Androids permissions are better ever still need lot work – Android permissions are better than ever, still needing a lot of work. This in-depth look explores the evolution of Android permissions, from their foundational purpose to the ongoing challenges and future directions. We’ll examine the various types of permissions, their impact on user experience, and the often-confusing aspects of requesting them. The discussion will cover everything from the historical context of permission management to the potential solutions for improving the user experience.
The current state of Android permissions presents both strengths and weaknesses. While the system has improved significantly over time, usability and transparency remain key areas for enhancement. Users deserve clear and concise explanations for permission requests, alongside options for more granular control. This article will delve into specific issues and potential solutions.
Android Permissions Overview
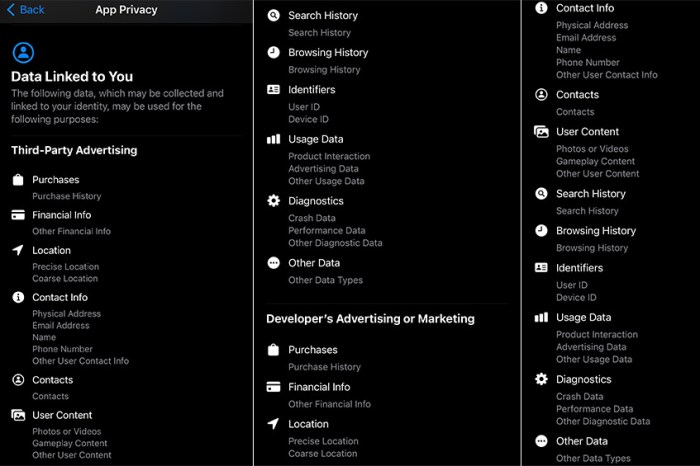
Android permissions are a crucial component of the Android operating system, carefully regulating access to various system resources. They serve as a critical security mechanism, safeguarding user data and privacy by preventing applications from accessing sensitive information or functionalities without explicit user consent. This approach fosters a more secure and user-friendly mobile experience.Permissions are essential for granting applications specific access rights.
Without these permissions, an application wouldn’t be able to perform actions that require them, ensuring that applications operate within defined boundaries. This controlled access protects users from unauthorized actions and ensures that applications adhere to established security guidelines.
Understanding Permission Types
Permissions in Android are categorized into different types, each governing access to specific resources. These categories are designed to provide a granular level of control, enabling applications to request only the permissions necessary for their functionality.
- Location Permissions: These permissions grant access to the device’s location services, allowing applications to determine the user’s geographic position. Common use cases include mapping applications, navigation tools, and location-based services. Examples include finding nearby restaurants or checking in at a specific location.
- Camera Permissions: These permissions enable applications to access the device’s camera, allowing functionalities like taking photos, recording videos, or scanning barcodes. Applications using this permission might be photo editing apps, video conferencing platforms, or barcode scanners.
- Storage Permissions: These permissions allow applications to access the device’s internal and external storage, enabling file reading, writing, and manipulation. Typical applications needing this access are file managers, photo galleries, and document editors.
- Contact Permissions: These permissions provide access to the user’s contact list, facilitating actions like displaying contacts, sending messages, or performing other operations related to user’s contacts. Examples include address books and communication applications.
- Microphone Permissions: This permission grants access to the device’s microphone, enabling applications to record audio or participate in voice calls. This includes voice assistants, video conferencing tools, and recording apps.
Permission Comparison
The following table compares and contrasts different permission types, emphasizing their impact on user experience:
| Permission Type | Typical Use Cases | User Experience Impact |
|---|---|---|
| Location | Navigation, location-based services | Enhanced convenience, but potential for tracking concerns |
| Camera | Photo/video capture, scanning | Enhanced functionality, but privacy implications |
| Storage | File management, data access | Critical for file-related tasks, but potentially exposing data |
| Contact | Communication, address books | Facilitates communication, but sensitive data access |
| Microphone | Voice recording, voice calls | Enables voice interactions, but potential privacy concerns |
Best Practices for Permission Requests
Effective permission management in Android applications is crucial for maintaining a positive user experience. Here are key principles and best practices:
- Explain the purpose clearly: Explain why an application needs a specific permission, detailing how it will be used. Users should understand the context of the permission request.
