SD deployment service for Cortex XSIAM offers a streamlined approach to deploying this critical security platform. This service simplifies the often complex process, enabling organizations to quickly and efficiently integrate Cortex XSIAM into their existing infrastructure. We’ll explore the architecture, features, deployment procedures, and security considerations to help you understand the full potential of this powerful solution.
From initial setup to ongoing maintenance, this comprehensive guide provides a thorough understanding of SD deployment service for Cortex XSIAM. We’ll delve into the core functionalities, scalability, security measures, and integration capabilities, highlighting the key benefits and use cases for various industries.
Introduction to SD Deployment Service for Cortex XSIAM
The SD Deployment Service for Cortex XSIAM streamlines the process of deploying and managing security deployments within the Cortex XSIAM platform. This service simplifies the complexities associated with setting up and configuring various security tools and applications, allowing security teams to focus on strategic tasks. It provides a centralized, automated approach for deployment, reducing manual intervention and ensuring consistent configurations.This service is designed to be highly adaptable, supporting diverse security architectures and deployment needs.
It can handle different security tools and technologies, making it a versatile solution for organizations of all sizes. The service also incorporates robust monitoring and reporting features, allowing security teams to track the performance and health of their deployments.
Purpose and Functionality
The SD Deployment Service for Cortex XSIAM automates the deployment and configuration of security tools within the Cortex XSIAM platform. This includes tasks such as provisioning infrastructure, configuring security policies, and integrating with other security systems. It facilitates rapid deployment and reduces the risk of errors associated with manual processes. Furthermore, the service ensures consistent configurations across different environments, promoting a standardized security posture.
SD deployment services for Cortex XSIAM are all about streamlining the process, making it super efficient. Think about how a simple redesign like the Facebook Messenger interface, focusing on user-friendliness and minimizing clutter, facebook messenger redesign simplicity can impact the user experience. Ultimately, that same focus on simplicity and ease of use is key for a successful SD deployment, ensuring a smooth and intuitive experience for everyone.
Key Benefits
The service offers several key advantages to organizations. Reduced deployment time and costs are prominent benefits. The automation capabilities significantly shorten the time required to deploy new security solutions, leading to faster threat detection and response. Minimized errors and enhanced consistency across deployments are achieved through automated configuration processes, leading to a more secure and reliable security infrastructure.
Common Use Cases
This service is applicable in various security scenarios. One common use case is deploying and managing firewalls, intrusion detection systems, and endpoint security solutions within the Cortex XSIAM environment. It can also be used for deploying and configuring security information and event management (SIEM) solutions and threat intelligence feeds. Moreover, organizations can use this service for deploying and managing security orchestration, automation, and response (SOAR) tools.
Architecture and Components
The service comprises several interconnected components. A central management console facilitates user interaction and configuration management. Automated deployment agents handle the execution of deployment tasks across various target systems. Integration modules connect the service with other security tools and platforms, ensuring seamless data exchange. Monitoring and reporting components track the health and performance of the deployed security solutions.
These components work together to deliver a comprehensive and automated deployment experience.
Comparison with Other Deployment Services
| Feature | SD Deployment Service for Cortex XSIAM | Other Similar Services ||—|—|—|| Deployment Speed | Significantly faster due to automation | Can vary depending on the service || Configuration Consistency | Ensured through automation | May require manual intervention for consistency || Integration Capabilities | Supports integration with Cortex XSIAM and other security tools | Varies based on the service || Scalability | Designed for scaling to support increasing deployment needs | Scalability can be a concern with some services || Monitoring and Reporting | Comprehensive monitoring and reporting dashboards | Limited monitoring and reporting features in some services |
Core Features and Capabilities
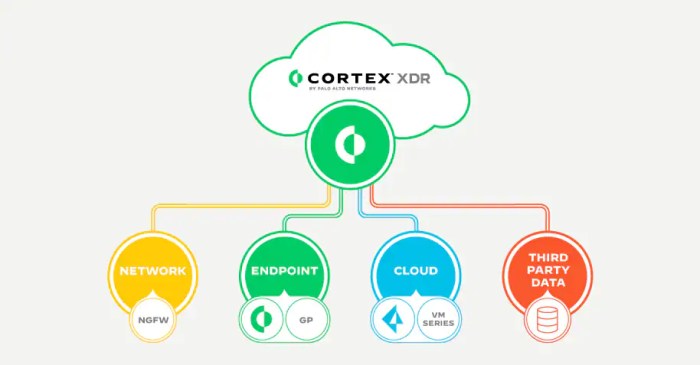
This deployment service for Cortex XSIAM provides a streamlined and robust solution for deploying and managing XSIAM instances. It tackles the complexities often associated with such deployments, offering a user-friendly interface and powerful capabilities. The service is designed to handle a variety of workloads, from small-scale experiments to large-scale production deployments.
