Adversary tricks CrowdStrike treats are a constant cybersecurity battleground. These are the sophisticated tactics employed by malicious actors, ranging from social engineering to complex malware deployments. CrowdStrike’s response is a multi-layered approach, utilizing threat intelligence and advanced detection techniques to identify and neutralize these threats. This exploration dives deep into the world of adversary tricks, CrowdStrike’s strategies, and real-world examples.
Understanding the motivations and methods behind these attacks is crucial for organizations to proactively bolster their security posture. The detailed analysis will shed light on the intricate ways adversaries operate and how CrowdStrike’s solutions provide effective countermeasures.
Introduction to Adversary Tricks
Adversary tricks, in the realm of cybersecurity, encompass a wide range of malicious techniques employed by threat actors to compromise systems, steal data, or disrupt operations. These techniques leverage vulnerabilities in technology, human psychology, and organizational processes. Understanding these tricks is crucial for developing effective defenses and mitigating potential risks.These tricks are often employed by individuals or groups motivated by financial gain, espionage, political agendas, or simply to cause disruption.
The motivations behind adversary tricks can be varied and complex, but the overarching goal remains the same: exploitation of vulnerabilities for malicious purposes.
Categories of Adversary Tricks
Adversary tricks can be broadly categorized into several key areas. These categories, while not mutually exclusive, offer a framework for understanding the diverse methods used to gain unauthorized access or inflict harm.
- Social Engineering: This involves manipulating individuals to gain access to sensitive information or systems. Techniques like phishing, pretexting, and baiting exploit human psychology, often relying on trust and persuasion to trick victims into divulging confidential details or executing harmful actions.
- Malware: This encompasses various types of malicious software designed to infiltrate systems and perform malicious actions. Examples include viruses, worms, Trojans, ransomware, and spyware, each with distinct functionalities and methods of operation.
- Phishing: A specific type of social engineering attack, phishing involves sending fraudulent communications (often emails) that appear legitimate to trick recipients into revealing sensitive information, such as usernames, passwords, or credit card details.
- Denial-of-Service (DoS) Attacks: These attacks aim to overwhelm a system or service with traffic, rendering it unavailable to legitimate users. DoS attacks can be launched through various methods, including flooding the target with requests or exploiting vulnerabilities in the target’s infrastructure.
Comparative Analysis of Adversary Tricks
Understanding the nuances of each trick is essential for developing effective countermeasures. The table below provides a comparative overview of different types of adversary tricks, highlighting their descriptions, tactics, and potential impacts.
| Description | Tactics | Potential Impact |
|---|---|---|
| Social Engineering | Exploiting human psychology; manipulation, pretexting, baiting; often involves impersonation or creating false urgency. | Data breaches, unauthorized access to systems, financial losses, reputational damage. Example: A threat actor posing as a bank representative to trick a user into revealing their account information. |
| Malware | Infects systems through various means; can perform a wide range of malicious activities, including data theft, system damage, and unauthorized access. | Data breaches, system compromise, financial losses, operational disruption. Example: A malicious program encrypting a victim’s files and demanding a ransom to decrypt them (ransomware). |
| Phishing | Sending deceptive emails or messages that appear legitimate; often impersonating trusted entities to gain access to sensitive information. | Data breaches, identity theft, financial fraud, account compromise. Example: A phishing email pretending to be from a legitimate online retailer, prompting users to update their login credentials on a fake website. |
| DoS Attacks | Overwhelms a system with traffic; exploits system vulnerabilities to overload resources. | Service disruption, downtime, loss of revenue, reputational damage. Example: A hacker launching a flood of requests against a website, making it inaccessible to legitimate users. |
CrowdStrike’s Approach to Threat Hunting
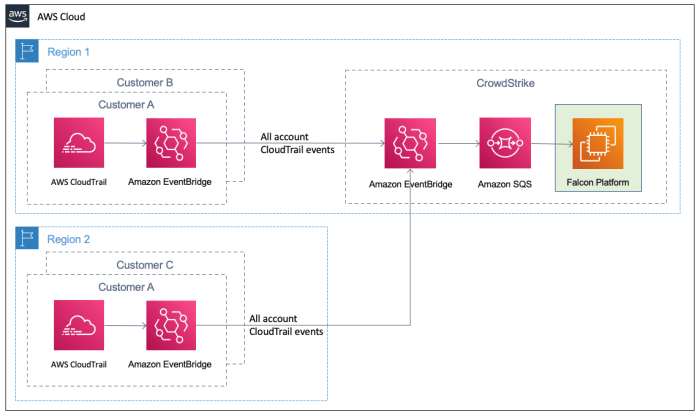
CrowdStrike takes a proactive and comprehensive approach to threat hunting, focusing on identifying and responding to sophisticated adversary tactics. This proactive approach distinguishes CrowdStrike from reactive security measures, allowing organizations to stay ahead of evolving threats. Their strategy revolves around a robust combination of threat intelligence, advanced detection capabilities, and skilled analysts.CrowdStrike’s approach emphasizes a deep understanding of adversary methodologies, enabling them to anticipate and counter evolving attack patterns.
