Kuwait news agency twitter hack iran – The Kuwait News Agency (KUNA) Twitter hack, potentially linked to Iran, has ignited a firestorm of discussion. This incident raises crucial questions about the security of vital news sources and the role of social media in international relations. Understanding the KUNA Twitter hack, Iran’s potential involvement, and the resulting impact is crucial for assessing the overall situation.
KUNA, a cornerstone of Kuwaiti media, plays a vital role in disseminating news globally. Its presence on Twitter is critical for reaching a wide audience. This hack underscores the vulnerability of even established news organizations to sophisticated cyberattacks, demanding greater attention to cybersecurity protocols in the digital age.
Background of the Kuwait News Agency (KUNA)
The Kuwait News Agency (KUNA) stands as a cornerstone of Kuwait’s media landscape, playing a vital role in disseminating news and information both domestically and internationally. Established in 1972, KUNA’s history is intrinsically linked to Kuwait’s own development and its commitment to transparency and communication. Its significance stems from its early adoption of modern technology and its commitment to impartiality, ensuring a global audience has access to accurate and timely news from Kuwait.KUNA’s mission extends beyond simply reporting events; it actively shapes the narrative surrounding Kuwait in the global arena.
It provides a platform for Kuwaiti perspectives and voices, while also serving as a vital source of information for international audiences seeking insight into the region.
History and Significance
KUNA was founded in 1972, aiming to provide comprehensive news coverage for the nation and the international community. Its establishment marked a crucial step in Kuwait’s efforts to foster transparency and maintain a positive image in the global community. This was a time of significant growth and development in the region, and KUNA’s emergence reflected the nation’s commitment to its role as a vital player in regional affairs.
KUNA quickly became a trusted source for news from the Middle East, building a reputation for accuracy and impartiality.
Services and Functions
KUNA offers a wide array of services, encompassing news gathering, translation, and dissemination. It provides news in multiple languages, catering to a global audience. KUNA’s functions include producing news reports, features, and analyses. Its services also include wire services for news distribution to various media outlets. In essence, KUNA acts as a central hub for information originating from Kuwait.
Importance of KUNA’s Presence on Twitter
KUNA’s presence on Twitter is a crucial component of its strategy for reaching a broader audience. It leverages this platform to deliver timely updates, engage in conversations, and provide insights into current events impacting Kuwait and the wider region. By interacting with users on Twitter, KUNA can foster a sense of engagement and transparency, making its news and information more accessible.
KUNA’s Twitter presence also enables the agency to quickly address potential misinformation and maintain its credibility.
Organizational Structure and Reporting Protocols
KUNA’s organizational structure is designed to ensure efficiency and accuracy in its news dissemination. The agency employs a hierarchical structure, with various departments responsible for specific tasks, from news gathering to editing and translation. Its reporting protocols are stringent, emphasizing impartiality and adherence to journalistic ethics. These protocols are critical in maintaining KUNA’s reputation for reliability and accuracy.
The agency follows a rigorous fact-checking process before publishing any news report, ensuring that information is both factual and impartial.
Role in Disseminating News to a Global Audience
KUNA plays a vital role in disseminating news to a global audience. It provides a platform for Kuwaiti voices and perspectives to be heard on a global scale. This global reach is crucial in countering misinformation and presenting an accurate picture of events in the region. KUNA employs a multi-language strategy to cater to a diverse readership, thereby enhancing its ability to connect with audiences worldwide.
KUNA’s extensive network of correspondents and partnerships ensures that it receives and distributes news from diverse sources.