- Request only necessary permissions: Requesting fewer permissions than needed helps maintain user trust and reduces the risk of accidental data exposure.
- Request permissions proactively: Request permissions at the appropriate moment, ideally when the feature requiring the permission is first used. This prevents unnecessary interruptions and enhances user experience.
- Provide a clear rationale: Provide a concise and understandable rationale for requesting each permission, explaining the functionality it enables. Avoid vague or misleading explanations.
- Respect user choices: Respect the user’s decision to grant or deny permissions, and offer ways to revisit permission settings if needed.
Evolution of Android Permissions
Android’s permission system has undergone significant evolution, reflecting a growing emphasis on user privacy and security. Early versions presented a less granular and user-friendly approach, leading to concerns about app overreach. This evolution has resulted in a more nuanced and empowering permission model for users, and more stringent guidelines for developers.The modern Android permission system, while still under development, has demonstrably improved the balance between app functionality and user control.
The shift toward a more granular and contextual approach has brought increased user transparency and control over how apps access their device’s resources. This has resulted in a more secure and user-friendly platform for all.
Key Improvements in Permission Management
The evolution of Android permissions has focused on several key improvements. These improvements are designed to enhance user privacy and provide a more secure platform. The primary goal is to give users more control over the data and resources their apps access.
- Granularity and Contextualization: Modern Android versions employ a more granular approach to permissions, allowing developers to request specific permissions for particular actions or functionalities. This differs from older systems that often requested broad permissions. For example, an app requesting location access only when needed (e.g., for navigation) is a significant improvement over requesting it for general usage. This contextual approach directly benefits user privacy by restricting access to the resource only when the user intends for the app to use it.
Android’s permission system, while definitely improved, still needs a lot of work. It’s a bit of a mixed bag, really. You’ve got to appreciate the effort put into making it more user-friendly, especially when compared to older versions. Speaking of improvements, if you’re looking to catch the UFC 307 Alex Pereira vs Khalil Rountree Jr. fight, be sure to check out the full card and livestream start time details here: ufc 307 alex pereira vs khalil rountree jr watch livestream start time full card.
But even with these improvements, the whole permission structure still feels a little clunky at times. More intuitive design is needed.
- User-Friendly Request Mechanisms: Permission request mechanisms have become more user-friendly. Users are presented with clear explanations of why an app needs a specific permission, often accompanied by a visual representation. This transparency directly empowers users to make informed decisions regarding their device’s resources. These improvements are aimed at addressing the previous lack of transparency in permission requests, which often left users in the dark about the app’s intentions.
- App Development Practices: Permission management has significantly impacted app development practices. Developers are encouraged to adopt a more responsible approach to permission requests, minimizing the use of broad permissions. This fosters a more user-centric design approach. Developers are also expected to provide clear explanations of why their app requires certain permissions. This has shifted the emphasis to a more user-centered approach to app design and development, reflecting the importance of user trust and data security.
Comparison of Permission Request Mechanisms Across Versions
The permission request process has evolved significantly across Android versions. This evolution has been driven by the need for a more secure and user-friendly approach. Early versions often lacked the granular control and transparency of newer versions.
| Android Version | Permission Request Mechanism | User Experience |
|---|---|---|
| Older Versions (pre-Marshmallow) | Apps could request broad permissions without much explanation. | Limited user control; users often unaware of the extent of access an app had. |
| Marshmallow (API 23) and Later | Introduced the concept of runtime permissions, requiring explicit user consent for each permission. | Users gain greater control over app access to device resources; greater transparency in app functionality. |
Impact on App Development
The changes in permission management have directly impacted app development. Developers must adapt to the new framework. This includes adjusting their apps to request permissions dynamically and provide clear explanations for each permission request. This shift emphasizes a more responsible and user-centric approach to app development, which is essential for maintaining user trust and ensuring the security of the platform.