This approach goes beyond simply detecting intrusions; it aims to understand the motivations, techniques, and objectives of the attackers. This proactive understanding allows for better prevention and response strategies.
CrowdStrike’s Threat Intelligence Utilization
CrowdStrike leverages a vast network of threat intelligence sources to build a comprehensive picture of the adversary landscape. This includes publicly available information, internal threat data, and insights from their extensive security operations center (SOC). This aggregated data is then analyzed to identify emerging patterns and trends in malicious activity. By understanding the context and intent behind the threats, CrowdStrike can effectively anticipate and mitigate potential risks.
CrowdStrike’s TTP Analysis Methodology
CrowdStrike employs sophisticated methods for analyzing adversary tactics, techniques, and procedures (TTPs). This includes techniques like behavioral analysis, correlating events across multiple data sources, and identifying anomalies in system activity. By examining the intricate details of each adversary campaign, CrowdStrike can identify subtle indicators of malicious activity that might be missed by basic security tools. These insights are used to develop more effective preventative measures and enhance the organization’s defensive posture.
CrowdStrike’s Detection and Response Tools, Adversary tricks crowdstrike treats
CrowdStrike’s suite of tools provides a comprehensive framework for detecting and responding to adversary tricks. These tools enable proactive threat hunting, allowing security teams to identify and neutralize threats before they cause significant damage. Their integrated platform offers a unified view of security events, enabling analysts to quickly identify and investigate potential threats.
| Tool Name | Function | Example Use Case |
|---|---|---|
| Falcon Platform | Provides a centralized platform for threat detection, response, and intelligence analysis. | Centralized view of all security events across the enterprise, enabling faster threat response. |
| Falcon Insight | Provides threat intelligence and data enrichment to contextualize security events. | Identifying the malicious intent behind a series of suspicious network connections. |
| Falcon Prevent | Offers proactive prevention against known and unknown threats. | Blocking malicious files and processes based on real-time threat intelligence. |
| CrowdStrike Threat Graph | Visualizes the relationships between threats and threat actors. | Identifying the links between different malware samples and threat groups, providing a comprehensive threat landscape view. |
Specific Adversary Tricks Targeted by CrowdStrike
CrowdStrike consistently identifies and analyzes sophisticated adversary tactics, techniques, and procedures (TTPs). Understanding these methods allows for proactive threat detection and mitigation. This deep dive explores specific adversary tricks, the techniques employed, and real-world attack examples.CrowdStrike’s threat intelligence feeds are crucial in identifying these adversary tricks. Their analysis allows for the development of effective countermeasures to defend against emerging threats.
This understanding of malicious actors’ approaches helps organizations strengthen their security posture and reduce the risk of successful attacks.
Common Adversary Evasion Techniques
Adversaries frequently employ techniques to evade detection, such as obfuscating malicious code and exploiting system vulnerabilities. These techniques aim to bypass security controls and achieve their objectives without being noticed. Effective detection requires recognizing these evasion methods and understanding the tools and strategies behind them.
