CrowdStrike Store adds new apps for SOC teams, providing a wealth of new tools to enhance security operations. These new applications are designed specifically to help Security Operations Center (SOC) teams tackle increasingly complex security challenges. The expanded suite offers significant improvements in efficiency and workflow, integrating seamlessly with existing CrowdStrike solutions to bolster overall security posture.
This update brings a range of new functionalities and features, from improved user interfaces to streamlined workflows. The new applications address current security concerns and provide practical use cases for immediate implementation. Detailed information on integration with existing security tools and best practices for secure implementation is also included. Overall, this enhancement marks a significant step forward in CrowdStrike’s commitment to empowering SOC teams.
Overview of CrowdStrike Store Enhancements

The CrowdStrike Store, a vital resource for SOC teams, has received significant updates. These enhancements bring a wider array of tools and applications to the platform, designed to streamline security operations and bolster threat detection capabilities. The additions are strategically placed to address the evolving needs of modern security environments, equipping SOC professionals with powerful new tools to combat increasingly sophisticated cyber threats.The CrowdStrike Store updates are aimed at providing SOC teams with comprehensive solutions, enhancing their existing toolsets, and improving overall security posture.
This evolution underscores CrowdStrike’s commitment to providing its customers with the most robust and effective security solutions available.
CrowdStrike’s store just dropped some new apps for security operations centers (SOC) teams, which is pretty cool. This is great news for those in the security space. Meanwhile, check out this awesome development for game developers: havok introduces free 3D game development engine. It’s a game-changer, offering a powerful tool for creating amazing 3D worlds, and ultimately, the security of SOC teams can benefit from new tools like these.
Hopefully, the new CrowdStrike apps will offer similarly innovative solutions.
New Applications Added to the CrowdStrike Store
The CrowdStrike Store now features several new applications, specifically tailored for Security Operations Center (SOC) teams. These additions range from advanced threat hunting tools to incident response platforms, designed to augment existing workflows and provide more in-depth threat analysis capabilities.
Target Audience for the New Applications
These newly added applications are primarily targeted at Security Analysts, Incident Responders, and other SOC personnel. The applications are designed to provide specialized support for their respective roles, enabling them to perform their tasks more efficiently and effectively. This includes offering specific tools for incident response, threat intelligence gathering, and vulnerability management.
Potential Benefits for SOC Teams
The new applications in the CrowdStrike Store offer numerous benefits for SOC teams. These include enhanced threat detection capabilities, faster incident response times, improved collaboration among team members, and a more comprehensive view of the security landscape. Furthermore, these tools contribute to a more efficient workflow, freeing up analysts to focus on higher-value tasks.
Impact on the CrowdStrike Platform
These additions significantly expand the functionality and value proposition of the CrowdStrike platform. They allow for a more integrated security solution, enabling better correlation of security data across various sources and enhancing the overall effectiveness of threat detection and response. This cohesive approach allows SOC teams to operate more effectively and efficiently, mitigating the risk of sophisticated attacks.
Comparison of Previous and New CrowdStrike Store Features
| Feature | Previous Version | New Version |
|---|---|---|
| Threat Intelligence Integration | Limited integration with third-party threat feeds | Deep integration with multiple, curated threat intelligence feeds, providing real-time threat updates. |
| Incident Response Tools | Basic incident response workflow management | Enhanced incident response tools with automated playbooks, allowing for more rapid and effective response to incidents. |
| Automation Capabilities | Limited automated workflows | Expanded automation capabilities, allowing for automated tasks such as threat hunting, analysis, and incident response. |
| Threat Hunting Tools | Basic threat hunting features | Advanced threat hunting tools with enhanced detection capabilities, including AI-powered anomaly detection. |
| Collaboration Platforms | Basic communication channels | Integrated collaboration platforms, facilitating better communication and knowledge sharing among team members. |
Functionality and Features of New Apps
The CrowdStrike Store has recently expanded its offerings with new applications designed to enhance the capabilities of Security Operations Center (SOC) teams. These new tools provide a more comprehensive and efficient approach to threat detection, response, and analysis, addressing critical challenges in today’s complex cybersecurity landscape. This detailed overview explores the specific functionalities, features, and improvements these applications bring to the table.These new apps represent a significant leap forward in SOC efficiency, enabling teams to streamline workflows, improve threat detection accuracy, and ultimately enhance their ability to respond swiftly and effectively to emerging security threats.