Apps must be designed to minimize the number of permissions requested and clearly communicate why they are needed.
Current State of Android Permissions
Android’s permission system, while foundational to app functionality, has evolved through several iterations. This evolution has aimed to strike a balance between app functionality and user privacy, but the current state still presents challenges. Understanding these challenges is crucial for developers and users alike to navigate the landscape effectively.The current Android permission system, while improved over previous versions, remains a point of contention.
Users often face unexpected permission requests that seem excessive or unnecessary. The system’s effectiveness hinges on transparency and user comprehension. How these permissions are presented to users significantly influences their trust and adoption of apps.
Effectiveness and User Experience
The current Android permission system strives to balance the need for app functionality with user privacy concerns. However, its effectiveness is mixed. Some users find the system to be helpful, while others are confused or frustrated by the frequency and scope of permission requests. This ambiguity often leads to a sense of unease regarding the app’s true intentions.
The system aims to empower users to make informed choices, but the practical application often falls short.
Common Issues and Drawbacks
The current system suffers from several issues. One prominent problem is the perceived lack of context around permission requests. Users may not fully understand why an app requires specific permissions, leading to uncertainty. Furthermore, the granularity of some permissions can be too broad, resulting in unnecessary access to user data. For example, an app requesting location access for a simple search function could be considered excessive.
Problematic Permission Requests
Many permission requests can be problematic or confusing to users. A prominent example involves apps requesting access to sensitive data like contacts or calendar events without clearly explaining the purpose. This lack of context often leads to users denying permissions, even if the app requires them for a legitimate function. Another example involves apps that request camera access for seemingly unrelated functionalities.
This lack of transparency creates user mistrust.
User Frustrations and Complaints
User complaints often revolve around a lack of clarity regarding permission requests. Users feel misled or exploited when they perceive that an app is asking for excessive permissions. This is often coupled with a lack of explanation for why these permissions are needed. Many users report that the permission request dialogs are not user-friendly, making it difficult to understand the implications of granting or denying access.
Users often report confusion or frustration regarding the specific permissions being requested. This ambiguity makes it difficult for users to understand the implications of granting or denying these requests.
Current Trends and Future Directions
Current trends indicate a push toward more granular and context-aware permission systems. The goal is to provide users with more control over their data while also ensuring that apps have the necessary access to function. Future directions likely involve a greater emphasis on explaining the specific use cases for permissions. For example, an app requesting location access for a specific task, like finding nearby stores, would be more transparent and less intimidating.
Areas for Improvement
The Android permission system, while significantly improved over time, still faces challenges in achieving optimal user experience and transparency. These shortcomings often lead to user confusion and a perceived lack of control over app access to sensitive data. Addressing these areas is crucial for fostering trust and encouraging responsible app development.Improving the permission system requires a multi-faceted approach, focusing on both the presentation of requests and the user’s ability to manage permissions granted.
Clearer communication, more granular control, and a streamlined process are essential to mitigate user anxiety and ensure app functionality aligns with user expectations.
Granularity of Permission Requests
The current system often presents users with broad permission requests, encompassing multiple functionalities within a single request. This lack of granularity can lead users to unknowingly grant access to features they don’t intend to use. For example, an app requesting location permission might also encompass access to precise location data, which the user might not be comfortable with.A more granular approach would allow users to grant permissions on a per-functionality basis, rather than granting access to a broad set of capabilities.
This would empower users to make informed decisions, aligning app access with their individual preferences.
Improved Permission Request Dialogs
The presentation of permission requests is often not user-friendly, lacking clear explanations of why an app requires a specific permission. Users often perceive the request as a mandatory requirement rather than a request for specific functionalities.To improve the user experience, permission requests should be more contextual and informative. Explaining how the permission is used and how it directly contributes to the app’s functionality will enhance transparency and user trust.
For example, a camera app requesting storage permission should clearly state that it’s needed to save the captured photos.