- Fileless Attacks: These attacks rely on leveraging existing legitimate applications and system tools to execute malicious code without creating or modifying files. This method evades traditional signature-based detection by circumventing file-scanning tools. For example, PowerShell scripts are frequently used in fileless attacks to execute malicious commands and establish remote access connections. Attackers often modify these scripts to avoid detection by security tools.
- Credential Access: Compromising credentials is a common objective for adversaries. Techniques include phishing campaigns, exploiting vulnerabilities in authentication systems, and stealing credentials from compromised systems. This allows attackers to gain unauthorized access to sensitive data and systems. Examples include spear phishing emails designed to trick users into revealing their login credentials, or exploiting vulnerabilities in poorly configured Active Directory environments to gain domain admin privileges.
- Exploiting Software Vulnerabilities: Adversaries often seek and exploit known and unknown vulnerabilities in software applications to gain unauthorized access. They use these vulnerabilities to execute malicious code, install malware, and gain control over the system. This requires proactive vulnerability management and patching of software.
Adversary Tricks and CrowdStrike’s Countermeasures
CrowdStrike’s threat intelligence and proactive approach to threat hunting allow for the development of countermeasures tailored to specific adversary tricks. This includes leveraging machine learning to identify and respond to emerging threats. This proactive approach is critical for staying ahead of attackers.
| Trick Type | Description | CrowdStrike’s Response |
|---|---|---|
| Fileless Attacks | Leveraging legitimate tools to execute malicious code without creating or modifying files. | CrowdStrike Falcon’s proactive detection using behavioral analysis and machine learning to identify suspicious activities in legitimate processes. |
| Credential Access | Gaining unauthorized access by compromising user credentials through phishing or exploiting authentication vulnerabilities. | CrowdStrike Falcon’s email security solutions to detect and block malicious emails, and security awareness training for users to identify and avoid phishing attempts. |
| Exploiting Software Vulnerabilities | Taking advantage of known or unknown vulnerabilities in software to gain unauthorized access. | CrowdStrike Falcon’s proactive vulnerability management solutions, including real-time threat intelligence feeds to identify and patch vulnerabilities in a timely manner. |
Case Studies of CrowdStrike’s Successes
CrowdStrike’s proactive threat hunting and advanced incident response capabilities have consistently proven effective in mitigating sophisticated cyberattacks. This section delves into specific case studies showcasing how CrowdStrike’s techniques have thwarted adversary tricks, leading to successful incident containment and minimized damage. These examples highlight the value of their approach in safeguarding organizations from evolving threats.
Documented Cases of Successful Mitigation
CrowdStrike has a track record of successfully detecting and responding to various sophisticated adversary tactics. These cases often involve complex attacks that leverage multiple techniques to evade detection. By analyzing these instances, organizations can learn valuable lessons about identifying and neutralizing advanced threats.
Case Study 1: The “Cobalt Strike” Campaign
In this instance, a targeted organization experienced a breach where attackers utilized Cobalt Strike, a widely recognized and sophisticated penetration testing tool, to gain initial access. CrowdStrike’s threat intelligence and advanced hunting capabilities detected suspicious activity related to Cobalt Strike command and control communication. The team quickly identified and isolated compromised systems, preventing lateral movement and data exfiltration.
Case Study 2: The “Ransomware” Attack
A different organization faced a ransomware attack that involved a novel encryption technique. CrowdStrike’s threat hunters identified the specific malware strain and its associated command-and-control infrastructure. By deploying proactive containment measures, CrowdStrike was able to prevent the complete encryption of critical data and contain the attack, thereby minimizing financial losses. The team further analyzed the ransomware’s infrastructure, contributing to industry-wide threat intelligence sharing and enhancing detection mechanisms for future attacks.
Case Study 3: The “Supply Chain Compromise”
A vulnerability in a widely used software library enabled an adversary to compromise the supply chain of a software vendor. CrowdStrike’s proactive threat intelligence gathering identified the compromised library and the attacker’s methods. This allowed the company to quickly alert its customers, providing timely mitigation steps and preventing further exploitation.
CrowdStrike, known for its robust security, often highlights the sneaky tactics adversaries use. It’s a constant battle, and these tricks are always evolving. Interestingly, news just broke that Amazon’s Wondery podcast studio is downsizing, laying off workers. This kind of news often reflects the shifting landscape of the tech industry, which in turn might affect the sophistication of the adversary tricks CrowdStrike continues to treat.