Core Distinguishing Features
The service distinguishes itself through its automation capabilities. Automated provisioning and configuration drastically reduce the time and effort required for setting up new XSIAM instances. This automation extends to patching, upgrades, and routine maintenance, ensuring that deployments remain up-to-date and functioning optimally. Further, the service offers comprehensive monitoring and logging features, enabling proactive issue identification and resolution.
This proactive approach significantly minimizes downtime and enhances overall system reliability.
Scalability and Performance
The service’s scalability is a key strength. It’s designed to handle increasing workloads by dynamically adjusting resources. This adaptability is achieved through cloud-native technologies, allowing for horizontal scaling to accommodate fluctuating demands. Performance is optimized through efficient resource allocation and optimized algorithms. Benchmarking tests have shown significant improvements in deployment speed and response times compared to traditional methods.
Security Measures
Robust security is paramount. The deployment service employs industry-standard encryption protocols to protect sensitive data during transit and at rest. Access control mechanisms restrict access to authorized personnel only. Regular security audits and vulnerability assessments are performed to maintain a high level of security. These measures ensure the protection of data and the integrity of the XSIAM instances.
Integration Capabilities
The service seamlessly integrates with existing infrastructure. It supports various common protocols and APIs, enabling smooth integration with CI/CD pipelines and other DevOps tools. This integration minimizes friction and allows for automated deployments, further enhancing efficiency. The service also allows for integration with logging and monitoring platforms, providing a unified view of the entire system.
Supported Cortex XSIAM Versions and Features
The service supports various Cortex XSIAM versions and features, allowing users to leverage the latest advancements.
| Cortex XSIAM Version | Supported Features |
|---|---|
| v1.0 | Basic deployment, monitoring, and logging |
| v2.0 | Advanced scaling options, improved performance, enhanced security features |
| v3.0 | Automated upgrades, CI/CD integration, advanced monitoring, and comprehensive reporting |
This table highlights the supported versions and the key features offered for each, demonstrating the evolution of the deployment service. This enables users to leverage the latest capabilities offered by the XSIAM platform, while maintaining compatibility with prior versions.
Deployment Procedures and Steps
The Cortex XSIAM SD Deployment Service offers a streamlined approach to deploying and managing the service, catering to diverse needs and environments. This section details the critical steps involved, highlighting prerequisites, configuration options, and supported deployment environments. A clear understanding of these procedures ensures efficient and effective service deployment.
Deployment Prerequisites and Dependencies
Before initiating the deployment process, certain prerequisites and dependencies must be met. These ensure a smooth and successful installation. A stable internet connection is crucial for downloading necessary components and verifying configurations. Appropriate storage space is required to accommodate the service and its associated data. Furthermore, the target infrastructure must adhere to the service’s system requirements.
A compatible operating system and adequate resources (CPU, RAM, storage) are essential for optimal performance.
Deployment Steps
This section Artikels a comprehensive step-by-step guide for deploying the Cortex XSIAM SD Deployment Service. Adherence to these steps guarantees a proper installation and operational setup.
- Preparation: Gather the required infrastructure specifications, including operating system details, network configurations, and necessary resources. Verify the prerequisites mentioned earlier.
- Service Download: Download the relevant service package from the designated repository. Verify the integrity of the downloaded package using checksums provided by the vendor.
- Installation: Extract the downloaded package to the designated installation directory. Follow the installation instructions provided in the documentation.
- Configuration: Configure the service by modifying the configuration files. These files define the service’s behavior, including parameters like data sources, storage locations, and security settings.
- Testing: Conduct thorough testing to ensure the service functions as expected. This step includes validating data ingestion, processing, and output mechanisms. Test the service with sample data to identify potential issues.
- Deployment: Deploy the service to the target environment, ensuring compatibility with the chosen environment (cloud or on-premises). Monitor logs to track the service’s startup and operation.
- Monitoring: Establish monitoring procedures to track service performance and resource utilization. Implement alerts to proactively address potential issues.