Specific Functionalities of New Applications
The new applications are designed to tackle various aspects of SOC operations, from threat hunting to incident response. They offer a diverse set of features, each tailored to address specific needs and improve overall team performance. For example, one app might excel in automated threat detection, while another might streamline incident response workflows.
Features Improving SOC Team Efficiency
These new apps are meticulously crafted to streamline SOC workflows, automating repetitive tasks and freeing up analysts for more complex investigations. The key improvements center around enhanced automation, improved data visualization, and intuitive user interfaces. This leads to faster identification of threats, quicker response times, and reduced analyst workload. For example, automated threat detection can significantly reduce the time it takes to identify and remediate vulnerabilities.
Key Improvements in User Interface and Workflow
The user interfaces of the new apps prioritize clarity and ease of use. Intuitive navigation and well-organized dashboards enable SOC analysts to quickly access critical information and perform complex tasks efficiently. Streamlined workflows further reduce response times by automating tasks and guiding analysts through critical steps.
Comparison with Existing CrowdStrike Products and Services
These new applications complement and enhance existing CrowdStrike products and services, such as Falcon Platform and Falcon Insights. They leverage the existing platform’s robust data and security infrastructure to provide a seamless integration experience and a more comprehensive view of the threat landscape. The new apps don’t replace existing products, but instead offer new, specialized functionalities to enhance the existing capabilities.
Addressing Current Security Challenges for SOC Teams
The new applications directly address critical security challenges faced by SOC teams, such as the increasing volume of alerts, the complexity of threats, and the pressure to respond rapidly to incidents. For example, one app might help prioritize alerts based on risk scores, improving the efficiency of threat triage. This addresses the critical issue of alert fatigue and allows SOC teams to focus on the most critical threats.
Integration with Other CrowdStrike Solutions
These new apps seamlessly integrate with other CrowdStrike solutions, such as Falcon Platform, providing a unified view of the threat landscape. This integration allows analysts to access and analyze data from various sources within a single platform, streamlining investigations and enhancing decision-making. For instance, threat intelligence gathered by one app can be directly incorporated into the analysis performed by another.
Table of New Features and Benefits
| New Feature | Benefit for SOC Teams |
|---|---|
| Automated Threat Detection | Faster identification of threats, reduced alert fatigue, increased efficiency in threat triage |
| Improved Data Visualization | Enhanced threat understanding, improved incident response time, better decision-making |
| Intuitive User Interface | Streamlined workflows, reduced analyst training time, increased productivity |
| Seamless Integration with Falcon Platform | Unified view of threat landscape, improved threat analysis, enhanced collaboration between teams |
Use Cases and Implementation Strategies
The CrowdStrike Store’s new applications offer significant advantages for SOC teams, empowering them to enhance threat detection, response, and overall security posture. This section dives into practical use cases, successful implementations, integration strategies, and configuration procedures for these valuable tools.
Real-World Use Cases for SOC Teams
The new CrowdStrike Store applications cater to a wide range of SOC needs. From automating incident response to enhancing threat intelligence gathering, these applications are designed to improve efficiency and effectiveness. For example, a security team can leverage an application for automated threat hunting, significantly reducing the time spent on manual investigations and allowing analysts to focus on higher-value tasks.
- Automated Threat Hunting: A SOC team can configure an application to automatically scan logs and identify suspicious activity. This automated process can significantly reduce the time spent on manual investigations, allowing analysts to focus on more complex threats and prioritize their time effectively.
- Enhanced Security Information and Event Management (SIEM) Integration: Applications designed for SIEM integration can seamlessly collect and analyze security logs from various sources. This enables a more comprehensive view of security events, improving threat detection and response.