The Twitter Hack
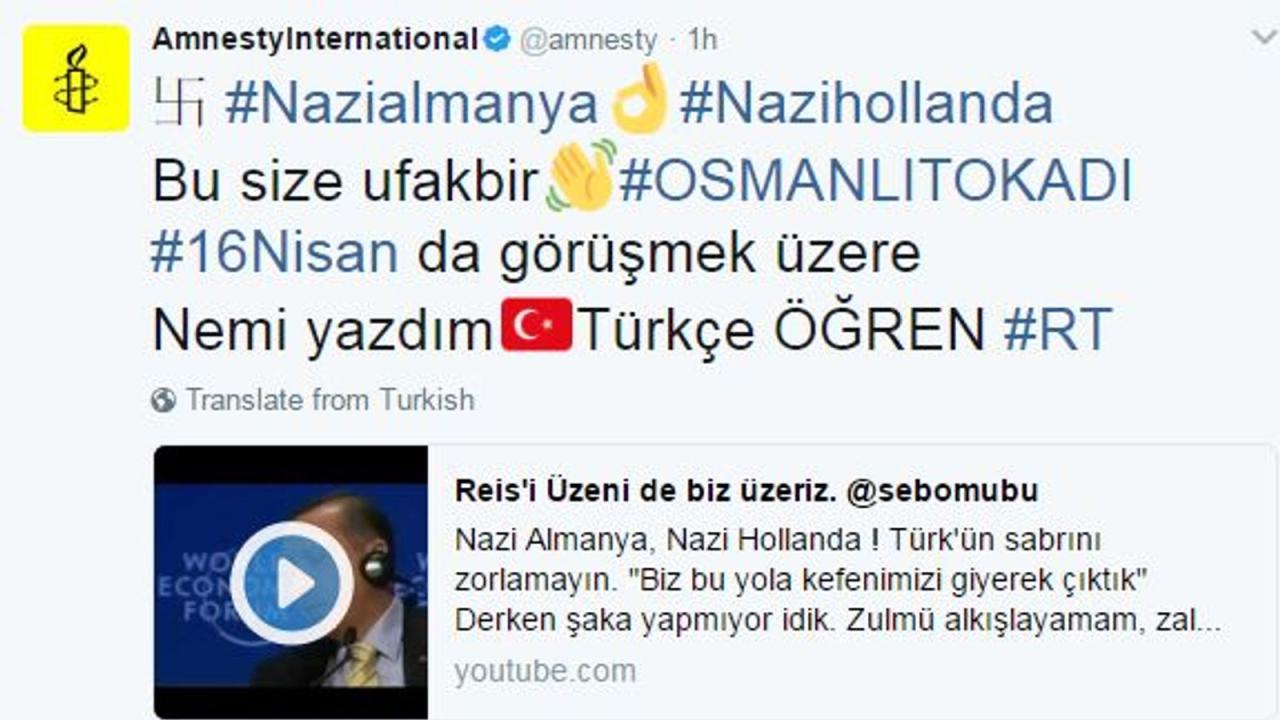
The recent Twitter hack targeting the Kuwait News Agency (KUNA) highlights the vulnerability of even reputable news organizations in the digital age. The attack underscores the importance of robust cybersecurity measures and the need for continuous vigilance against sophisticated online threats. The compromised account, a crucial source of information, was subjected to a barrage of malicious activity, raising concerns about the potential for misinformation and disinformation campaigns.
Methods and Techniques Used
The precise methods employed in the KUNA Twitter hack remain under investigation. However, common techniques used in similar attacks often involve exploiting vulnerabilities in the target’s systems, leveraging social engineering tactics to gain unauthorized access, or employing sophisticated malware. Attackers might also exploit vulnerabilities in third-party applications or services that the target uses. In some cases, credential stuffing—reusing compromised credentials from other platforms—is employed.
This strategy is frequently used in combination with other techniques to increase the likelihood of success.
Impact on KUNA’s Twitter Account
The KUNA Twitter account suffered significant disruption during the hack. The account was used to disseminate false or misleading information, potentially causing confusion and anxiety among followers. This disruption likely negatively impacted KUNA’s credibility and its ability to deliver accurate news to its audience. The potential for reputational damage is substantial.
