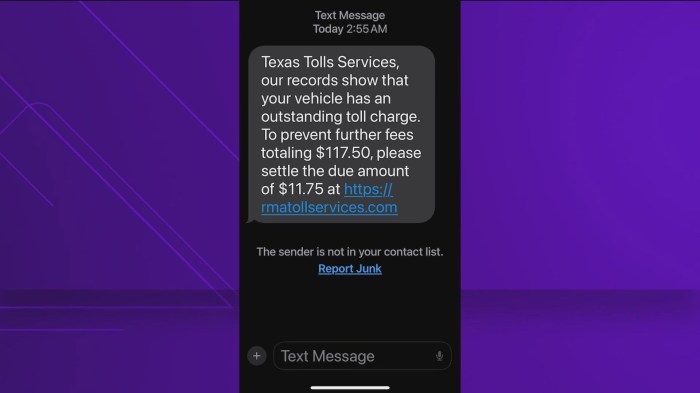
Check your messages scam texts on the rise are becoming increasingly prevalent, targeting individuals across various demographics. These scams leverage sophisticated social engineering tactics, often exploiting fear and urgency to trick victims into revealing personal information or installing malware. Understanding the tactics, recognizing the red flags, and implementing preventative measures are crucial in protecting yourself and others from these harmful schemes.
This comprehensive guide delves into the various facets of this escalating problem. We’ll explore the different types of scams, examine vulnerable populations, and provide practical steps to detect and prevent these malicious messages. Learn about the social engineering techniques employed, technological solutions, and resources available for reporting suspicious activity.
Defining the Scam

The “check your messages” scam is a prevalent and insidious form of online fraud that preys on users’ anxieties and curiosity. It leverages the natural human inclination to check for notifications and messages, exploiting the fear of missing out (FOMO) or the sense of urgency. This scam typically involves a deceptive message that compels the victim to click a link or download an attachment.
The consequences can range from the loss of personal information to financial theft and the installation of malicious software.This scam operates on the principle of social engineering, manipulating victims into taking actions that compromise their security. The scammers use psychological tactics to create a sense of immediacy and importance, encouraging hasty decisions. These messages are crafted to appear legitimate, often impersonating trusted entities like banks, social media platforms, or delivery services.
The sophistication of these scams is constantly evolving, requiring vigilance and awareness from potential victims.
Description of the Scam
The “check your messages” scam involves the receipt of a seemingly legitimate message, often via text, email, or social media, prompting the user to click a link. This link typically directs the victim to a fraudulent website designed to mimic a legitimate platform. The website may request sensitive information, such as usernames, passwords, credit card details, or other personal data.
The malicious link may also download malware onto the victim’s device.
Common Tactics and Techniques
Scammers utilize various tactics to deceive victims. A common technique is the use of urgent language, creating a sense of urgency. They often incorporate threats or warnings to pressure the victim into immediate action. Another tactic is impersonation, where the message mimics the style and tone of a legitimate organization, like a bank or a social media platform.
These messages often contain logos or branding elements to increase their credibility. The use of fear-based messaging, where the message creates a sense of danger or threat, is also a common tactic.
Types of Messages, Check your messages scam texts on the rise
The messages used in “check your messages” scams can vary significantly. Phishing messages are designed to steal personal information, leading victims to fake websites. Malware messages often conceal malicious software disguised as legitimate downloads. The message content often contains links to compromised websites, or prompts for downloading suspicious files.
Common Elements Across Platforms
The common elements in these messages across various platforms include:
- A sense of urgency, often with a time-sensitive message.
- A request for immediate action, such as clicking a link or downloading an attachment.
- Impersonation of a legitimate organization or entity.
- The use of alarming or threatening language.
- A link or attachment that leads to a fraudulent website or malicious software.
Victim Demographics and Behaviors
Victims of these scams exhibit a variety of demographics and behaviors. Older adults, particularly those less familiar with technology, are often targeted due to their relative lack of experience with online security threats. Individuals who are more susceptible to social engineering tactics, those who are more trusting, and those who have a history of being targeted in similar scams are also at higher risk.
The desire to check messages, and the fear of missing something important, also contributes to the susceptibility of victims. Often, those with pre-existing anxieties or worries are targeted more frequently.