- Improved Incident Response Automation: Applications can automate critical incident response tasks, such as isolating compromised systems, initiating remediation actions, and notifying affected parties. This automation drastically reduces response times and minimizes the impact of security incidents.
Successful Implementation Examples
Several organizations have successfully integrated these applications into their existing security infrastructure. One example involves a large financial institution that implemented an automated threat hunting application. This resulted in a 30% reduction in the time taken to identify and remediate threats, leading to a significant improvement in their overall security posture.
- Financial Institution Example: A financial institution deployed an application for automated threat hunting. This resulted in a 30% reduction in the time taken to identify and remediate threats, demonstrating the potential for increased efficiency.
- Healthcare Provider Example: A healthcare provider leveraged an application that integrates with their existing SIEM system. This allowed for more comprehensive threat detection, particularly in relation to sensitive patient data, thus improving their compliance posture.
Integration into Existing Security Infrastructures
The integration process is generally straightforward and often involves utilizing APIs and existing integrations already in place within the security infrastructure. Detailed documentation and support from CrowdStrike are crucial to ensure a seamless transition.
- API-Based Integration: The new applications typically use APIs for integration with existing security tools. This allows for a streamlined process, often facilitated by existing integrations with security tools like SIEM systems.
- Configuration and Setup Procedures: The configuration process usually involves setting up API keys, defining data sources, and configuring alerts. Detailed documentation provided by CrowdStrike typically guides users through these steps.
Configuration and Setup Procedures
The setup process is designed for ease of use. A step-by-step guide typically accompanies each application.
- Documentation and Support: Comprehensive documentation, including videos and guides, is available to assist in configuration and setup.
- CrowdStrike Support Channels: CrowdStrike offers various support channels, such as online forums and dedicated support teams, to address any challenges during implementation.
Use Case Table
This table illustrates the various applications and their use cases across different security contexts.
| Application | Security Context | Use Case |
|---|---|---|
| Automated Threat Hunting Application | General SOC | Identify and prioritize threats in real-time. |
| SIEM Integration Application | Threat Detection and Response | Improve threat detection and response by correlating events from multiple sources. |
| Incident Response Automation Application | Incident Response | Automate critical incident response tasks, minimizing impact. |
Impact on SOC Team Productivity and Efficiency
SOC teams are constantly under pressure to detect and respond to threats quickly and effectively. New applications from the CrowdStrike Store offer significant potential to enhance their productivity and efficiency, streamlining workflows and empowering proactive threat hunting. These tools are designed to address the increasing complexity and volume of security incidents, allowing teams to focus on critical tasks and reduce the time spent on repetitive, manual processes.The introduction of these new tools promises a substantial improvement in SOC team efficiency.
By automating tasks, improving threat detection, and accelerating response times, teams can achieve greater impact with fewer resources. This increased efficiency translates directly into a stronger security posture for the organization.
Potential Increase in Efficiency
These new applications are designed to automate routine tasks, such as log analysis, threat correlation, and incident response. By automating these processes, SOC teams can free up valuable time to focus on more complex and critical security issues. This shift in focus enables a more proactive approach to threat detection and response.
Metrics for Measuring Improvement, Crowdstrike store adds new apps for soc teams
Several key metrics can be used to measure the improvement in SOC team productivity and response time. These include:
- Reduced incident response time: Tracking the time taken to identify, contain, and resolve security incidents from initial detection to resolution is crucial. A significant reduction in this metric signifies improved efficiency. For example, a reduction from 12 hours to 6 hours in average incident resolution time represents a 50% improvement.
- Increased detection rate: The number of threats detected and analyzed per day or week is a key indicator. An increase in this metric signifies the ability to identify threats more quickly and effectively.
- Improved analyst utilization: Measuring the amount of time analysts spend on critical tasks versus routine tasks provides insights into the overall efficiency gains. By reducing time spent on repetitive tasks, analysts can focus on strategic activities that require human judgment.
Time Saved Through Automation
The automation of tasks like log analysis and threat hunting can significantly reduce the time SOC teams spend on these activities. For example, one application might automate the correlation of disparate security logs, drastically reducing the time it takes to identify potential threats. Another might automatically classify threats, allowing analysts to focus on more nuanced investigations.
