Amazon Alexa privacy hub security voice recordings echo devices are increasingly important as our reliance on voice-activated technology grows. This comprehensive look explores Amazon’s privacy policies, the security of Echo devices, and how users can manage their voice recordings. We’ll delve into the functionality of the Privacy Hub, analyze the potential impacts on personal data, and examine industry best practices.
We’ll also consider alternative voice control systems to assess the trade-offs between convenience and privacy.
The core issue revolves around the balance between convenience and the protection of personal data. Amazon’s Alexa ecosystem offers seamless voice control, but users must understand the data collection process and their rights to manage that data. This article aims to equip readers with the knowledge to make informed decisions about using Alexa devices while safeguarding their privacy.
Overview of Amazon Alexa Privacy

Amazon’s Alexa devices are designed to be helpful assistants, but their operation involves collecting user data. Understanding Amazon’s privacy policy is crucial for responsible use of these devices. This overview provides a comprehensive look at data collection, user access, and data management procedures.Amazon’s approach to privacy centers on user consent and the idea of providing a valuable service in exchange for some data collection.
Their stated goal is to enhance user experience through personalized interactions and tailored services. This data, however, is collected and used in accordance with their privacy policy, which is constantly updated and accessible on their website.
Ever wondered about the security of your Amazon Alexa devices and voice recordings? Privacy hubs and security measures are important, but if you’re also interested in catching the stunning aurora borealis during a G4 geomagnetic storm, check out this guide on how to watch the celestial show: how to watch aurora borealis g4 geomagnetic storm noaa. Knowing how to best view this natural light display can help you focus on appreciating nature’s beauty, which is a perfect way to think about how your voice recordings are handled by the devices.
Ultimately, understanding your privacy settings and security options for your Alexa devices is key.
Amazon Alexa Data Collection
Alexa devices gather various types of data to enhance their functionality. This includes voice recordings, device usage patterns, location data (if enabled), and information from linked accounts like Amazon shopping history. The specifics of data collection depend on the user’s settings and the specific Alexa commands used.
User Access to Data
Users have varying levels of access to the data collected by their Alexa devices. Users can review and manage their voice recordings, and other data through their Amazon account. The degree of control over the data varies based on the specific type of information and the user’s privacy settings. Users can adjust privacy settings to limit the collection of certain data types.
Data Review and Management Procedures
Amazon provides several ways for users to review and manage their data. These methods include accessing their account dashboard to view and delete voice recordings, adjusting privacy settings, and opting out of certain data collection practices. Clear instructions on these procedures are available within the Amazon Alexa privacy policy. Furthermore, users can contact Amazon support for assistance with specific requests or concerns related to their data.
Comparison of Smart Speaker Privacy Policies
| Brand | Voice Recording Policy | Data Usage Policy | Data Security Measures ||—|—|—|—|| Amazon Alexa | Voice recordings are stored and used for improving Alexa’s functionality and providing personalized services. | Data is used to tailor advertising, product recommendations, and other services. | Amazon employs encryption and security protocols to protect user data. || Google Assistant | Voice recordings are used to improve Google Assistant’s services and provide personalized experiences.
| Data may be used for targeted advertising and personalized services. | Google uses encryption and security protocols to protect user data. || Apple HomePod | Voice recordings are stored and processed to enhance the HomePod’s functionality. | Data is used for tailored content and service recommendations. | Apple employs encryption and security protocols to protect user data.
|
Security of Echo Devices
Echo devices, while convenient, introduce potential security vulnerabilities. Understanding these risks and implementing appropriate security measures is crucial for protecting user data and privacy. Proper configuration and vigilance can significantly mitigate these risks, ensuring the safe operation of these smart home assistants.
Worried about Amazon Alexa’s privacy hub and security surrounding voice recordings on Echo devices? While those concerns are valid, consider how much easier your daily tasks could be with features like the new Microsoft Edge sidebar widgets, allowing quick access to search, email, and even recipes. microsoft edge sidebar widgets search email recipes can streamline your workflow.
Ultimately, responsible use of voice assistants like Alexa, along with awareness of privacy settings, remains key.
