With prisma cloud uts gains comprehensive visibility contextual assessment and simplifies compliance – With Prisma Cloud, you gain comprehensive visibility, contextual assessment, and simplify compliance. This powerful platform offers deep insights into your security posture, going beyond basic scans to understand the context behind potential threats. By leveraging contextual information like user activity and application logic, Prisma Cloud proactively identifies vulnerabilities and simplifies compliance procedures, ultimately bolstering your overall security posture.
Imagine having a crystal-clear view of your entire IT infrastructure, not just isolated parts. Prisma Cloud provides that visibility, allowing you to see application traffic, infrastructure configurations, and vulnerabilities in real-time. This comprehensive view, coupled with contextual assessment, allows you to understand the ‘why’ behind security events and proactively address risks. Simplified compliance processes are a natural consequence, leading to greater efficiency and reduced administrative overhead.
Comprehensive Visibility
Prisma Cloud’s comprehensive visibility isn’t just about seeing what’s happening; it’s about understanding
- why* and
- how* it impacts your security posture. This deep insight empowers security teams to proactively identify and address vulnerabilities, understand attack surfaces, and fortify their defenses against ever-evolving threats. This visibility is crucial for modern security operations, enabling a shift from reactive to proactive security measures.
Comprehensive visibility within Prisma Cloud allows security teams to see a holistic picture of their entire application and infrastructure landscape, moving beyond isolated views to a unified, contextualized understanding. This integrated view provides the necessary context to identify threats early and respond effectively. This level of insight is fundamental to successful security operations in today’s complex threat environment.
Prisma Cloud UTM’s impressive visibility, contextual assessment, and compliance simplification capabilities are top-notch. Thinking about a new phone? Checking out the latest Samsung Galaxy M series India pricing and features can be super helpful when comparing different options samsung galaxy m series india pricing features. Ultimately, Prisma Cloud UTM’s powerful features make it a strong choice for businesses looking for a streamlined and secure approach to their cloud environments.
Types of Visibility
Prisma Cloud provides multiple layers of visibility, encompassing various aspects of your infrastructure and applications. These different views allow security teams to build a complete picture of their attack surface and identify potential vulnerabilities. Understanding application traffic, infrastructure configurations, and vulnerabilities is essential for effective threat detection and response.
- Application Traffic Visibility: Prisma Cloud’s detailed visibility into application traffic provides insights into the flow of data and interactions between different components within your application. This allows for monitoring of unusual traffic patterns, suspicious activities, and potential attacks in real-time. For instance, a sudden spike in requests from a particular IP address might indicate a malicious attempt.
- Infrastructure Configuration Visibility: Prisma Cloud monitors the configuration of your infrastructure, including servers, networks, and cloud resources. This provides a comprehensive view of your environment, identifying misconfigurations and vulnerabilities that could be exploited. A misconfigured firewall rule, for example, could expose sensitive data to unauthorized access.
- Vulnerability Visibility: Prisma Cloud identifies vulnerabilities in your applications and infrastructure. This visibility includes a detailed assessment of known vulnerabilities, as well as those introduced through new or modified code. Understanding the potential vulnerabilities in your code base and infrastructure is vital for mitigating risks.
Actionable Insights
The visibility Prisma Cloud provides translates directly into actionable insights for security teams. By correlating different data points, security analysts can quickly identify potential threats, understand their impact, and take appropriate action.
- Threat Detection: Prisma Cloud’s ability to identify suspicious activities and anomalies in application traffic helps security teams detect threats earlier in the attack lifecycle. For instance, if Prisma Cloud detects unusual login attempts from an unknown IP address, security teams can quickly investigate and respond.
- Vulnerability Management: Comprehensive visibility into vulnerabilities allows security teams to prioritize remediation efforts. By identifying vulnerabilities, Prisma Cloud allows for proactive patching and mitigation, reducing the potential for exploits.
- Compliance: The holistic view of your environment enables security teams to ensure compliance with industry regulations and standards. Prisma Cloud simplifies compliance by providing a clear picture of your security posture.