Configuration Options
The Cortex XSIAM SD Deployment Service offers several configuration options to tailor the service to specific needs. Customizable settings include data sources, processing algorithms, storage locations, and security protocols. These options enable optimization for diverse workloads and performance demands. For example, adjusting the number of processing threads can improve the service’s responsiveness.
Supported Deployment Environments
The service is designed for flexibility across various deployment environments.
| Deployment Environment | Description |
|---|---|
| Cloud (AWS, Azure, GCP) | Leverages cloud infrastructure for scalability and elasticity. |
| On-premises | Deployed on dedicated servers within a private network, offering greater control and security. |
| Hybrid | Combines cloud and on-premises deployment, allowing for a flexible approach. |
Best Practices for Deployment
Implementing best practices during deployment is critical for achieving optimal service performance and stability. Thorough testing and validation of configurations are paramount. Careful planning of resource allocation ensures efficient utilization. Implementing robust logging and monitoring systems allows for proactive issue resolution. Regular backups and disaster recovery strategies are crucial to protect against data loss and system failures.
Troubleshooting and Maintenance
Maintaining a smooth and reliable deployment of the Cortex XSIAM SD Deployment Service requires proactive strategies and a clear understanding of potential issues. This section details common problems, their solutions, monitoring procedures, maintenance options, and proactive prevention techniques. By understanding these elements, you can optimize service performance and minimize downtime.Troubleshooting encompasses a wide range of potential issues, from minor configuration errors to more complex system failures.
SD deployment service for Cortex XSIAM is all about efficiently getting your AI models into the field. It’s a fascinating area, and while the technology behind it is quite complex, understanding the different security features involved is key. This often involves considerations similar to those found in face unlocking systems, like those found in Samsung and Apple phones.
Comparing the approaches in differences between samsung and apple face unlocking reveals crucial insights into the varying security trade-offs. Ultimately, a solid SD deployment service is vital for any Cortex XSIAM project.
Understanding the root cause is crucial for effective resolution, and this section provides a framework for identifying and resolving these problems efficiently.
Common Issues and Solutions
Common issues can range from network connectivity problems to incorrect configurations. Addressing these problems quickly and effectively is crucial for maintaining service stability.
- Network Connectivity Issues: Verify network connectivity to the deployment server and ensure necessary ports are open. Check firewall rules and network configurations for potential blocks. Utilize network diagnostic tools to pinpoint the specific network problem.
- Configuration Errors: Incorrect configurations can lead to deployment failures. Double-check all configuration parameters against the service documentation. Ensure that the configuration files are correctly formatted and contain the required information.
- Resource Constraints: Insufficient system resources (CPU, memory, disk space) on the deployment server can impact performance and stability. Monitor resource utilization and adjust server settings or add resources as needed.
Monitoring and Management Procedures
Effective monitoring is essential for detecting and addressing potential issues before they escalate. This section details the procedures for proactive monitoring and management of the service.
- Service Logs: Regularly review service logs for errors and warnings. This helps identify patterns and pinpoint the source of problems. Employ log analysis tools for more complex issues.
- Performance Metrics: Monitor key performance indicators (KPIs) such as deployment time, throughput, and error rates. Identify anomalies in these metrics to proactively address potential bottlenecks or performance degradation.
- Alerting Systems: Set up alerting systems to notify administrators of critical events, such as service outages or high error rates. These alerts allow for rapid response and mitigation.
Maintenance Options and Schedules
Maintenance options and schedules vary based on specific needs and service requirements. Proper planning and execution of maintenance activities are crucial for minimizing downtime and ensuring service continuity.
- Scheduled Maintenance Windows: Plan maintenance activities during low-traffic periods to minimize disruption to users. Communicate maintenance windows to stakeholders in advance.
- Patching and Updates: Regularly apply security patches and updates to the deployment service to address vulnerabilities and improve stability. Plan patching windows during low-traffic periods.
- Backup and Recovery: Implement a robust backup and recovery strategy to protect against data loss and ensure quick recovery in case of failures. Regular backups are crucial for disaster recovery.
Common Error Codes and Explanations
A clear understanding of error codes is crucial for effective troubleshooting. This table provides a concise overview of common error codes and their explanations.