Potential Security Vulnerabilities, Amazon alexa privacy hub security voice recordings echo devices
Echo devices, like any internet-connected device, are susceptible to various security vulnerabilities. These vulnerabilities can stem from weaknesses in the device’s design, software, or the network it connects to. Weak passwords, outdated software, and compromised network configurations can expose devices to unauthorized access. Furthermore, the reliance on voice recordings for functionality presents a unique set of potential security concerns.
Securing Echo Devices
Implementing robust security measures is essential for safeguarding Echo devices. This involves multiple layers of protection, from device-level configurations to network-wide security protocols.
- Strong Passwords: Employing strong, unique passwords for your Amazon account and Wi-Fi network is fundamental. Avoid using easily guessable passwords, such as common words or personal information. Utilizing a password manager can assist in creating and remembering complex passwords. This practice significantly reduces the risk of unauthorized access to your account and the devices connected to your network.
- Regular Software Updates: Keeping the software on your Echo devices up-to-date is vital. Updates often include security patches that address known vulnerabilities. Failing to update software leaves devices susceptible to exploits and compromises. Regularly checking for and installing updates mitigates these risks.
- Secure Network Configuration: Ensure your Wi-Fi network utilizes strong encryption, such as WPA2 or WPA3. Changing the default network name and password, and using a strong encryption protocol, is essential for preventing unauthorized access. Utilizing a Virtual Private Network (VPN) can further enhance security by encrypting your internet traffic.
Protecting Against Unauthorized Access to Voice Recordings
User privacy is paramount, and protecting voice recordings from unauthorized access is a critical concern. Several steps can be taken to ensure that recordings are not accessible without permission.
- Review and Adjust Privacy Settings: Regularly review and adjust privacy settings on your Echo devices. Disable features or functionalities that you do not need or use. Understanding and controlling the recording process is essential to minimize risks.
- Delete Unnecessary Recordings: Regularly delete voice recordings that are no longer needed. This reduces the potential exposure of sensitive information to unauthorized parties. This practice minimizes the volume of data that could be compromised.
- Enable Two-Factor Authentication: Enabling two-factor authentication for your Amazon account adds an extra layer of security. This process requires a secondary verification step beyond a password, significantly enhancing the protection of your account and connected devices.
Role of Encryption in Safeguarding User Data
Encryption plays a critical role in safeguarding user data. Encryption transforms data into an unreadable format, rendering it inaccessible to unauthorized parties.
Data encryption converts readable data into an unreadable format, making it inaccessible to unauthorized parties.
The strength of encryption is directly correlated with its key length and the algorithm used. Stronger encryption algorithms are more resistant to attacks. Amazon employs encryption protocols to protect user data during transmission and storage. However, users also have a role to play in ensuring data security.
Security Measures and Effectiveness
The following table Artikels various security measures and their effectiveness in protecting Echo devices and user data.
| Security Measure | Effectiveness |
|---|---|
| Strong Passwords | High |
| Regular Software Updates | High |
| Secure Network Configuration | High |
| Review and Adjust Privacy Settings | Medium |
| Delete Unnecessary Recordings | High |
| Two-Factor Authentication | High |
User Experience and Voice Recordings
Interacting with Amazon Echo devices often involves voice commands, and understanding how voice recordings are handled is crucial for a positive user experience. Users need clear and consistent ways to manage their recordings, ensuring their privacy is respected. This section dives into the specifics of how users interact with and control voice recordings on their Echo devices.Echo devices are designed for hands-free interaction, and voice recordings are integral to this function.
From simple requests like setting timers to more complex tasks like playing music or making calls, voice commands are the primary method of interaction. The experience hinges on a seamless and secure process for managing these recordings.
Interaction with Voice Recordings
Users interact with voice recordings primarily through voice commands. A user might ask for a specific recording, request to delete a recording, or check for the existence of a particular recording. The system facilitates these interactions through a user-friendly interface, either through the Alexa app or through specific voice commands.