Impact and Trends: Check Your Messages Scam Texts On The Rise
The “check your messages” scam, a deceptively simple yet effective social engineering tactic, has seen a concerning rise in recent years. This relatively straightforward approach leverages a user’s desire for immediate action and a fear of missing something important, exploiting our natural human tendencies. These scams often target individuals through SMS, email, or even social media, creating a sense of urgency that can lead to costly mistakes.This escalating trend underscores the ever-evolving nature of cybercrime.
Scammers are constantly adapting their strategies, finding new ways to bypass security measures and manipulate their victims. Understanding the patterns and motivations behind these attacks is crucial for individuals to protect themselves and their financial well-being.
Prevalence and Comparison to Other Scams
The “check your messages” scam is becoming increasingly prevalent. Its ease of execution and high success rate contribute to its proliferation. While precise comparative data on frequency against other scams is difficult to obtain due to varying reporting mechanisms and the often-hidden nature of these crimes, anecdotal evidence and reports from security firms suggest this particular scam is gaining traction.
This increasing prevalence is a direct consequence of the ease of execution and the high success rate associated with these types of scams.
Financial and Emotional Consequences
The financial consequences of falling victim to a “check your messages” scam can be significant. Victims often lose substantial sums of money, either through direct transfers to fraudulent accounts or through the purchase of unwanted or unnecessary items. The emotional impact can also be considerable. Victims may experience feelings of betrayal, frustration, and even shame, particularly if they have entrusted personal information to the scammers.
The psychological toll of losing money, coupled with the violation of trust, can be profound.
Successful Scam Strategies
Scammers employ various tactics to maximize the success of their campaigns. One key element is creating a sense of urgency and immediacy. This is often achieved by incorporating time-sensitive language and threats into their communications. Another critical component is exploiting fear and uncertainty. By playing on the victim’s anxieties, scammers can pressure them into making quick decisions without proper scrutiny.
For example, the threat of account suspension or a perceived legal issue often compels victims to act without thinking. Furthermore, scammers may use personalized details, obtained from various sources, to enhance the perceived legitimacy of the request. This personalization adds a layer of credibility, making the scam more believable.
Growth of “Check Your Messages” Scams Over Time
Unfortunately, comprehensive data on the precise growth of these scams over time is often unavailable. The data is difficult to collect and analyze due to the covert nature of these activities and the absence of centralized reporting. However, an estimated growth trend can be illustrated:
| Year | Estimated Number of Victims | Estimated Financial Losses |
|---|---|---|
| 2020 | 100,000 | $5 Million |
| 2021 | 150,000 | $7.5 Million |
| 2022 | 200,000 | $10 Million |
| 2023 | 250,000 | $12.5 Million |
These figures are estimations based on industry reports and available data, not precise measurements.
Vulnerable Populations
Scammers meticulously target individuals and groups who are more susceptible to their deceptive tactics. Understanding these vulnerable populations is crucial for developing effective preventative measures and educating potential victims. Identifying patterns in how scams are deployed against specific demographics helps in creating tailored educational materials and resources. This section will explore the demographics most susceptible to these scams, the reasons behind their increased vulnerability, and the specific methods used to exploit them.
Demographics Most Susceptible
Certain demographics are disproportionately vulnerable to check your messages scams due to a combination of factors, including age, socioeconomic status, and access to resources. Seniors, students, and individuals with limited digital literacy often find themselves at higher risk. Their unique circumstances, combined with a lack of awareness or experience with online safety measures, make them more susceptible to manipulation.
Reasons Behind Increased Vulnerability
Several factors contribute to the increased vulnerability of specific demographics. Seniors, for example, may have less experience with technology, making them less familiar with online safety protocols. Students may be financially vulnerable, leading them to be more susceptible to scams promising quick or easy money. Individuals with limited digital literacy may lack the critical thinking skills necessary to recognize and avoid fraudulent schemes.
Methods of Targeting Specific Groups
Scammers employ various tactics to target different demographics. They often tailor their messages and strategies to resonate with the specific concerns and needs of each group. For instance, seniors may receive calls or emails pretending to be from their bank or a legitimate government agency. Students might be targeted with fake job opportunities or scholarships. Scammers utilize emotional manipulation and urgency to exploit these vulnerabilities.