Android’s permission system is definitely a step up, but there’s still a ton of work to be done. It’s a bit like learning how to update your PS5 DualSense controller, a process that can seem complicated at first. Luckily, there’s a helpful guide to walk you through the process, including all the steps you need to know. ps5 playstation controller how to update dualsense This is a similar kind of complexity to understanding and managing app permissions.
Even with the improvements, the sheer number of permissions and their interactions still require refinement for a truly seamless experience.
Streamlined Permission Management
Current methods for managing granted permissions often lack a centralized and intuitive interface. Users might struggle to revoke permissions or understand which apps have access to their data. This can lead to a sense of helplessness and frustration when dealing with permissions issues.Providing a dedicated permission management screen within the Android settings will empower users to review and modify app permissions at any time.
This would offer a clear and accessible way to control app access to sensitive information, fostering greater user agency.
Transparency and Explanation, Androids permissions are better ever still need lot work
The lack of transparency in the Android permission system can create a significant hurdle for users. Often, apps requesting permissions fail to adequately explain
why* they need a specific permission.
To enhance transparency, a standardized approach for describing the use of permissions is needed. This should involve clear explanations, including specific examples, within the app’s permission request dialogs. This practice will help users understand the context behind the request and make informed decisions about granting permissions.
Future-Proofing the System
Future improvements should consider the evolving needs of users and the growth of app functionalities. The permission system should adapt to accommodate new use cases, such as those related to emerging technologies.For example, as AI-powered features become more integrated into apps, the permission system must clearly delineate the data usage for these features, allowing users to understand how their data is being processed and used.
Android permissions are definitely better than they used to be, but there’s still a ton of work to be done. It’s a bit like the recent Akira Toriyama Sand Land animated movie by Bandai Namco ; it’s visually impressive, but still needs a little something extra to make it truly special. Similarly, Android permissions are visually improved, but the underlying implementation and user experience still have plenty of room for enhancement.
This ensures user data is protected in accordance with evolving technologies.
User Experience Considerations
Android permissions are a crucial aspect of app development, yet they can significantly impact the user experience. A poorly designed permission request process can lead to user frustration and app abandonment. Understanding the user’s perspective and crafting a clear, concise, and trustworthy approach is paramount.Effective permission management goes beyond simply asking for access. It requires a delicate balance between the app’s functionality and the user’s comfort level.
This involves anticipating user concerns, mitigating perceived risks, and designing a streamlined permission request process.
Permission Request Dialog Design
A well-designed permission request dialog is key to a positive user experience. The dialog should be easy to understand and navigate, providing clear context for why the permission is needed. Ambiguity or overly technical language should be avoided.
- Clarity and Conciseness: The dialog should clearly state the permission’s purpose. Use simple, everyday language, avoiding jargon. For example, instead of “access to device location history,” use “allow us to show you your recent location.” Users need to quickly grasp the reason behind the request.
- Contextual Explanation: Highlight the specific use case for the permission. Don’t just say “location access” but explain how it directly benefits the user, such as “to find nearby stores” or “to provide you with real-time directions.” A direct link between the permission and the app’s functionality is crucial.
- Visual Cues: Use visual cues like icons or illustrations to enhance understanding. A small map icon with the permission request for location access would greatly aid comprehension.
Good and Bad Permission Request Practices
Effective permission requests are critical for user trust and engagement. A poorly designed request can negatively impact the user’s perception of the app.
- Good Practice: A permission request should clearly explain the purpose of the requested permission and how it directly benefits the user. For example, “Allow access to your photos to enable you to upload your photos to the social media feed.” This approach builds trust and demonstrates transparency.
- Bad Practice: A request that is vague, overly broad, or lacks context will likely cause user apprehension. “Grant us access to all your data for optimal performance” is an example of a poorly phrased request. This kind of request creates a negative perception of the app and can lead to user distrust.
Reducing Friction for Users
Friction in the permission request process can lead to user reluctance and app abandonment. Minimizing this friction is crucial for a positive user experience.