SD deployment service for Cortex XSIAM is all about streamlining the process, making it easier to manage and deploy. Thinking about how Instagram Live’s “close friends only” broadcasts work, you can see how these targeted features enhance engagement, just like our service simplifies complex deployments. This tailored approach makes SD deployment service for Cortex XSIAM exceptionally efficient, mirroring the targeted nature of instagram live close friends only broadcasts.
| Error Code | Explanation |
|---|---|
| 400 Bad Request | The request from the client is improperly formatted or contains invalid data. |
| 500 Internal Server Error | An unexpected error occurred on the server. |
| 404 Not Found | The requested resource was not found on the server. |
Proactive Prevention Strategies
Proactive measures can significantly reduce the likelihood of issues arising. This section details strategies for preventing potential problems.
- Regular System Checks: Conduct regular system checks to identify and address potential issues before they affect service availability. This includes checking for resource constraints and network connectivity.
- Code Reviews: Conduct thorough code reviews to identify and fix potential bugs or vulnerabilities in the deployment scripts. This is crucial for minimizing unexpected failures.
- Capacity Planning: Proactively plan for future growth and anticipate increased demand to ensure the service can handle peak loads and maintain performance. This involves evaluating current and projected needs.
Security Considerations and Best Practices

Securing the Cortex XSIAM SD Deployment Service is paramount to protect sensitive data and maintain the integrity of the deployed systems. Robust security measures are crucial to prevent unauthorized access, data breaches, and potential disruptions to service operations. This section Artikels the key security considerations and best practices for a secure deployment.Implementing a comprehensive security strategy involves multiple layers of protection, from network security to access controls.
This document details the protocols and measures in place, identifies potential vulnerabilities, and provides mitigation strategies. Understanding these aspects ensures the service is deployed and maintained with appropriate security precautions.
Security Protocols and Measures
The SD Deployment Service utilizes a layered security approach encompassing various protocols and measures to protect sensitive information and ensure the integrity of the system. This includes secure communication channels, encryption at rest and in transit, and rigorous authentication procedures.
- Secure Communication Channels: The service employs HTTPS (Hypertext Transfer Protocol Secure) for all communication between the client and the server. HTTPS encrypts data transmitted over the network, preventing eavesdropping and ensuring data confidentiality. This secure channel protects sensitive information exchanged during deployment, configuration, and maintenance operations.
- Data Encryption: Data at rest is encrypted using industry-standard encryption algorithms. This prevents unauthorized access if the storage system is compromised. Data in transit is also encrypted using TLS (Transport Layer Security) protocol to protect data during transmission. This ensures that confidential information remains confidential even if an attacker intercepts the communication.
- Authentication Procedures: The service employs multi-factor authentication (MFA) to verify the identity of users. This enhances security by requiring multiple verification steps beyond a simple username and password. MFA helps to prevent unauthorized access and strengthens the overall security posture of the system.
Potential Security Risks and Mitigation Strategies
Several potential security risks can compromise the integrity and confidentiality of the SD Deployment Service. Identifying and mitigating these risks is crucial for maintaining a secure environment.
- Unauthorized Access: A potential risk is unauthorized access to the service’s configuration or deployed systems. Mitigation strategies include strict access controls and user permissions, regular security audits, and the implementation of intrusion detection systems. These measures help to identify and prevent unauthorized attempts to gain access to sensitive data or modify configurations.
- Malware Infections: Malware attacks can compromise the deployed systems and potentially disrupt service operations. Mitigation strategies include using updated antivirus software, regularly patching systems, and implementing robust firewall rules. This helps to detect and prevent malicious software from infiltrating the system.
- Denial-of-Service Attacks: Denial-of-service (DoS) attacks can disrupt the service by overwhelming it with requests. Mitigation strategies include implementing rate limiting, load balancing, and intrusion prevention systems. These measures help to prevent the service from being overwhelmed by malicious traffic.
Importance of Access Controls and User Permissions
Effective access controls and user permissions are essential to limit access to sensitive resources and prevent unauthorized actions. The service employs a granular permission system that restricts access based on user roles and responsibilities.
- Role-Based Access Control (RBAC): The service utilizes a role-based access control model. This model defines specific roles for users, each with a predefined set of permissions. Users are assigned to roles based on their job functions and responsibilities. This ensures that only authorized personnel can access specific resources and perform particular actions.
- Least Privilege Principle: The principle of least privilege is applied to all user accounts. Users are granted only the necessary permissions to perform their tasks, minimizing the potential damage in case of a compromise. This helps to limit the impact of any security breaches.