Summary Table
| Case Name | Adversary Trick | CrowdStrike’s Response | Outcome |
|---|---|---|---|
| Cobalt Strike Campaign | Utilizing Cobalt Strike for initial access and lateral movement | Identified suspicious activity, isolated compromised systems, prevented lateral movement and data exfiltration | Successful containment, minimal damage |
| Ransomware Attack | Novel encryption technique used in ransomware | Identified malware strain and C2 infrastructure, implemented proactive containment measures | Prevented complete data encryption, minimized financial losses |
| Supply Chain Compromise | Exploiting vulnerability in a widely used software library to compromise supply chain | Identified compromised library and attacker methods, alerted customers, provided mitigation steps | Prevented further exploitation, contained the attack |
Illustrative Examples of Adversary Tricks
Understanding the tactics, techniques, and procedures (TTPs) employed by sophisticated threat actors is crucial for effective threat hunting and incident response. These examples illustrate how adversaries leverage various methods to compromise systems and gain access to sensitive data. By examining these techniques, organizations can better prepare for and defend against these attacks.
CrowdStrike’s got some serious adversary tricks up its sleeve, and it’s not just about protecting your systems. Think about the thrilling gameplay of the Uncharted Nathan Drake Collection on PlayStation 4 uncharted nathan drake collection playstation 4. They’re both about navigating complex challenges and outsmarting foes. Similarly, CrowdStrike’s expertise in cybersecurity relies on understanding and anticipating those tricks, which is crucial in today’s threat landscape.
Sophisticated Phishing Campaign
Sophisticated phishing campaigns often target specific individuals or organizations, leveraging detailed reconnaissance and tailored messages to increase their effectiveness. These campaigns often mimic legitimate communications, employing techniques like spear phishing and whaling. For instance, a campaign might target a specific executive within a company, impersonating a trusted colleague or vendor, sending a seemingly innocuous email with a malicious attachment or link.
The email may include highly specific details gleaned from publicly available information, social media, or previous interactions, making it appear authentic. The goal is to trick the recipient into opening the attachment or clicking the link, which could lead to malware infection or data exfiltration.
Malware Infection Vector
Malware infection vectors can take various forms, exploiting vulnerabilities in software or exploiting human behavior. A common infection vector is a malicious email attachment disguised as a legitimate document. For example, an adversary might send a Word document that, when opened, executes malicious macros that download and install ransomware onto the victim’s system. The adversary trick here is the exploitation of a user’s trust in a seemingly innocuous file type, and their lack of awareness regarding macro-enabled documents.
Another infection vector could be a compromised website hosting a malicious script that infects visitors’ browsers. The trick here is to exploit the victim’s trust in a legitimate website and leverage the browser’s execution capabilities.
CrowdStrike’s got a knack for uncovering sneaky adversary tricks, but the recent news about Facebook and those 400 apps that might have pilfered user logins highlights just how crucial it is to stay vigilant. These security breaches are a stark reminder that even seemingly trusted platforms can be vulnerable, and the need for robust security measures, like the ones CrowdStrike implements, is more critical than ever.
Ultimately, the fight against these digital adversaries is an ongoing one, and we all need to remain aware of the tactics being employed.
Supply Chain Attack
Supply chain attacks target vulnerabilities in the software supply chain, aiming to compromise multiple organizations by infecting a trusted third-party vendor. For example, an adversary might compromise a software development kit (SDK) used by numerous companies. By subtly altering the legitimate SDK, the attacker can introduce malicious code into the software updates deployed by the vendor. When customers update their systems using the compromised SDK, they unwittingly install the malicious code.
The adversary trick in this scenario lies in the trust placed in the vendor and the lack of rigorous security testing and vetting procedures within the supply chain.
Zero-Day Exploit
Zero-day exploits target vulnerabilities in software that are unknown to the software vendor. This lack of knowledge makes patching extremely difficult. The adversary trick here is to discover and exploit a vulnerability before a patch is available, often through reverse engineering or analyzing the software’s source code. For instance, an attacker might discover a previously unknown vulnerability in a widely used operating system, creating a specific exploit to leverage that weakness and gain unauthorized access to systems.