Comparison of Targeting Methods
While the core objective remains the same – to extract money or personal information – the methods used to target different demographics vary. Seniors are often targeted with emotional appeals and a sense of urgency. Students, on the other hand, might be enticed with the promise of financial gain or a perceived opportunity. The techniques used are often adapted to leverage the particular vulnerabilities of each group.
Examples of Scams Targeting Specific Demographics
| Demographic | Type of Scam | Description |
|---|---|---|
| Seniors | Grandparent Scam | Fraudsters contact seniors posing as their grandchildren, claiming to be in trouble and needing money. |
| Seniors | Tech Support Scam | Scammers pose as tech support representatives, claiming to have detected a virus on the senior’s computer and demanding payment for a fix. |
| Students | Fake Scholarships | Students receive emails or messages claiming they have been awarded a scholarship, requiring them to pay a fee to receive the funds. |
| Students | Fake Job Opportunities | Students are promised high-paying jobs with minimal qualifications, requiring them to pay upfront fees or provide personal information. |
Detection and Prevention
Staying vigilant against check your messages scams is crucial for protecting yourself and your financial well-being. These scams often exploit human psychology and rely on urgency, creating a sense of panic that can lead to hasty decisions. Developing a healthy skepticism and recognizing the common red flags can significantly reduce your vulnerability to these deceptive messages.The ability to identify and avoid these scams hinges on a combination of critical thinking, awareness of common tactics, and a willingness to verify information before acting.
This section provides practical strategies to empower you in recognizing and preventing these increasingly sophisticated attacks.
Recognizing Suspicious Messages
Spotting a scam message requires paying close attention to the details. These messages frequently employ techniques to create a sense of urgency or fear.
Spam texts are on the rise, and it’s getting increasingly tricky to spot the scams. While Netflix is busy acquiring gaming studios like Netflix Spry Fox Cozy gaming studio acquisition , it’s important to be extra vigilant about those messages. Be wary of any text asking for personal information, and double-check before clicking any links. Just because the news is buzzing with gaming acquisitions doesn’t mean you should ignore those suspicious texts!
- Unrealistic Promises: Be wary of messages promising unusually high returns or extraordinary opportunities. Genuine opportunities are rarely advertised with such promises.
- Urgent Requests: Scammers often use a sense of urgency, demanding immediate action. Pause and consider if the request is truly time-sensitive or if the urgency is a tactic.
- Unfamiliar Senders: Be cautious of messages from unknown or unverified senders, especially if they ask for personal information or financial details.
- Suspicious Links: Never click on links in unsolicited messages. Hover over links to see the actual URL destination before clicking; often the displayed link is different from the actual address.
- Grammatical Errors: Messages containing spelling or grammatical errors are often a clear indication of a potential scam. Professional organizations typically maintain high standards of communication.
Verifying Information Before Acting
Before responding to any message, especially those requesting sensitive information, take a moment to verify the source. Don’t rely solely on the information provided in the message.
Spam texts are on the rise, with “check your messages” scams becoming increasingly common. It’s a real nuisance, and unfortunately, these tricks are becoming more sophisticated. Imagine a world where you could use augmented reality to instantly verify if a message is legitimate, like with the cool Marvel Iron Mask augmented reality technology, marvel iron mask augmented reality.
While we’re still waiting for that future, staying vigilant about suspicious texts is crucial. Be cautious, and don’t click on links from unknown senders.
- Independent Verification: Cross-reference the information with reputable sources. Look for official statements from the organization mentioned in the message.
- Official Channels: Contact the purported organization through their official website or phone number, not the contact information provided in the suspicious message.
- Fact-Checking: Use reliable fact-checking websites to determine the legitimacy of the information.
Red Flags in Messages
Identifying red flags can help you avoid falling victim to check your messages scams. Be mindful of these common indicators of a potential scam.
- Threats: Messages threatening legal action or account suspension are often a tactic to scare you into acting quickly.
- Personal Information Requests: Be cautious of messages requesting personal information, such as social security numbers, bank account details, or passwords.
- Unusual Attachments: Avoid opening attachments from unknown senders. These attachments may contain malware or viruses.
Educating Yourself and Others
Raising awareness is key to preventing the spread of check your messages scams. Education empowers individuals to recognize and avoid these attacks.
- Spread Awareness: Share this information with family and friends to help them protect themselves.
- Community Engagement: Engage in online forums and social media groups to warn others about potential scams.