Data Points and Holistic View
The following table Artikels the various data points Prisma Cloud collects and how they contribute to a holistic view of your environment.
| Data Point | Contribution to Holistic View |
|---|---|
| Application traffic patterns | Identifies unusual activities, potential attacks, and anomalies in application behavior. |
| Infrastructure configurations | Highlights misconfigurations, exposes potential vulnerabilities in your infrastructure, and enables the identification of weak points in your security posture. |
| Vulnerabilities | Provides a clear picture of known and unknown vulnerabilities in your application and infrastructure. Enables prioritization of remediation efforts. |
| User activity | Provides a context to understand the activities of users and identify suspicious behavior that may indicate potential insider threats. |
| Security events | Correlates security events across different components of the environment to understand the context and potential impact of an incident. |
Contextual Assessment
Security assessments are evolving beyond simple scans. Traditional approaches often miss the nuanced details that reveal real vulnerabilities. Modern security tools, like Prisma Cloud, are leveraging contextual assessment to provide a deeper, more accurate understanding of risk. This approach moves beyond surface-level analysis to consider the broader environment and specific circumstances.Contextual assessment is a security analysis method that goes beyond traditional scanning techniques.
It enriches security findings by incorporating various contextual factors, leading to a more precise and accurate understanding of potential risks. This detailed analysis provides a richer understanding of the environment and how potential threats might interact with it.
Understanding Contextual Assessment
Contextual assessment goes beyond simply identifying vulnerabilities. It delves into the intricacies of an organization’s environment, including user activity, application logic, compliance regulations, and infrastructure configurations. By considering these interconnected elements, contextual assessment can identify vulnerabilities that traditional scanning methods might miss.
How Prisma Cloud Uses Context
Prisma Cloud leverages contextual information to enhance the accuracy and relevance of security findings. The tool analyzes user access patterns, application flow, and compliance requirements to better understand the potential impact of identified vulnerabilities. This deeper understanding allows for more informed security decisions. For example, a vulnerability identified in a rarely accessed part of the application might be less critical than one affecting frequently used functionalities.
Prisma Cloud accounts for these nuances.
Contextual Information in Security Decisions
Contextual information significantly impacts security decisions. User activity, for instance, can reveal suspicious login patterns or unauthorized access attempts. Analyzing these activities alongside application logic can help pinpoint potential exploits. Similarly, compliance requirements, such as industry regulations, can influence security decisions. If a vulnerability violates a specific compliance standard, Prisma Cloud can flag it as a higher priority.
This allows organizations to focus their resources on the most impactful risks.
Traditional Scanning vs. Contextual Assessment
| Feature | Traditional Scanning | Contextual Assessment |
|---|---|---|
| Approach | Identifies vulnerabilities based on predefined rules and signatures. | Analyzes vulnerabilities within the context of user activity, application logic, and compliance requirements. |
| Accuracy | Can be less accurate due to lack of contextual awareness. | More accurate and relevant findings due to comprehensive analysis. |
| Relevance | May flag vulnerabilities that are not practically significant. | Prioritizes vulnerabilities based on their potential impact within the specific environment. |
| Depth | Surface-level analysis. | In-depth analysis considering various contextual factors. |
| Weaknesses | Can miss vulnerabilities that are dependent on specific configurations or user behavior. | Requires accurate and up-to-date contextual data to be effective. |
| Strengths | Faster identification of known vulnerabilities. | Improved prioritization and remediation of vulnerabilities based on actual risk. |
Simplifying Compliance: With Prisma Cloud Uts Gains Comprehensive Visibility Contextual Assessment And Simplifies Compliance
Navigating the complex landscape of security compliance can be daunting. Manual processes, scattered tools, and a lack of visibility often lead to delays, errors, and increased risk. Prisma Cloud addresses these challenges by streamlining compliance procedures, providing comprehensive visibility, and automating key tasks. This allows organizations to focus on their core business objectives while maintaining regulatory compliance.Prisma Cloud simplifies compliance by automating the process of identifying and remediating security vulnerabilities.