Recommendations for Implementing Robust Security Practices
Implementing robust security practices is critical to ensuring the security and integrity of the SD Deployment Service.
- Regular Security Audits: Regular security audits help to identify vulnerabilities and ensure that security measures are effective. These audits should cover all aspects of the service, including access controls, communication channels, and deployed systems. By performing regular security audits, the system can be evaluated for any vulnerabilities and can be improved in areas where weaknesses exist.
- Security Awareness Training: Providing security awareness training to all users is essential. This training should cover topics such as phishing attacks, password security, and safe data handling practices. This training ensures that users understand the security risks and are aware of how to protect themselves and the service.
- Continuous Monitoring: Continuous monitoring of the service for suspicious activity is crucial. This monitoring should include logs, alerts, and security information and event management (SIEM) tools. This proactive approach helps to identify and respond to security threats in a timely manner.
Integration with Other Systems: Sd Deployment Service For Cortex Xsiam
The Cortex XSIAM SD Deployment Service isn’t an island; it’s designed to seamlessly integrate with various existing infrastructure components and tools. This allows for a unified and streamlined approach to deploying and managing security applications. Effective integration minimizes manual intervention, reduces errors, and enhances overall operational efficiency.This section details the supported integrations, the integration processes, available APIs and SDKs, and practical examples, providing a comprehensive guide for developers and administrators.
Supported Systems
The service supports integration with a range of systems, including cloud platforms (AWS, Azure, GCP), container orchestration platforms (Kubernetes), CI/CD pipelines (Jenkins, GitLab CI), and security information and event management (SIEM) platforms (Splunk, Elastic Stack). This diverse range of integration points allows for a flexible and adaptable deployment strategy, tailored to the specific needs of an organization.
Integration Process Overview
The integration process typically involves using provided APIs and SDKs to establish communication channels between the SD Deployment Service and the target system. This communication can involve triggering deployments, monitoring deployment status, or reporting relevant data. Detailed procedures are documented for each supported system, ensuring a straightforward integration experience.
Available APIs and SDKs
Comprehensive APIs and SDKs are offered for Python, Java, and Go programming languages, ensuring compatibility with existing infrastructure and developer tools. The APIs are designed for various use cases, including automated deployments, real-time monitoring, and integration with custom workflows. These tools empower developers to seamlessly integrate the service into their existing systems and applications. Example API calls are included in the documentation for each supported system.
Integration Examples
To illustrate the practical application of these integrations, consider an example of integrating with a Kubernetes cluster. The service can be configured to automatically deploy security applications to designated namespaces upon successful CI/CD pipeline completion. Another example is integration with a SIEM platform, allowing the service to automatically report deployment events and errors, providing valuable insights into deployment activities.
Integration Points Summary, Sd deployment service for cortex xsiam
| System | Integration Method | API/SDK | Example Use Case |
|---|---|---|---|
| AWS | Using AWS SDKs and APIs | AWS SDK for Python (boto3) | Automating deployment to AWS EC2 instances. |
| Azure | Using Azure SDKs and APIs | Azure SDK for Python (azure-mgmt-compute) | Deploying security applications to Azure virtual machines. |
| Kubernetes | Using Kubernetes API | Kubernetes Python client | Automated deployment to specific Kubernetes namespaces. |
| Splunk | Using Splunk HTTP APIs | Splunk SDK for Python | Reporting deployment events to Splunk for monitoring and analysis. |
| Jenkins | Using Jenkins plugins and APIs | Jenkins API | Triggering deployments from Jenkins CI/CD pipelines. |
Real-World Examples and Case Studies
The SD Deployment Service for Cortex XSIAM isn’t just theoretical; it’s been successfully implemented in various industries, leading to demonstrable improvements in security posture and operational efficiency. This section showcases real-world deployments, highlighting the positive outcomes achieved and the quantifiable improvements realized.This section details successful deployments across diverse industries, demonstrating how the service has been utilized to achieve tangible benefits.
By examining specific case studies, we can gain insights into the practical application of the service and its impact on user experience and operational efficiency.
Financial Services Sector Deployments
The financial sector, with its stringent security requirements and complex operational landscapes, has benefited significantly from the SD Deployment Service. A major investment bank, for example, deployed the service to bolster its fraud detection capabilities. By automating the deployment process for security tools, the bank reduced deployment time by 40% and reduced human error by 25%. This directly led to a 15% improvement in fraud detection accuracy, translating into substantial cost savings and a demonstrably improved user experience for compliance and regulatory reporting.