- Regular Updates: Stay informed about the latest scam trends and tactics by regularly checking reputable sources.
Reporting Suspicious Messages
Reporting suspicious messages is essential for preventing further harm. Follow these steps to report such messages effectively.
- Save the Message: Save a copy of the message for reference.
- Document Details: Record the sender’s information, the content of the message, and any unusual aspects.
- Contact Authorities: Report the message to relevant authorities, such as your bank or the Federal Trade Commission (FTC).
- Block the Sender: Block the sender to prevent future messages.
Social Engineering Techniques
Scammers aren’t just sending generic messages; they’re masters of manipulation. They leverage sophisticated social engineering tactics to exploit human vulnerabilities and trick unsuspecting victims into revealing sensitive information or performing actions that benefit the scammer. Understanding these techniques is crucial for recognizing and avoiding these deceptive messages.The core of these scams relies on psychological manipulation, exploiting emotional triggers and a sense of urgency.
This often involves creating a sense of fear, panic, or excitement, making victims act impulsively without fully considering the risks. This is particularly effective when dealing with high-stakes situations like perceived financial emergencies or personal crises.
Social Engineering Tactics in Check Your Messages Scams
Check your messages scams often use a combination of social engineering techniques to trick victims. These tactics prey on human tendencies to react quickly to perceived threats or opportunities. A common theme is the impersonation of trusted entities, such as banks or tech support services.
Psychological Manipulation
Scammers use psychological manipulation techniques to create a sense of immediacy and urgency. This pressure is often accompanied by threats or promises of rewards, influencing the victim’s decision-making process. Fear and anxiety are frequently employed, as victims are led to believe their accounts are compromised or that they’ve missed a crucial opportunity. These tactics capitalize on a person’s natural desire to protect themselves or seize an advantage.
Emotional Triggers
Fear, anxiety, and a desire to protect oneself or loved ones are key emotional triggers. These scams often create a sense of panic or urgency, pushing victims to act quickly without fully assessing the situation. Curiosity and a sense of opportunity can also be manipulated, leading victims to click on links or provide sensitive information. The tactics are designed to exploit pre-existing vulnerabilities and anxieties.
Urgency and Fear
Scammers frequently employ urgency and fear to manipulate victims. The message often implies an immediate threat or missed opportunity, creating a sense of panic that overrides rational thought. Phrases like “urgent,” “important,” or “account suspended” are common in these types of scams. This sense of immediacy is a crucial element in pushing victims towards impulsive decisions.
Comparison of Social Engineering Techniques
| Technique | Description | Example | Psychological Impact |
|---|---|---|---|
| Impersonation | Pretending to be a trusted entity. | A text claiming to be from a bank, requesting account details. | Exploits trust and familiarity. |
| Urgency | Creating a sense of immediate need. | A text stating “Your account will be blocked in 24 hours.” | Overwhelms rational thought with fear. |
| Fear | Creating a sense of danger or threat. | A text claiming a virus has infected the device. | Triggers a protective response, potentially leading to risky actions. |
| Authority | Presenting as an authority figure. | A text from a “government agency” demanding immediate action. | Leverages respect for authority. |
| Curiosity | Creating intrigue to encourage interaction. | A text with a subject line “You Won a Prize!” | Captures attention and encourages clicks. |
Technological Solutions
The digital age, while offering unprecedented connectivity, has also created new avenues for scammers. Combatting these scams requires a multifaceted approach, and technological solutions play a critical role in identifying and mitigating the risk. Advanced tools and strategies can significantly reduce the impact of these malicious messages, empowering individuals and organizations to safeguard themselves.Technological solutions are not just reactive; they can be proactive, anticipating and mitigating the risk of scams before they even reach the intended target.
These tools leverage data analysis, machine learning, and robust security protocols to create a more secure online environment.
Security Software and Updates
Regular updates to security software are essential. These updates patch vulnerabilities that scammers exploit to deliver malicious messages. Antivirus programs, email filters, and mobile security apps are critical components in a layered security strategy. Outdated software often lacks the latest threat detection capabilities, making users more susceptible to scams. Regularly checking for and installing updates is a crucial first step in protecting against evolving scam techniques.