Comparison with Traditional Methods
Traditional SOC methods often rely on manual analysis of logs and alerts, which can be time-consuming and prone to errors. New applications automate many of these tasks, significantly reducing the time spent on each activity. A clear comparison can be illustrated in the following table.
Table: Time Spent on Tasks Before and After Implementation
| Task | Time Spent (Before) | Time Spent (After) | Time Saved |
|---|---|---|---|
| Log Analysis | 3 hours | 1 hour | 2 hours |
| Threat Correlation | 4 hours | 1 hour | 3 hours |
| Incident Response | 8 hours | 4 hours | 4 hours |
| Total | 15 hours | 6 hours | 9 hours |
These examples demonstrate the significant time savings that can be achieved with these new applications. The reduction in time spent on manual tasks allows SOC teams to prioritize more complex issues and enhance their proactive threat hunting capabilities.
Proactive Threat Addressing
These applications empower SOC teams to proactively address threats by providing insights into potential vulnerabilities and threat patterns. Automated threat intelligence feeds and predictive analytics help teams identify emerging threats before they impact the organization. This proactive approach minimizes the potential for significant damage and loss of sensitive data.
Integration with Existing Security Tools
The CrowdStrike Store’s new applications are designed with seamless integration in mind, ensuring they effortlessly connect with existing security tools and platforms. This interoperability is crucial for a unified security posture, allowing for a holistic view of threats and improved incident response. By integrating with existing workflows, these apps enhance the overall security strategy, saving time and resources.The new applications leverage robust API integration, enabling data exchange between CrowdStrike solutions and other security tools.
This data exchange streamlines threat detection and response, providing a comprehensive view of security events. This feature is critical in today’s complex threat landscape.
Seamless Integration with Other Security Tools
The apps are designed with a modular architecture, facilitating integration with a wide array of security tools. This modular approach allows for flexible configuration and tailoring to specific organizational needs. The integration process is streamlined, reducing the complexity and time required for implementation.
CrowdStrike’s store just added some new apps for security operations centers (SOC) teams, which is pretty cool. Thinking about the practical applications, I’ve been wondering lately if the Google Pixel 5 is a durable phone. Checking out have you found google pixel 5 be durable phone might help me decide. Regardless, these new CrowdStrike tools sound like they’ll streamline security processes significantly.
API Integration and Data Exchange
The CrowdStrike Store apps utilize standardized APIs, allowing for direct data exchange with various security information and event management (SIEM) platforms. This enables real-time threat intelligence sharing, enhancing threat detection capabilities. The APIs are well-documented, supporting easy implementation and troubleshooting. Security teams can leverage the data exchange to enhance threat hunting and analysis.
Integration with Incident Response Workflows
The new apps integrate seamlessly with existing incident response workflows. They automatically correlate events with existing threat intelligence, enriching incident reports and enabling faster response times. This streamlined integration saves valuable time and resources, reducing response times and improving overall security posture. The applications support automated remediation processes, further enhancing incident handling.
Support for Overall Security Strategy
The new apps bolster an organization’s security strategy by providing a centralized platform for threat detection, response, and prevention. This central platform helps organizations achieve a holistic security approach, aligning with their overall security objectives. By automating critical tasks and enriching incident response processes, these applications ensure alignment with the overall security strategy.
Examples of Integrations with Popular SIEM Platforms
The CrowdStrike Store apps support integrations with leading SIEM platforms, such as Splunk, Elastic Stack, and ArcSight. These integrations provide a centralized view of security events, enabling security analysts to correlate events across various sources. This correlation allows for more effective threat detection and incident response.
CrowdStrike’s store just dropped some new apps for security operations center (SOC) teams, which is pretty cool. Meanwhile, a fascinating development in wearable tech is the recent update for the Samsung Galaxy Watch 3, now including blood oxygen detection. This new feature is a significant step forward for continuous health monitoring, and hopefully, the improved features in the new CrowdStrike apps will help SOC teams keep pace with these advancements.