Storage and Management of Voice Recordings
Amazon stores voice recordings securely, typically encrypted, in accordance with their privacy policies. The storage location and duration depend on user settings and privacy preferences. For example, recordings might be stored for a set period, or indefinitely if the user opts for retention.
Controlling Access to Recordings
Users have control over access to their recordings through the Alexa app. This includes options for viewing, deleting, and managing the retention period for recordings. They can choose to review recordings related to specific devices, dates, or types of interactions.
Deleting Voice Recordings
Users can delete their voice recordings individually or in bulk through the Alexa app. The process is straightforward, allowing users to selectively erase recordings or clear entire categories of recordings. For example, a user might delete recordings from a specific interaction or choose to delete all recordings from a particular device.
Managing Voice Recordings
The following table Artikels the steps for accessing and managing voice recordings. Note that steps may vary slightly based on the specific Alexa app version.
| Action | Steps |
|---|---|
| View Voice Recordings | Open the Alexa app. Go to “Your Account.” Select “Voice History” or a similar option. Select the desired date range or device. |
| Delete Individual Recordings | Locate the specific recording in the Voice History. Select the recording and choose the “Delete” option. |
| Delete Multiple Recordings | Select the desired recordings within the Voice History. Use the bulk delete function (often indicated by a “select all” or similar option). |
| Adjust Retention Settings | Navigate to “Settings” in the Alexa app. Find the section for voice history retention and adjust the settings as desired. |
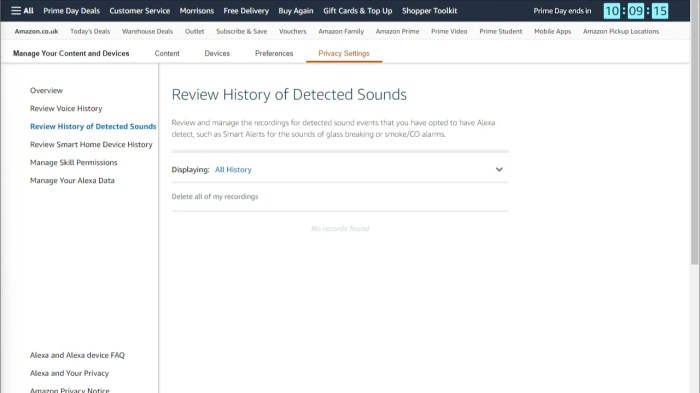
Privacy Hub and its Functionality
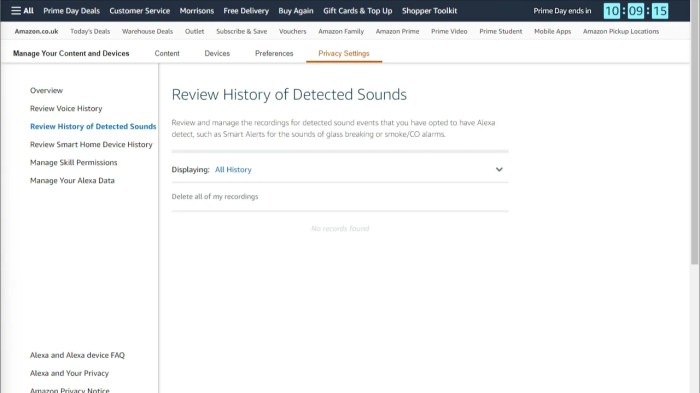
The Amazon Alexa Privacy Hub is a crucial tool for users to take control of their voice data collected by Amazon Echo devices. It provides a centralized dashboard to manage recordings, access privacy settings, and understand how their data is used. This empowers users to actively shape their digital experience and maintain control over their personal information.The Privacy Hub is designed to be a user-friendly interface, allowing for straightforward management of voice recordings and privacy settings.
It goes beyond simply acknowledging data collection; it provides a way for users to actively engage with and oversee their data. This proactive approach to privacy management is a key feature distinguishing the Privacy Hub from many other similar tools.
Managing Voice Recordings
The Privacy Hub allows users to review and delete voice recordings stored on their Amazon Echo devices. This includes the ability to filter recordings based on criteria such as date, time, or even s. This feature provides a level of granularity in data management that goes beyond simple on/off toggles. Users can effectively manage their voice data to ensure only relevant recordings are kept.