Once the vulnerability is identified, the attacker can develop a malicious payload that exploits the vulnerability, leading to unauthorized access or data theft. The key is the attacker’s ability to leverage the unknown vulnerability before a patch can be developed.
Adversary Trick Mitigation Strategies
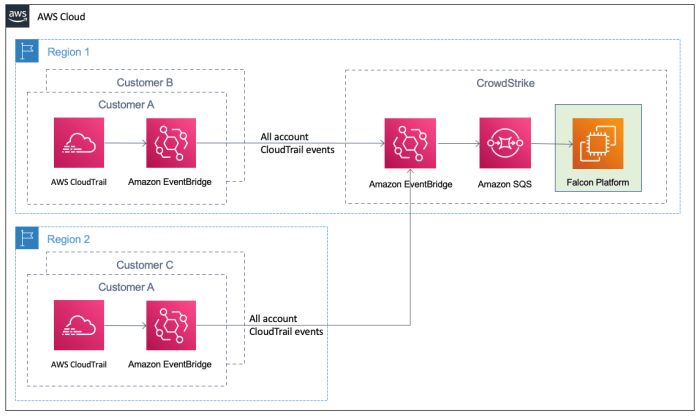
Protecting against sophisticated cyberattacks requires a multi-layered approach that combines robust technical controls with proactive security awareness training. Organizations must understand the tactics, techniques, and procedures (TTPs) employed by adversaries to effectively mitigate risks. A strong defense relies on understanding the adversary’s arsenal and developing countermeasures.A layered security approach is crucial for defending against the diverse range of adversary tricks.
Implementing multiple defense mechanisms makes it significantly harder for attackers to penetrate the system. Each layer acts as a barrier, slowing down the attacker and making their work more difficult, thus buying the organization time to detect and respond to the intrusion. This proactive approach is more effective than simply reacting to attacks after they’ve occurred.
Security Awareness Training Programs
Effective security awareness training is vital for employee education and risk mitigation. Training should focus on identifying phishing attempts, suspicious emails, and other social engineering tactics commonly used by adversaries. By equipping employees with the knowledge and skills to recognize potential threats, organizations significantly reduce the likelihood of successful attacks. A well-structured program should cover various aspects of cybersecurity awareness, from recognizing malicious links to avoiding risky downloads.
This training empowers employees to act as the first line of defense.
- Phishing simulations are crucial for demonstrating the effectiveness of training. Regular simulations allow employees to practice identifying malicious emails and links, reinforcing their knowledge and improving their response time. These simulations should be engaging and realistic to mirror real-world scenarios, making learning more effective and memorable.
- Develop a comprehensive training program that covers various attack vectors. Include modules on social engineering, password security, malware recognition, and safe internet browsing practices. This ensures a holistic approach to security awareness, equipping employees with a broad range of defensive skills.
- Regularly update the training content to reflect emerging threats. The threat landscape is constantly evolving, and training must adapt to address new tactics and techniques used by adversaries. Regular updates ensure employees remain current with the latest security threats.
Technical Controls for Specific Adversary Tricks
Technical controls are essential for protecting against specific adversary tricks. Implementing these controls reduces the attack surface and makes it harder for adversaries to exploit vulnerabilities.
- Implement strong access controls. Restrict access to sensitive data and systems based on the principle of least privilege. This limits the damage that attackers can cause if they gain access to a compromised account.
- Employ intrusion detection and prevention systems (IDS/IPS) to identify and block malicious network traffic. IDS/IPS solutions continuously monitor network activity for suspicious patterns and respond accordingly. This helps to prevent attacks from reaching their target.
- Implement robust endpoint security solutions. Antivirus, anti-malware, and endpoint detection and response (EDR) tools provide protection against malware and malicious software. They help to identify and neutralize threats that try to compromise endpoints.