Compromised Content Examples
The compromised content included the dissemination of false or misleading statements. This could have included fabricated news reports, political endorsements, or personal attacks. The compromised account likely disseminated messages that were inconsistent with KUNA’s usual reporting style, highlighting the disruption caused by the attack.
Potential Motivations Behind the Attack
The motivations behind the attack are still speculative. Such attacks are sometimes driven by malicious intent, including spreading misinformation, disrupting public discourse, or promoting a particular agenda. The attack might have been part of a larger campaign targeting the Kuwaiti government or its institutions. Alternatively, it might have been a test of Twitter’s security protocols or an attempt to demonstrate the vulnerability of news organizations.
The recent hack of the Kuwait News Agency’s Twitter account, supposedly linked to Iran, is definitely a significant development. Meanwhile, it’s exciting to see new tech announcements like the Dell XPS 15 and 17 laptops with Intel and Nvidia components, which you can check out in the full announcement here: dell xps 15 17 laptop intel nvidia launch announcement.
Hopefully, this technological advancement will help us stay ahead of cyber threats like this one in the future. Still, the motivations and implications of the Kuwait News Agency hack remain a crucial area of concern.
Comparison to Similar Incidents
Numerous similar incidents have occurred in the past, demonstrating a growing trend of targeted attacks against news organizations and other high-profile entities. These attacks often share similar characteristics, such as the use of sophisticated techniques and a focus on disrupting information dissemination. Past incidents highlight the urgent need for robust security measures and ongoing vigilance in the digital age.
For instance, the 2020 hack of multiple news organizations demonstrates a pattern of using social engineering and exploiting vulnerabilities to spread misinformation. These prior examples show a pattern of attacks that are not isolated incidents, but rather part of a broader trend.
Iran’s Potential Involvement
The recent hack of the Kuwait News Agency (KUNA) has sparked intense speculation, particularly regarding Iran’s potential role. The timing of the cyberattack, coupled with historical tensions between the two nations, fuels these suspicions. While definitive proof remains elusive, examining the circumstantial evidence and the broader geopolitical context is crucial to understanding the potential ramifications.The cyberattack on KUNA highlights the increasing sophistication and frequency of state-sponsored cyber operations.
These attacks are not simply acts of vandalism; they can have significant geopolitical consequences, influencing public opinion, undermining trust, and potentially escalating tensions between nations.
Potential Links Between Iran and the Hack
The historical relationship between Kuwait and Iran, characterized by periods of both cooperation and conflict, provides a context for examining potential links. Past disagreements over territorial claims, maritime boundaries, and political influence have contributed to an often strained relationship. These historical tensions, coupled with Iran’s documented history of cyber activity, raise questions about potential motives for a cyberattack on KUNA.
Public Statements and Accusations Regarding Iran’s Role
Various public statements have been made concerning Iran’s possible involvement. While some countries and analysts have explicitly accused Iran of being behind the attack, others have refrained from making such definitive pronouncements, citing the lack of conclusive evidence. The absence of irrefutable proof complicates the situation, leaving the possibility of other actors remaining open.
Evidence Presented or Alleged in Connection to Iran
The evidence presented in connection to Iran’s involvement, while circumstantial, includes specific patterns of cyber activity attributed to Iranian actors. These patterns may include the use of particular hacking tools, the style of attack, and the nature of the information compromised. However, it is crucial to recognize that such patterns can be mimicked or employed by other actors, making attribution difficult.
History of Relations Between Kuwait and Iran
The history of relations between Kuwait and Iran has been complex and at times fraught with tension. This includes disputes over maritime boundaries, oil resources, and political influence in the region. These historical tensions contribute to the sensitivity of the situation and the potential for the cyberattack to exacerbate existing geopolitical concerns.
Potential Geopolitical Implications of the Hack
The cyberattack on KUNA has potential geopolitical implications that extend beyond the immediate impact on Kuwait. It could escalate regional tensions, potentially leading to further instability and conflict. The attack serves as a reminder of the increasing importance of cybersecurity in international relations and the potential for cyberattacks to be used as tools of geopolitical coercion. This underscores the importance of robust international cooperation in addressing and preventing such attacks.