This automation significantly reduces the time and resources required for compliance audits, allowing security teams to focus on proactive security measures rather than reactive remediation efforts. The platform provides a centralized view of security posture across the entire application lifecycle, facilitating a holistic approach to compliance.
Prisma Cloud UTM’s impressive gains in comprehensive visibility, contextual assessment, and simplified compliance are definitely noteworthy. Think about how a tool like the Ford Parking City Dash Appy could benefit from this enhanced clarity and streamlined processes. Ultimately, Prisma Cloud UTM’s strengths in these areas remain crucial for modern security and operational efficiency.
Compliance Framework Support
Prisma Cloud supports various compliance frameworks, ensuring that organizations can meet the specific requirements of their industry or sector. These frameworks often dictate specific security controls and procedures that must be implemented and maintained. Prisma Cloud helps organizations meet these requirements by providing comprehensive visibility and automated controls. For instance, PCI DSS (Payment Card Industry Data Security Standard) compliance requires stringent controls over data handling, storage, and transmission.
Prisma Cloud UTM’s impressive visibility, contextual assessments, and streamlined compliance features are top-notch. Imagine integrating that with the seamless control offered by Amazon Alexa, Nest, and Honeywell thermostats, like amazon alexa nest honeywell thermostat control. Ultimately, Prisma Cloud UTM’s comprehensive approach to security and control remains invaluable.
Prisma Cloud can help meet these requirements by automating vulnerability scans, detecting suspicious activity, and ensuring secure configurations. Similarly, Prisma Cloud supports HIPAA (Health Insurance Portability and Accountability Act) compliance by helping organizations maintain strict controls over protected health information (PHI).
Automation Features for Streamlined Compliance
Prisma Cloud offers powerful automation features that streamline compliance tasks. These features automate repetitive actions, freeing up security teams to focus on strategic initiatives. Automation helps to reduce errors, increase efficiency, and reduce the time and resources required for compliance tasks. Automated vulnerability scanning, configuration checks, and policy enforcement help to ensure that security controls are continuously maintained and that the organization meets compliance requirements.
These automated features reduce manual effort, improving accuracy and consistency.
Compliance Features Overview
| Compliance Feature | Automation Tools | Reporting Capabilities | Integration Points |
|---|---|---|---|
| Vulnerability Scanning | Automated scans for known vulnerabilities; integration with vulnerability databases | Detailed reports on vulnerabilities, including remediation recommendations | Integration with CI/CD pipelines, cloud environments, and existing security tools |
| Configuration Management | Automated checks for secure configurations; enforcement of security policies | Reports on configuration discrepancies and recommendations for remediation | Integration with cloud platforms, infrastructure-as-code tools, and existing security tools |
| Policy Enforcement | Automated enforcement of security policies across the application lifecycle | Comprehensive policy violation reports and remediation guidance | Integration with various cloud platforms and application development tools |
| Security Posture Management | Continuous monitoring of security posture and automatic remediation | Comprehensive dashboards and reports on overall security posture | Integration with existing security tools and infrastructure |
Relationship Between Elements
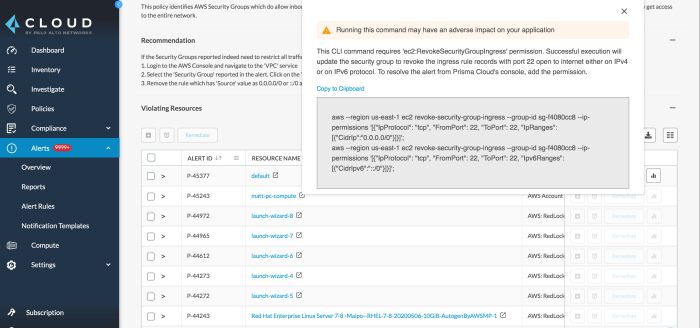
Prisma Cloud’s power lies in the intricate dance between comprehensive visibility, contextual assessment, and simplified compliance. These aren’t isolated features; they’re interconnected components that work synergistically to build a robust security posture. This synergy allows organizations to not just identify vulnerabilities but also understand their impact and quickly implement appropriate remediation strategies.The core principle is that comprehensive visibility acts as the foundation, providing the necessary data for contextual assessment.
