regulatory landscape.
Creating a Data Security Budget Framework
A structured approach to budgeting is essential for effective resource allocation. The framework should align with the overall M&A strategy and include a detailed assessment of potential risks. The budget should be categorized to clearly reflect the different stages of the M&A process, from due diligence to integration and beyond. Key elements should include:
- Due Diligence Phase: This phase necessitates a detailed assessment of the target company’s data security posture, including identifying vulnerabilities, evaluating compliance with regulations, and assessing the current state of data protection measures.
- Integration Phase: This phase involves implementing data security measures to ensure the smooth integration of the acquired company’s systems and data with the acquirer’s. This often requires investment in new tools and infrastructure.
- Ongoing Maintenance and Monitoring: Data security is an ongoing process. Resources are needed for regular security assessments, threat monitoring, incident response planning, and employee training to maintain a robust defense.
Costs Associated with Data Security Measures
The costs of various data security measures vary considerably, depending on the specific needs and scope of the M&A transaction. These costs need to be carefully evaluated and factored into the overall budget.
- Security Audits and Assessments: Independent assessments of data security practices can cost from tens of thousands to hundreds of thousands of dollars depending on the scope and complexity of the audit. A comprehensive assessment identifies weaknesses and areas for improvement, which is invaluable in planning for post-acquisition data security initiatives.
- Data Encryption and Access Control: Implementing strong encryption and access control measures requires investment in software licenses, implementation costs, and ongoing maintenance. Costs can vary widely depending on the scale and sophistication of the solution.
- Incident Response Planning and Training: Developing and maintaining an incident response plan, coupled with employee training on data security protocols, are essential components of a robust security posture. These initiatives can range from thousands to tens of thousands of dollars depending on the size and scope of the program.
Justifying Data Security Spending to Stakeholders
Data security spending requires clear justification to stakeholders. Focus on the potential financial losses from a data breach, the return on investment (ROI) from implementing security measures, and the importance of maintaining a strong reputation. Use quantifiable metrics and examples to highlight the potential impact of data breaches.
Different Approaches to Securing Data Security Funding
Several approaches can be employed to secure funding for data security initiatives in M&A transactions. These include:
- Dedicated Budget Allocation: A separate budget for data security initiatives, explicitly approved by senior management, demonstrates the organization’s commitment to data protection.
- Cost-Benefit Analysis: Present a clear cost-benefit analysis to stakeholders, highlighting the potential financial losses from a data breach and the ROI of security investments.
- Negotiating Inclusion in Deal Terms: Incorporate data security clauses into the M&A agreement, requiring the target company to meet specific security standards or allocate resources to enhance security post-acquisition.
Estimated Costs for Data Security Measures in M&A
| Security Measure | Estimated Cost | Return on Investment | Justification |
|---|---|---|---|
| Security Audits (Comprehensive) | $50,000 – $200,000 | Reduced risk of data breaches, improved compliance, and identification of vulnerabilities | Essential for understanding the target company’s security posture and proactively addressing potential weaknesses. |
| Data Encryption and Access Control | $25,000 – $150,000 | Protection of sensitive data, enhanced compliance, and reduced risk of unauthorized access | Critical for safeguarding sensitive data and ensuring compliance with data protection regulations. |
| Incident Response Plan and Training | $10,000 – $50,000 | Reduced recovery time in case of a breach, improved incident response efficiency, and minimized reputational damage | Essential for effectively handling security incidents and minimizing potential negative consequences. |
Last Recap
In conclusion, navigating data security during mergers and acquisitions requires a proactive and multifaceted approach. Thorough due diligence, robust integration strategies, and a comprehensive breach response plan are essential for mitigating risks and ensuring compliance. Understanding the legal and regulatory landscape, along with allocating appropriate resources and employing suitable technology, are equally crucial. This guide provides a roadmap for organizations seeking to successfully integrate data security into their M&A processes, safeguarding sensitive information and preserving their reputation.