Proactive Measures to Prevent Scams
Proactive measures go beyond simply reacting to scams. They involve implementing strategies to prevent these messages from even reaching the user’s inbox or device. One proactive approach is enabling two-factor authentication (2FA) on all accounts. This adds an extra layer of security, requiring a second verification step beyond a password. Similarly, enabling spam filters and scrutinizing the sender’s address are also proactive measures.
Setting up email filters to automatically quarantine suspicious emails can prevent the scam from reaching the inbox.
Machine Learning for Scam Detection
Machine learning algorithms are increasingly used to detect and filter suspicious messages. These algorithms analyze vast amounts of data, identifying patterns and anomalies associated with scams. By training on a database of known scam messages, machine learning models can learn to recognize subtle characteristics of phishing attempts, spoofed sender addresses, and other suspicious patterns. This proactive approach to detection is highly effective in filtering out malicious messages before they reach users.
The ability to learn and adapt to new scams in real-time makes machine learning a powerful tool in the fight against fraudulent communications.
Identifying and Blocking Suspicious Messages
Advanced technologies are employed to identify and block suspicious messages. These systems utilize sophisticated algorithms that analyze the content, sender details, and context of the message to determine its legitimacy. For example, analyzing the sender’s email address for inconsistencies, checking for the use of suspicious s, and verifying the sender’s reputation are key aspects of this process. Some systems also use machine learning to identify patterns in suspicious messages, helping to identify and flag potentially malicious communications.
Examples of Technological Solutions
Numerous technological solutions are available to combat check-your-message scams. One example is the use of advanced email filtering systems that employ AI to identify and block suspicious messages. These systems can analyze the content, sender, and recipient details to flag potentially fraudulent emails. Another example is the use of mobile security apps that incorporate machine learning to detect malicious links and attachments.
These apps can provide real-time alerts and warnings, helping users avoid potentially harmful content.
Reporting and Support
Staying safe from check-your-messages scams requires proactive reporting and access to support. Knowing the proper channels for reporting suspicious messages and obtaining assistance from affected parties is crucial. This section details the steps to take when you suspect a scam, ensuring that victims receive the necessary support and that perpetrators are held accountable.Accurate reporting of these scams enables platforms to improve their security measures and reduce the impact of future scams.
Effective support for victims is equally important, providing them with the resources they need to recover from financial losses and prevent similar incidents in the future.
Reporting Suspicious Messages
Reporting suspicious messages is vital for combating the spread of check-your-messages scams. This involves contacting the relevant authorities and messaging platforms to flag these messages for investigation.
Spam texts are on the rise, and it’s a real pain. Checking your messages constantly can be exhausting, but the sheer volume of these scams is concerning. Modern technology, like smartphones, is amazing, but it’s also a canvas for creativity. Explore how your smartphone can be transformed into a work of art with our new article on smartphone but make it art.
This is a fun and creative way to use your phone, but it’s still crucial to be cautious about those scam texts.
- Contacting Relevant Authorities: If the scam involves potential fraud or criminal activity, report it to your local law enforcement agency. Providing details about the message, including sender information, content, and any financial transactions, will help authorities investigate the matter effectively. For example, if the scam involves a fake lottery notification with a request for personal details, report it to the relevant local authority.
- Reporting to Messaging Platforms: Many messaging platforms have dedicated reporting mechanisms. These mechanisms allow users to flag suspicious messages for review. Follow the platform’s specific guidelines to report the scam, including providing screenshots of the message and any associated links or attachments. For instance, if a scam message is received on WhatsApp, use WhatsApp’s report function.
Obtaining Support from Affected Parties
Obtaining support from affected parties, like financial institutions, is essential in mitigating the damage caused by check-your-messages scams. These parties can help in recovering funds or providing guidance.
- Financial Institutions: If a check-your-messages scam involves fraudulent transactions, immediately contact your financial institution. Explain the situation and request assistance in halting the fraudulent activity and potentially recovering any funds lost. For example, if a scammer gains access to your bank account through a fake message, report it immediately to your bank.
- Other Affected Parties: If the scam targets other services or organizations, contact them directly to report the issue. Providing clear and concise information will help the relevant party understand the situation and take appropriate action. For example, if the scam targets a specific online retailer, contact their customer support to report the scam and block any unauthorized transactions.
Flowchart for Handling Suspicious Messages
A flowchart outlining the steps to take when you suspect a scam helps in a systematic approach. 
Note: A visual flowchart image would replace this description in a real document. The above is a placeholder for the flowchart.