This assessment then clarifies the implications of the identified risks, ultimately streamlining the compliance process. This streamlined process ensures that security efforts are not only effective but also efficient.
Interdependencies Within Prisma Cloud
Prisma Cloud’s architecture is designed with these interdependencies in mind. Comprehensive visibility is achieved through various data sources, including logs, network traffic, and application activity. This data is crucial for contextual assessment. Contextual assessment analyzes this visibility, factoring in the specific environment and potential attack vectors. This process isn’t simply a data dump; it’s a sophisticated analysis that considers the relationships between various security elements.
The output of this assessment directly informs the compliance simplification process.
Flow of Data from Collection to Compliance Reporting
| Stage | Description |
|---|---|
| Data Collection | Prisma Cloud gathers security data from diverse sources, including logs, network traffic, and application activity. |
| Data Aggregation and Normalization | Collected data is aggregated and normalized to ensure consistency and compatibility. |
| Contextual Assessment | The normalized data is analyzed to determine potential risks and vulnerabilities. Factors like user behavior, application dependencies, and compliance regulations are considered. |
| Risk Prioritization | Identified risks are prioritized based on severity and potential impact. |
| Compliance Reporting | Prisma Cloud generates reports that clearly Artikel compliance status, highlight any deviations, and recommend remediation steps. |
Benefits of Integrated Features
- Reduced Security Risks: By combining visibility, assessment, and compliance, Prisma Cloud significantly reduces the likelihood of security breaches. This holistic approach allows for proactive mitigation of threats.
- Improved Compliance Posture: The simplified compliance process ensures that organizations consistently meet industry standards and regulatory requirements.
- Enhanced Efficiency: Automating the compliance process frees up security teams to focus on higher-value tasks.
- Proactive Risk Management: Prisma Cloud’s contextual assessment enables proactive risk management, allowing organizations to address potential issues before they escalate.
- Data-Driven Decision Making: The comprehensive visibility and contextual assessment provide the data needed for informed security decisions.
Use Cases and Examples
Prisma Cloud’s comprehensive visibility, contextual assessment, and simplified compliance features empower organizations to enhance their security posture across diverse environments. This section explores practical use cases, illustrating how Prisma Cloud improves security in various deployment models, from cloud-native applications to complex hybrid infrastructures. Real-world scenarios demonstrate the tangible benefits of these features.
Cloud-Native Application Security
Prisma Cloud excels in securing cloud-native applications by providing continuous monitoring and threat detection within the development lifecycle. It integrates seamlessly with popular platforms like Kubernetes, enabling proactive security checks and automated responses to vulnerabilities. For instance, Prisma Cloud can automatically scan container images for known vulnerabilities, preventing compromised deployments from entering production. Early detection and remediation of vulnerabilities translate to a significant reduction in risk, and minimize the potential for costly breaches.
Hybrid Environment Security
Hybrid environments, with their combination of on-premises and cloud resources, present unique security challenges. Prisma Cloud offers a unified security platform for hybrid environments, bridging the gap between disparate systems. It provides centralized visibility into the entire infrastructure, regardless of location, and helps organizations maintain a consistent security posture across their entire attack surface. This unified view enables faster incident response and facilitates effective compliance management across the diverse environments.
Real-World Security Posture Improvement
Prisma Cloud’s impact on security posture improvement can be seen in numerous real-world scenarios. One example involves a large financial institution that used Prisma Cloud to enhance its visibility into its hybrid infrastructure. By integrating Prisma Cloud’s security analysis tools, the institution significantly reduced vulnerabilities in its cloud-native application deployments, enabling faster detection and mitigation of potential threats.
This ultimately resulted in a demonstrably stronger security posture and a more secure operational environment.