- Option for Later: Allow users to defer the permission request if possible. This avoids disrupting the user flow and can lead to a more positive first impression. Offer a clear alternative like “Request later” or “Skip for now” buttons.
- Avoid Multiple Requests: Minimize the number of permission requests for a single feature. Requesting all necessary permissions in one prompt enhances user experience and avoids a confusing barrage of requests.
- Progressive Disclosure: Request permissions only when they are necessary. Avoid requesting permissions upfront for features that the user may not even use. This builds user trust and avoids an overwhelming initial experience.
Improving User Trust and Reducing Perceived Risk
Building trust is essential to a successful app. Users need to understand that the app is trustworthy and will only use their data appropriately.
- Transparency: Be upfront about how the data will be used. Include clear privacy policies that users can easily access. Provide specific details on data storage and usage.
- Clear Data Usage: Demonstrate that the collected data is being used responsibly. Highlight the benefits of the collected data for the user and provide clear examples of how this data is used.
- Security Measures: Emphasize security measures to protect the user’s data. Show that you’re committed to protecting their information and that you take data privacy seriously.
Potential Solutions and Future Directions
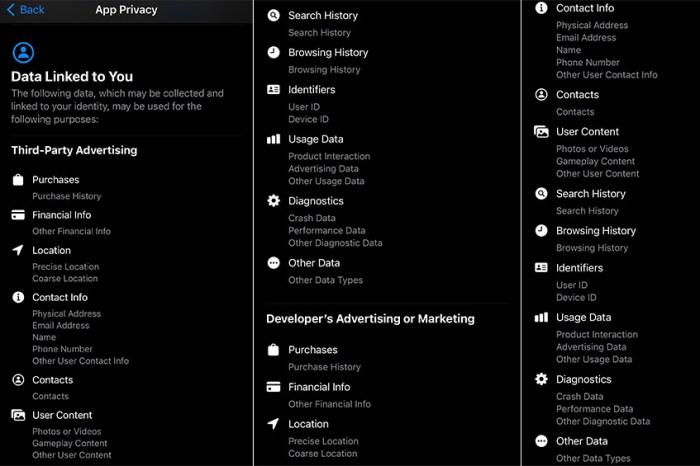
Android’s permission system, while foundational, still needs significant refinement. The current approach often presents a challenging balance between granting necessary app functionality and safeguarding user privacy. This section explores potential solutions, focusing on a more empowering and intuitive experience for users.The future of Android permissions hinges on a more nuanced and user-centric approach. This necessitates a system that empowers users with clear and actionable choices, fostering trust and transparency in the app development process.
It’s vital to move beyond the current binary permission model, offering granular controls and adaptable options.
Potential Solutions for Improved Permission Management
A more nuanced approach to permission management requires several key changes. One crucial element is a tiered system of permissions, allowing apps to request access based on specific use cases rather than broad, potentially intrusive categories. This allows for a more granular level of control, where users are not presented with an all-or-nothing choice.
- Granular Permissions: Instead of a single “location” permission, apps could request specific location data, such as “location for five minutes while using the app.” This allows users to control the duration and context of permission grants, promoting better trust and reducing potential misuse.
- Contextual Permissions: Permissions could be tied to specific actions or contexts. For example, an app requesting camera access might only be granted permission when a user is actively taking a picture, rather than being granted perpetual access. This approach would limit the potential impact of misuse and give users more control over when permissions are active.
- Permission Revocation: Users should have the ability to revoke permissions at any time, with clear explanations for why the permission is being revoked. This includes easy ways to restore previous permission if needed.
- Transparency and Explanation: Apps should clearly explain
-why* a specific permission is needed, going beyond generic explanations. This can include specific examples or use cases that illustrate how the data will be used. A simple “this permission is needed to show you nearby restaurants” is preferable to “this permission is needed for general functionality.”
Balancing User Privacy with App Functionality
The ideal permission system should provide a strong framework for balancing user privacy with app functionality. The system should prioritize user control, transparency, and clear communication to build user trust. This necessitates a shift away from a simple grant/deny model towards a more dynamic and contextual approach.