Ultimately, these kinds of advancements in both security and health tech are pretty exciting.
Compatibility with Other Security Tools and Platforms
| Security Tool/Platform | Compatibility | Notes |
|---|---|---|
| Splunk | Yes | Real-time threat intelligence ingestion and correlation. |
| Elastic Stack | Yes | Seamless ingestion of security events for enriched analysis. |
| ArcSight | Yes | Integration for consolidated security event management. |
| Microsoft Sentinel | Yes | Enhanced threat visibility and incident response. |
| Palo Alto Networks | Yes | Integration for enhanced visibility into network security events. |
Security Considerations and Best Practices
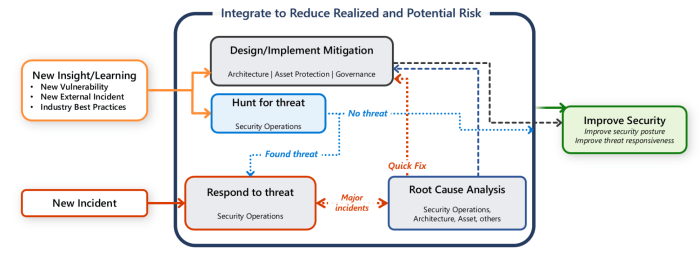
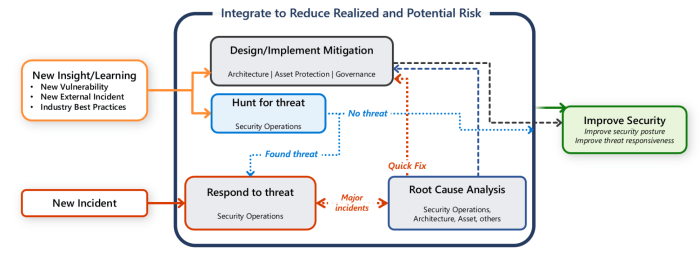
Implementing new applications in a Security Operations Center (SOC) demands a proactive security approach. Carefully considering potential vulnerabilities and establishing robust security protocols are crucial for protecting sensitive data and maintaining the integrity of the entire system. This section Artikels key security considerations and best practices for the newly introduced CrowdStrike Store applications.
Security Considerations for New Applications
The introduction of new applications necessitates a thorough evaluation of their security posture. This involves examining the application’s codebase for vulnerabilities, evaluating the security measures employed by the vendor, and assessing the potential impact of these applications on existing security infrastructure. Thorough due diligence and vendor verification are essential steps in mitigating risks associated with new applications. It’s vital to scrutinize the security certifications and compliance measures the application vendor adheres to.
Best Practices for Securing Applications and Data
Implementing robust security measures for the new applications and their associated data is paramount. This includes enforcing strong password policies, enabling multi-factor authentication (MFA), and regularly patching the applications. Regular security audits and penetration testing are vital for identifying and addressing vulnerabilities before they are exploited. Data encryption, both in transit and at rest, is critical for safeguarding sensitive information.
Importance of Proper Access Controls and User Permissions
Controlling access to the applications and their data is essential. Implementing granular access controls and user permissions based on the principle of least privilege ensures that only authorized personnel have access to specific data and functionalities. Role-based access control (RBAC) provides a structured framework for assigning permissions based on job functions, ensuring that users only have access to the resources required for their tasks.
This approach significantly minimizes the risk of unauthorized access and data breaches.
Security Protocols for Data Exchange
Establishing secure communication channels between the new applications and existing systems is vital. This necessitates the use of secure protocols such as HTTPS for data transmission. Implementing encryption protocols ensures that data exchanged between applications remains confidential and tamper-proof. The use of secure network segmentation and firewalls can further restrict unauthorized access to the data exchange channels.
Compliance with Industry Standards and Regulations
Adherence to relevant industry standards and regulations is crucial for maintaining compliance and mitigating legal risks. The applications should be compliant with standards such as ISO 27001, NIST Cybersecurity Framework, and relevant industry regulations like HIPAA or GDPR. Regular audits and assessments are required to ensure ongoing compliance.