Building a Layered Security Approach
A layered security approach is essential for creating a robust defense against various adversary tricks. This strategy involves implementing multiple security controls at different points in the system. It provides multiple barriers that make it harder for attackers to compromise the organization.
| Strategy | Description | Implementation Steps |
|---|---|---|
| Strong Access Controls | Restrict access to sensitive data and resources based on the principle of least privilege. | Implement role-based access control (RBAC), multi-factor authentication (MFA), and regular access reviews. |
| Network Segmentation | Divide the network into smaller, isolated segments to limit the impact of a breach. | Use firewalls, virtual LANs (VLANs), and network segmentation tools to isolate critical systems and data. |
| Endpoint Security | Protect endpoints from malware and other threats. | Implement antivirus, anti-malware, and endpoint detection and response (EDR) solutions. |
| Security Information and Event Management (SIEM) | Centralized log management and threat detection. | Implement a SIEM solution to collect and analyze security logs from various sources. |
| Security Awareness Training | Educate employees about security threats and best practices. | Conduct regular training sessions, phishing simulations, and awareness campaigns. |
Evolving Landscape of Adversary Tricks: Adversary Tricks Crowdstrike Treats
The digital threat landscape is constantly shifting, with adversaries adapting their tactics, techniques, and procedures (TTPs) to exploit emerging vulnerabilities. This continuous evolution demands a proactive and adaptable approach to threat hunting, requiring organizations to stay ahead of the curve by understanding the latest trends and tools being employed by malicious actors.The sophistication and frequency of attacks are increasing, driven by readily available tools, readily available resources, and the growth of organized criminal enterprises.
This means organizations need to be prepared for a broader range of threats and not just rely on historical data.
Emerging Trends and Challenges
Adversaries are increasingly leveraging automation and AI to streamline their operations. This allows them to launch more targeted and sophisticated attacks, while also increasing their attack volume. Furthermore, the rise of cloud-based infrastructure presents new attack surfaces and complexities in threat detection. This includes using cloud-based tools and resources for malicious activities, requiring organizations to understand and adapt to these evolving environments.
The growing use of ransomware-as-a-service (RaaS) models also poses a serious threat, enabling less technically skilled actors to launch large-scale attacks.
New Techniques and Tools
Adversaries are increasingly using techniques such as supply chain attacks, where they compromise trusted software or hardware vendors to gain access to multiple targets. The use of “living-off-the-land” techniques, leveraging legitimate system tools, is also growing, making detection more difficult. Furthermore, the development of advanced persistent threats (APTs) that are designed to remain undetected for extended periods requires proactive and persistent threat hunting.
The sophistication of malware is also increasing, with more sophisticated evasive techniques and obfuscation to bypass traditional security tools. These include techniques such as metamorphic malware, which changes its code structure to evade detection.
CrowdStrike’s Adaptability
CrowdStrike employs a multi-layered approach to threat intelligence and response. Their solutions incorporate machine learning algorithms and threat intelligence feeds to detect and respond to emerging threats. This proactive approach helps them stay ahead of the curve by constantly monitoring and analyzing the latest threat data, and providing real-time threat insights to their customers. CrowdStrike’s global threat intelligence team continuously monitors and analyzes new threat activity and patterns.
Significance of Continuous Threat Intelligence and Learning
Staying ahead of evolving adversary tricks requires a commitment to continuous learning and threat intelligence. Threat intelligence allows organizations to understand the motivations, tactics, and procedures of adversaries. This intelligence is vital for building effective security defenses and for developing effective incident response strategies. By continually updating their threat models and security tools, organizations can effectively respond to new attack vectors.
This includes continuous monitoring of the threat landscape, incorporating threat intelligence into security operations, and maintaining a culture of continuous learning and improvement.
Evolving Threat Landscape Summary
“The evolving landscape of adversary tricks demands vigilance and a commitment to continuous learning. Organizations must adapt their security strategies to address new techniques and tools, leveraging threat intelligence to proactively identify and mitigate emerging threats.”
Closing Notes
In conclusion, adversary tricks are constantly evolving, demanding a vigilant and proactive approach to cybersecurity. CrowdStrike’s comprehensive strategies and advanced tools, combined with ongoing threat intelligence, are crucial in mitigating these threats. This exploration highlighted the intricate nature of the threat landscape and the importance of continuous learning and adaptation to maintain a robust security posture.