- Phased Permissions: Apps could request permissions in phases. Initial access might be limited to basic functionality. More granular permissions could be requested later, if and only if the user continues to interact with the app and demonstrates positive use cases. This fosters trust and allows users to evaluate the app’s behavior before granting extensive access.
- Usage-Based Permissions: Permissions could be automatically revoked if an app doesn’t utilize the requested data for a set period. This prevents apps from hoarding permissions that aren’t being used.
- User Feedback Mechanisms: Regular feedback from users about their permission experiences is critical. Mechanisms should be in place to allow users to report issues, suggest improvements, or voice concerns about specific permissions.
Hypothetical Permission Management System
Imagine a system where users can review and customize their permission grants on a per-app basis. This system could offer a visual representation of how apps are using permissions and allow users to selectively adjust access levels.
| Permission Management Strategy | User Empowerment | App Development Impact |
|---|---|---|
| Phased Permissions | High, gradual trust building | Requires more nuanced app design |
| Contextual Permissions | High, focused control | More complex logic for app functionality |
| Usage-Based Permissions | High, active control | Requires careful monitoring and revocation logic |
Impact on App Development and User Experience
A revamped permission system will require developers to design apps with more consideration for user privacy. However, the benefits will extend to both developers and users. Improved user trust and better app experiences will be the result of this shift.
Permissions and App Functionality
Android apps rely heavily on permissions to access various device resources. These permissions, while crucial for functionality, are also a double-edged sword, demanding a careful balance between app needs and user privacy. A well-designed permissions system is essential for creating robust and user-friendly applications.Understanding the direct impact of permissions on app capabilities is paramount. Permissions are not merely checkboxes; they are the keys that unlock specific functionalities.
Without the appropriate permissions, apps may be significantly crippled, impacting user experience and limiting their effectiveness.
Impact of Permissions on App Functionality
Permissions are integral to the operation of many apps. A camera app, for example, needs camera access to capture images. Similarly, a location-based app requires location access to pinpoint user position. Without these permissions, these apps simply cannot perform their intended functions.
Implications of Not Requesting Necessary Permissions
Failing to request necessary permissions results in a severely limited application. An app that needs access to the user’s contacts but does not request it will be unable to display contact information or perform contact-related actions. This often leads to a frustrating user experience, where the app feels incomplete or broken.
Examples of Apps Leveraging Permissions Effectively
Many apps exemplify how to effectively use permissions. A weather app, for instance, leverages location permissions to provide personalized weather forecasts based on the user’s current location. A social media app utilizes contact permissions to suggest friends or facilitate communication with existing contacts. These examples demonstrate how permissions empower apps to deliver specific and valuable features.
Importance of Permissions in Ensuring App Functionality
Permissions are vital for ensuring apps function as intended. They provide the bridge between app capabilities and the device’s resources. A meticulously designed permission request process helps users understand exactly what an app needs to do its job, promoting transparency and user trust.
Breakdown of Various Use Cases Where Permissions are Critical
Various use cases necessitate specific permissions for app functionality. This table illustrates some key examples:
| App Category | Permission | Functionality |
|---|---|---|
| Camera Apps | Camera | Capturing photos and videos |
| Location-Based Services | Location | Determining user location, providing location-based services, like navigation, or checking nearby places. |
| Social Media Apps | Contacts | Suggesting friends, facilitating communication with existing contacts |
| Messaging Apps | SMS/MMS | Sending and receiving text messages |
| File Management Apps | Storage | Reading, writing, and managing files on the device |
Closing Notes: Androids Permissions Are Better Ever Still Need Lot Work
In conclusion, Android permissions, while significantly improved, still face challenges in user experience. The evolution of permission requests has made progress, but friction points remain in clarity and user control. Addressing these areas with improved transparency and user empowerment is crucial for a better mobile experience. This discussion highlights the importance of balance between app functionality and user privacy, paving the way for a more intuitive and trustworthy permission system in the future.