Table of Use Cases
| Environment Type | Use Case | Achieved Outcomes |
|---|---|---|
| Cloud-Native Applications (Kubernetes) | Automated scanning of container images for vulnerabilities; continuous monitoring of deployments for suspicious activity; proactive identification of misconfigurations. | Reduced vulnerability exposure, faster detection and response to threats, improved compliance with security standards. |
| Hybrid Environments (On-premises and Cloud) | Centralized visibility into the entire infrastructure (cloud and on-premises); streamlined compliance reporting across different environments; automated security policies enforcement across the entire attack surface. | Improved incident response time, enhanced compliance posture, reduction in security incidents, and enhanced visibility across the organization’s entire infrastructure. |
Future Trends and Implications
Prisma Cloud’s current capabilities in visibility, assessment, and compliance are strong, but the future of cybersecurity demands even more sophisticated solutions. The evolving threat landscape, coupled with the increasing complexity of cloud environments, necessitates continuous innovation in security tools. This section explores potential future developments and their impact on the security landscape.
Potential Developments in Visibility
The future of visibility in cloud security will likely involve more proactive and predictive capabilities. Expect advancements in real-time threat detection and response, leveraging machine learning and AI to identify anomalies and potential vulnerabilities before they are exploited. This proactive approach will shift the focus from reactive security measures to a more preventative posture. For instance, advanced threat intelligence feeds integrated into Prisma Cloud could predict potential attacks based on observed patterns and known attack vectors.
Potential Developments in Assessment
Contextual assessment is crucial for effective security. Future iterations of Prisma Cloud will likely incorporate more sophisticated contextual analysis, considering not only technical aspects but also business context and user behavior. This enhanced contextual awareness will allow for more nuanced risk assessments, enabling organizations to prioritize vulnerabilities based on their real-world impact. This will move beyond simple vulnerability scans to a more holistic risk profile for applications and infrastructure.
Potential Developments in Compliance
Compliance is a dynamic field, and Prisma Cloud needs to adapt to evolving regulatory landscapes. Future developments should focus on automating compliance reporting and verification, streamlining the process for organizations operating across multiple clouds and jurisdictions. This will include more sophisticated integrations with various compliance frameworks and the ability to generate automated reports tailored to specific regulatory requirements.
Furthermore, continuous compliance monitoring, facilitated by AI and machine learning, will ensure ongoing adherence to standards.
Potential Future Integrations and Enhancements, With prisma cloud uts gains comprehensive visibility contextual assessment and simplifies compliance
Continued innovation in cloud security demands adaptability and seamless integration. Here are potential enhancements to Prisma Cloud:
- Integration with Kubernetes orchestration tools: This will allow Prisma Cloud to provide comprehensive visibility into containerized applications, enabling better security posture management within Kubernetes environments. This integration would improve the detection of container-related vulnerabilities and threats.
- Enhanced API integrations: Improved API integrations with existing cloud platforms and security tools will allow for streamlined data flow and automated workflows, reducing manual processes and improving overall efficiency. This will further strengthen security operations through automated responses and proactive measures.
- AI-powered threat hunting: Implementing advanced AI algorithms to analyze massive datasets in real-time will help identify suspicious patterns and potential threats that may be missed by traditional security tools. This will enhance threat hunting and accelerate incident response.
- Automated vulnerability remediation: Prisma Cloud could offer automated remediation capabilities, suggesting fixes and implementing patches for identified vulnerabilities, further reducing the attack surface and improving security posture. This is a critical component of proactive security.
- Zero Trust implementation: Integration with zero trust principles will enable granular access control and continuous verification of identities, reducing the risk of unauthorized access and enhancing the overall security posture.
Closing Summary
In conclusion, Prisma Cloud’s comprehensive visibility, contextual assessment, and simplified compliance features offer a powerful solution for enhancing security posture in today’s complex environments. By understanding the interconnectedness of these elements, organizations can gain a more robust security framework, proactively identifying vulnerabilities, and efficiently adhering to compliance requirements. The future of security operations is looking brighter thanks to these advancements.