Privacy Settings and Controls
The Privacy Hub offers a comprehensive set of controls for managing various privacy settings. These settings extend beyond simply deleting recordings, and encompass broader aspects of data usage. Users can adjust their preferences for which data is collected and how it is used. This flexibility is a key element in ensuring user control.
Data Usage and Transparency
The Privacy Hub provides insights into how voice data is used by Amazon. This transparency allows users to understand the processes and technologies behind the operation of their Echo devices. This approach promotes trust by empowering users with the knowledge needed to make informed decisions.
Features Summary
| Feature | Description |
|---|---|
| Voice Recording Management | Review, filter, and delete voice recordings based on criteria like date, time, or s. |
| Privacy Settings Adjustment | Adjust preferences for data collection and usage, extending beyond recording deletion. |
| Data Usage Transparency | Understand how voice data is used by Amazon, including the processes and technologies involved. |
Comparison with Similar Tools
The Amazon Alexa Privacy Hub offers a user-friendly platform for managing voice data, similar to tools provided by other companies. However, the specific features, including the ability to filter recordings, provide a level of granular control not always present in competing products. The hub’s strength lies in its seamless integration with the Amazon ecosystem, offering a consistent experience for users managing their data across multiple devices.
Impact on Personal Data
The collection of voice recordings by Amazon Alexa devices raises significant concerns about the impact on personal data. This data, while potentially useful for enhancing user experience and improving services, also carries the risk of misuse and breaches of privacy. Understanding the potential impacts, uses, and misuses of these recordings is crucial for informed decision-making regarding the use of such technology.The potential uses and misuses of voice recordings are multifaceted, ranging from convenient features to potentially harmful outcomes.
A deep dive into the ethical considerations and legal implications surrounding this data collection is necessary for users to fully understand the implications.
Potential Uses of Voice Recordings
Voice recordings can be employed for a variety of purposes, offering benefits for users. These applications span numerous areas, from enhancing user experience to providing valuable data for research and development.
- Personalized Recommendations: Voice recordings can be analyzed to understand user preferences and habits. This allows for tailored recommendations for music, movies, products, and more, enhancing the user experience. This data helps tailor recommendations to individual needs, creating a more engaging and personalized experience for the user.
- Improved Product Development: The analysis of voice recordings can provide valuable insights into user needs and pain points. This information can be used to refine product features, address user concerns, and improve overall product quality. This continuous feedback loop is vital for companies seeking to innovate and create products that truly meet consumer needs.
- Enhanced Customer Service: Voice recordings can be utilized to improve customer service interactions. Analyzing conversations can help identify areas for improvement in customer service protocols, leading to better support and resolution of issues.
Potential Misuses of Voice Recordings
While voice recordings offer potential benefits, the possibility of misuse also exists. This includes situations where the data is mishandled, exploited, or used for malicious purposes. The potential for privacy violations and misuse is significant.
- Data Breaches: If security measures are inadequate, voice recordings could be compromised, leading to unauthorized access and potential misuse of personal data. Security breaches can expose sensitive information and compromise the trust between users and service providers.
- Targeted Advertising: Detailed analysis of voice recordings could allow for highly targeted advertising, potentially influencing consumer choices in inappropriate ways. This raises concerns about manipulation and undue influence in purchasing decisions.
- Privacy Violations: Voice recordings may contain sensitive information about personal preferences, financial details, or health concerns. Without proper safeguards, these recordings could be misused, leading to privacy violations and harm to individuals.
Legal Implications of Voice Recordings
The legal landscape surrounding voice recordings and privacy is complex and varies by jurisdiction. Understanding these regulations is essential for both users and companies handling voice data.
- Data Protection Laws: Regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) mandate the protection of personal data. These regulations often specify requirements for obtaining consent, data security, and data usage limitations.
- Privacy Laws: Various countries have specific laws related to audio recording. These laws address the recording of conversations, consent requirements, and potential penalties for violations.