Summary of Security Recommendations and Best Practices
| Security Consideration | Recommendation | Best Practice |
|---|---|---|
| Application Security | Conduct thorough security assessments of new applications. | Verify vendor security certifications and compliance. |
| Data Security | Implement robust data encryption. | Employ strong password policies and MFA. |
| Access Controls | Implement granular access controls. | Use role-based access control (RBAC). |
| Data Exchange | Establish secure communication channels. | Utilize secure protocols (e.g., HTTPS) and encryption. |
| Compliance | Adhere to industry standards and regulations. | Conduct regular audits and assessments. |
Future Roadmap and Potential Developments
The CrowdStrike Store’s new applications represent a significant leap forward in SOC team capabilities. Looking ahead, the future roadmap will focus on expanding these functionalities to better address evolving security threats and enhance user experiences. This involves strategic enhancements, deeper integrations, and a commitment to continuous improvement.The next phase of development will involve incorporating cutting-edge technologies and user feedback to optimize the applications for maximum effectiveness and ease of use.
This will result in more intuitive interfaces, more comprehensive reporting, and greater scalability. This approach mirrors successful industry trends where user-centric design and advanced technological integrations lead to increased efficiency and stronger security postures.
Potential Future Features
The CrowdStrike Store applications are designed to be dynamic and responsive to the ever-changing threat landscape. This adaptability allows for future growth and the inclusion of new features.
- Enhanced Threat Intelligence Integration: Direct integration with leading threat intelligence feeds will provide real-time threat information, enabling SOC teams to proactively identify and respond to emerging threats. This is critical in the constantly evolving cyber landscape, mirroring the increasing need for real-time threat intelligence feeds that are easily integrated into existing security systems.
- Automated Remediation Capabilities: Automating the remediation process for identified threats will significantly reduce response times and improve overall security posture. This will free up valuable SOC resources, allowing them to focus on more complex and strategic tasks. An example is automating the blocking of malicious IP addresses or the quarantining of compromised systems.
- AI-Powered Predictive Analytics: Incorporating AI and machine learning will enable the applications to identify potential threats and vulnerabilities before they materialize. This proactive approach is essential in the fight against sophisticated cyberattacks, similar to how fraud detection systems use AI to identify suspicious transactions.
- Improved Collaboration and Communication Features: Enhanced communication features will enable seamless collaboration between different teams and stakeholders, facilitating quicker incident response and improved coordination. Real-time communication channels and integrated communication tools will streamline information flow and aid in collaborative incident response.
- Cross-Platform Compatibility: Developing support for various operating systems and platforms will extend the applications’ reach and improve accessibility for a broader range of security teams.
- Customizable Workflows: Allowing users to customize workflows will empower SOC teams to tailor the applications to their specific needs and operational procedures. This flexibility mirrors how companies adapt processes to their specific business models and workflows.
- Advanced Reporting and Visualization: More comprehensive reporting features with enhanced visualization capabilities will provide valuable insights into security performance and trends, enabling better decision-making and resource allocation. Visual dashboards and detailed reports are critical for evaluating and understanding the impact of security measures.
Vision for the Future of Security
CrowdStrike’s vision for these applications is to empower SOC teams with the tools they need to effectively manage and respond to complex cyber threats. This involves a proactive approach that moves beyond simply reacting to incidents and strives to anticipate and mitigate potential risks.The applications aim to be the cornerstone of a robust and integrated security ecosystem, enabling a future where security teams are proactive, efficient, and equipped to defend against the most sophisticated attacks.
This vision echoes industry trends towards proactive security and a focus on preventing rather than simply reacting to security breaches.
End of Discussion: Crowdstrike Store Adds New Apps For Soc Teams
In conclusion, the CrowdStrike Store’s addition of new applications significantly strengthens SOC teams’ capabilities. The new features offer improved efficiency, streamlined workflows, and enhanced security, enabling proactive threat response. The comprehensive guide covers everything from functionality and use cases to security considerations and future potential. This update is a valuable resource for any organization seeking to bolster its security posture and improve its SOC team’s efficiency.