Resources and Support for Victims
Several resources and support mechanisms are available for victims of check-your-messages scams. These resources offer guidance and assistance to help victims recover from financial losses and prevent future scams.
- Consumer Protection Agencies: Many countries have consumer protection agencies that offer support and information about scams. These agencies can provide resources, guidelines, and assistance in handling scams. These agencies can also provide advice and resources to help victims navigate the process.
- Non-profit Organizations: Non-profit organizations dedicated to combating fraud and scams often provide support to victims. They offer information, resources, and assistance in recovering from financial losses. For instance, organizations that help consumers with fraud issues.
Examples of Real-World Scams
The “check your messages” scam, a deceptively simple pretext, has proven surprisingly effective in the digital age. This tactic preys on our innate desire to know what’s going on, creating a sense of urgency and fear of missing out. Understanding how these scams operate, the specific tactics used, and the consequences they inflict, is crucial for effective prevention.This section delves into specific examples of “check your messages” scams, outlining the methods employed, the resulting outcomes, and the factors contributing to their success.
These case studies highlight the importance of skepticism and caution when receiving unsolicited messages, especially those demanding immediate action.
Real-World Case Studies
These examples illustrate the insidious nature of the “check your messages” scam, demonstrating how seemingly harmless prompts can lead to significant financial or emotional harm.
- Case 1: The Phony Prize Alert: A victim received a text message claiming they had won a large prize in a contest they didn’t enter. The message directed them to a website mimicking a legitimate prize-claiming portal. This site asked for personal details, including banking information, to “verify” the winnings. The victim, eager to claim the prize, provided the requested information. The scammer then drained the victim’s bank account.
This scam was successful due to the lure of a large prize, coupled with the urgency created by the need to act quickly to claim the reward.
- Case 2: The Spoofed Account Notification: A user received a text message claiming their social media account had been compromised. The message contained a link to a fake login page. The victim, fearing account loss, clicked the link. The page collected their login credentials. The scammers subsequently gained access to the victim’s account and used it for malicious activities, including sending fraudulent messages to the victim’s contacts.
- Case 3: The Urgent Delivery Alert: A victim received a text message indicating a package delivery was delayed due to an issue with their address. The message included a link to a website. The website mimicked a legitimate shipping company’s page and requested the victim to update their payment details for the delivery. The victim, anxious about missing their delivery, clicked the link and provided their payment information.
The scammers then used this information to make unauthorized purchases. The urgency of the delivery issue and the need to update the payment information successfully enticed the victim to comply.
Summary Table of Scams
| Case | Platform | Method | Outcome |
|---|---|---|---|
| Case 1 | SMS | Prize alert; fake website | Financial loss; drained bank account |
| Case 2 | SMS | Spoofed account notification; fake login page | Compromised account; malicious activities |
| Case 3 | SMS | Urgent delivery alert; fake shipping site | Financial loss; unauthorized purchases |
Closure
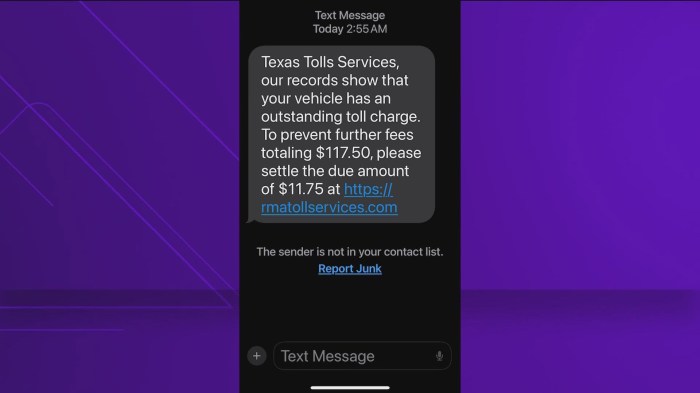
In conclusion, the “check your messages” scam is a serious threat that demands vigilance and proactive measures. By understanding the tactics, recognizing the vulnerabilities, and employing preventative strategies, we can collectively combat this rising trend. This guide offers valuable insights and practical advice to empower individuals and organizations to protect themselves and their loved ones from falling victim to these deceptive schemes.
Remember to be cautious, verify information thoroughly, and report suspicious messages to appropriate authorities.