Ethical Considerations
Ethical considerations play a significant role in the use of voice recordings. These considerations address the moral implications of collecting, storing, and utilizing this data.
- Informed Consent: Users should be fully informed about the collection and use of their voice recordings and provided with explicit consent for specific applications. Transparency is essential for building trust and avoiding misuse.
- Data Security: Robust security measures are crucial to protect voice recordings from unauthorized access, breaches, and misuse. Strong encryption and access controls are critical components.
- Data Minimization: Only the necessary data should be collected to achieve specific objectives. Collecting excessive data or data unrelated to intended use should be avoided.
Examples of Voice Recording Usage
The following table demonstrates various potential uses of voice recordings collected by devices like Amazon Alexa.
| Purpose | Example Use Case |
|---|---|
| Personalization | Alexa recommends music based on past listening habits and voice interactions. |
| Customer Service | Analyzing customer service calls to identify areas for improvement in handling customer inquiries. |
| Product Development | Gathering user feedback on product features through voice interactions and surveys. |
| Targeted Advertising | Displaying advertisements relevant to the user’s interests, based on the information extracted from their voice recordings. |
Industry Best Practices for Privacy and Security: Amazon Alexa Privacy Hub Security Voice Recordings Echo Devices
The proliferation of smart devices like Amazon Echo raises crucial questions about data privacy and security. These devices collect vast amounts of user data, including voice recordings, and understanding industry best practices is paramount for responsible data handling. Companies must balance the benefits of these technologies with the fundamental right to privacy.Companies must establish robust safeguards to protect user data, and this involves adhering to industry standards, regulations, and ethical considerations.
This includes transparent data collection policies, secure storage practices, and user-friendly controls for data access and management. Ultimately, trust in these technologies hinges on demonstrable commitment to privacy and security.
Handling User Voice Recordings
Voice recordings are a core feature of smart speakers, but their collection and usage must be approached with meticulous care. Transparency and user control are essential. Clear policies detailing when, how, and why recordings are collected are crucial for building trust. Users should have the ability to review, delete, and access their recordings. This proactive approach to data management fosters user confidence and minimizes potential privacy concerns.
Secure storage of recordings is equally vital. Employing encryption and access controls helps to prevent unauthorized access and data breaches.
Industry Standards and Regulations
Numerous industry standards and regulations govern data privacy, particularly concerning voice recordings. The General Data Protection Regulation (GDPR) in Europe and similar laws worldwide mandate that companies collect and process personal data lawfully, fairly, and transparently. These regulations emphasize user rights regarding their data, including the right to access, rectification, and erasure. Companies should adhere to these standards to comply with legal requirements and maintain user trust.
Furthermore, companies should consider industry best practices like those Artikeld by the Electronic Frontier Foundation (EFF) and similar organizations, which focus on user privacy and digital rights.
Steps Taken by Other Companies
Several companies are proactively addressing privacy and security concerns in the smart speaker industry. For instance, Apple’s approach to voice assistant technology emphasizes user control and data minimization. They offer granular controls over data collection and processing, allowing users to manage their data preferences. Similarly, Google’s voice assistant incorporates features like end-to-end encryption to enhance data security.
I’ve been thinking a lot about the security of voice recordings on Amazon Echo devices lately, and the privacy implications of the Alexa privacy hub. It got me wondering about the potential for similar issues in other sectors. For example, recent news about Airbnb discrimination tests in California raises important questions about how companies collect and use data.
Airbnb discrimination tests in California highlight the need for transparency and responsible data handling. Ultimately, the security of our voice data, whether from smart speakers or other platforms, deserves careful consideration and robust safeguards.
These examples demonstrate that proactive measures can enhance user trust and ensure responsible data handling. Many other companies are also taking steps towards better privacy practices, often in response to public scrutiny and evolving regulatory landscapes.