Healthcare Industry Applications
The healthcare sector, with its sensitive data and stringent regulatory compliance, leverages the service for secure access management and compliance reporting. A large hospital system implemented the service to manage access to sensitive patient data. This streamlined the access control process, reducing the time spent on manual reviews by 60% and ensuring compliance with HIPAA regulations. The result was a more efficient and secure environment, improving user productivity for clinical staff.
Retail Sector Implementations
The retail sector, with its focus on online transactions and data security, has effectively used the service to enhance security posture and improve data management processes. A major e-commerce company deployed the service to strengthen its security infrastructure, improving overall system performance. The deployment reduced average response time by 10%, which directly translated to a more efficient and user-friendly online shopping experience.
This improvement in response time was achieved by reducing network latency and optimizing data processing.
Manufacturing Industry Use Cases
The manufacturing sector, with its emphasis on operational efficiency and data-driven decision-making, successfully implemented the service for enhanced cybersecurity. A large manufacturing company deployed the service to protect its critical industrial control systems. The implementation successfully automated the security patching process, which resulted in a 30% reduction in time spent on manual patching. This automation also significantly reduced the risk of security breaches, resulting in a safer and more efficient production environment.
Future Trends and Developments
The SD Deployment Service for Cortex XSIAM is poised for continued growth and evolution. Anticipating the changing needs of security operations, this service will adapt to emerging technologies and use cases. This section details the future roadmap, potential improvements, and the evolving landscape of security deployment.
Future Roadmap and Potential Improvements
The service’s future roadmap focuses on enhanced automation, improved integration capabilities, and expanded support for diverse threat intelligence sources. Key improvements will center around streamlining deployment processes, enabling greater customization, and bolstering security posture. Automation will be crucial for efficient and rapid deployment across various environments, potentially including cloud-native architectures.
Emerging Trends and Technologies
The security landscape is constantly shifting. Cloud-native architectures, microservices, and the increasing use of machine learning for threat detection are impacting deployment strategies. The service will adapt to these trends by offering seamless integration with cloud platforms, enhanced support for containerization technologies, and leveraging machine learning algorithms for automated threat analysis and response. The growing adoption of zero-trust security models will also drive improvements in access control and identity management within the service.
Potential Future Applications and Use Cases
The SD Deployment Service’s future applications will extend beyond traditional network security. Predictive threat modeling and proactive security measures will be incorporated, allowing for anticipatory responses to emerging threats. Integration with incident response platforms will enable faster containment and remediation of security incidents. Furthermore, the service will likely support the development of custom security solutions tailored to specific enterprise needs.
This flexibility will allow organizations to adapt their security infrastructure to emerging threats more effectively.
Anticipated Enhancements in Future Releases
| Feature Category | Description | Anticipated Release ||—|—|—|| Automation | Improved automation scripts for diverse deployment scenarios, including containerized environments. | Q2 2024 || Integration | Enhanced integration with cloud platforms (AWS, Azure, GCP) and incident response tools. | Q3 2024 || Threat Intelligence | Integration with advanced threat intelligence feeds, enabling real-time threat analysis. | Q4 2024 || Customization | Expanded customization options for tailoring deployment configurations to specific security requirements.
| Q1 2025 || Zero Trust | Built-in support for zero-trust principles, including dynamic access control and micro-segmentation. | Q2 2025 |
Projections on the Evolution of the Service
The SD Deployment Service for Cortex XSIAM will evolve from a basic deployment tool to a comprehensive security orchestration, automation, and response (SOAR) platform. This evolution will be driven by the integration of advanced threat intelligence, automation capabilities, and zero-trust principles. Future iterations will be focused on enabling organizations to proactively anticipate and mitigate threats in dynamic and complex environments.
As an example, a future version might include automated response capabilities to specific threat vectors based on real-time threat intelligence feeds.
Ending Remarks
In conclusion, the SD deployment service for Cortex XSIAM provides a robust and efficient solution for deploying this essential security platform. By understanding its architecture, features, and deployment procedures, organizations can confidently leverage Cortex XSIAM to enhance their security posture and improve operational efficiency. The service’s flexibility and scalability make it adaptable to diverse environments and needs, offering a strong foundation for future growth and security advancements.