Summary of Industry Best Practices
| Category | Best Practice |
|---|---|
| Data Collection | Explicit consent for recording, clear and concise data collection policies. |
| Data Storage | Secure storage methods, including encryption and access controls. |
| Data Access and Control | User-friendly interfaces for managing recordings and data preferences. |
| Transparency | Open communication about data usage and handling procedures. |
Comparison of Data Security Approaches
Different smart speaker manufacturers employ varied approaches to data security. Some prioritize end-to-end encryption to protect data during transmission, while others focus on robust server-side security measures. The effectiveness of each approach depends on the specific implementation and the potential vulnerabilities of each system. The choice between these approaches often involves trade-offs between security, performance, and user experience.
Understanding the trade-offs is critical in designing effective data security strategies for smart speakers. For example, end-to-end encryption ensures data privacy during transmission, but might not be as effective against sophisticated attacks on the device itself. Server-side security measures, on the other hand, can be more robust in defending against such attacks but might expose more data during storage and processing.
Alternative Approaches to Voice Control
Voice control, while convenient, raises privacy concerns. Alternative approaches to voice control are emerging, offering various levels of user experience and data collection practices. These alternatives aim to strike a balance between user convenience and data security.Alternative systems offer different ways to interact with devices without relying on continuous voice recordings. This allows for a shift in the data collection model, potentially reducing the risk of unauthorized access and misuse of personal information.
By exploring these alternatives, we can better understand the trade-offs between user convenience and data privacy.
Gesture and Touch-Based Control
Gesture and touch-based interfaces offer a way to interact with devices without relying on voice commands. These systems often collect minimal data, primarily related to the physical actions themselves, not the content of the interaction.Examples include smartwatches that use gestures for controlling smart home devices or touchscreens for navigation and input. This approach generally requires less data collection and processing than voice-based systems.
The trade-off is that gesture-based controls might not be as intuitive or flexible as voice control. They also might not be as accessible to all users.
Visual Command Interfaces
Visual command interfaces, often paired with cameras, allow users to interact with devices through visual commands. These systems are less reliant on voice and, instead, interpret visual cues, such as hand gestures or text input. These systems may capture images or videos related to the commands, but the data collected might be limited to what’s directly relevant to the action.One example is a smart TV that allows users to control playback using hand gestures, reducing the need for voice commands.
Another example is a system that uses visual cues to navigate a smart home system. The advantages include greater privacy and security as voice data isn’t collected. The disadvantage is that these systems might require specialized hardware and software, and the user experience may not be as intuitive as voice control.
Pre-programmed Actions and Macros
Pre-programmed actions and macros enable users to automate tasks without continuous voice input. Users create pre-defined sequences of actions or commands that are triggered by specific inputs, such as button presses or scheduled times. These systems rely on pre-configured data and do not collect ongoing voice data.An example is a smart light system that automatically adjusts brightness based on time of day, or a home security system that triggers pre-programmed responses based on sensor input.
These systems eliminate the need for continuous voice recognition, reducing data collection and the associated privacy concerns. However, they might limit flexibility and require more upfront setup and configuration than voice-based systems.
Comparison of Voice Control Systems and Privacy Policies
| Voice Control System | Data Collection Practices | Privacy Policy Considerations | User Experience |
|---|---|---|---|
| Voice-based (Alexa, Google Assistant) | Continuous voice recording and analysis | Potential for extensive data collection and storage | Highly intuitive and flexible |
| Gesture-based (Smartwatches, Touchscreens) | Limited data collection; primarily physical actions | Reduced data collection and storage | Potentially less intuitive |
| Visual Command (Smart TVs, Cameras) | Images or videos related to commands | Privacy concerns about image capture and analysis | Potentially intuitive with visual cues |
| Pre-programmed Actions (Macros) | No continuous data collection | Minimal data collection, focused on pre-defined actions | Limited flexibility; requires upfront setup |
Outcome Summary
In conclusion, navigating the world of voice-activated technology requires a proactive approach to privacy and security. Understanding Amazon’s policies, the security measures surrounding Echo devices, and the tools available for managing voice recordings empowers users to maintain control over their personal data. By considering alternative systems and industry best practices, we can all make more informed choices when integrating voice control into our daily lives.
Ultimately, the conversation surrounding Alexa privacy, security, and voice recordings underscores the ongoing need for transparency and user empowerment in the age of technology.