Impact and Aftermath
The recent hack of the Kuwait News Agency (KUNA) Twitter account, suspected to have Iranian origins, has rippled through the information landscape, raising concerns about the credibility of news sources and the potential for state-sponsored cyberattacks. The incident exposed vulnerabilities in news dissemination and highlighted the growing threat of misinformation in the digital age. The long-term consequences extend beyond the immediate fallout, impacting trust and potentially shaping future media strategies.The hack’s impact transcended the mere act of altering tweets; it struck at the very heart of public trust in the media.
KUNA, a respected news agency, found itself embroiled in a crisis of credibility, as the authenticity of its news feed was challenged. This, in turn, casts a shadow on the broader media landscape, as public trust in news sources in general can be easily eroded by such incidents.
Immediate Consequences of the Hack
The immediate consequences of the hack were multifaceted. KUNA’s Twitter account was compromised, leading to the dissemination of false or misleading information. This compromised information created confusion and uncertainty among the public, especially given the sensitivity of the geopolitical situation surrounding the incident. The rapid spread of misinformation via social media amplified the impact, potentially affecting diplomatic relations and public perception of the event.
The rapid response of KUNA to the situation was essential in mitigating the negative effects, though the damage had already been done.
Impact on Public Trust
The hack undoubtedly eroded public trust in KUNA and, by extension, the media in general. The incident exposed a vulnerability that many people had not considered, demonstrating how easily information can be manipulated in the digital sphere. This can lead to a diminished belief in the accuracy and impartiality of news sources. News organizations must strive to strengthen security measures and transparency to rebuild trust with the public.
Previous incidents of similar scale, such as the Cambridge Analytica scandal, highlight the profound effect such events can have on public perception of information sources.
KUNA’s Response and Measures
KUNA, in response to the hack, took swift action to restore its account and assure the public of its commitment to accurate reporting. This included publicly acknowledging the incident and outlining steps to strengthen its security protocols. The agency likely implemented additional measures to protect its systems from future attacks, potentially including enhanced authentication, firewalls, and intrusion detection systems.
Their response, while crucial, demonstrated the need for proactive measures to prevent similar events in the future.
Public Reactions and Responses
Public reactions to the incident were varied, ranging from skepticism to outrage. Some expressed concerns about the credibility of news sources, while others questioned the potential motivations behind the attack. Social media discussions surrounding the incident likely included accusations and speculation, highlighting the importance of responsible online engagement and the need for critical evaluation of information. The ensuing public discourse, while sometimes unproductive, underscores the need for a more informed and engaged public in the digital age.
Governmental and Legal Responses
The incident prompted governmental investigations to determine the extent of the cyberattack and potential implications for national security. The Kuwait government likely took measures to analyze the attack, identify vulnerabilities, and assess the potential for future attacks. This could involve the establishment of task forces, or increased collaboration with international partners to share information and strategies to prevent such attacks.
The legal ramifications of the hack, including potential legal action against the perpetrators, are yet to be determined. The incident highlighted the need for robust legal frameworks to address cybercrimes, particularly those targeting news organizations.
The recent hack of the Kuwait News Agency’s Twitter account, supposedly linked to Iran, is definitely a big story. It’s fascinating how these digital attacks can ripple out, impacting news dissemination and trust. Speaking of digital ripples, the latest version of The Sims Mobile, a popular gaming experience from Maxis on Android and iOS platforms, the Sims mobile focused version gaming maxis android ios , is really engaging players with new features.
It makes you wonder if the same level of innovative strategy and security measures are in place for news outlets, considering the potential for misinformation and disruption.
Media Response and Analysis
The KUNA Twitter hack, and the potential involvement of Iran, sparked a flurry of media coverage worldwide. International news outlets responded with varying degrees of scrutiny and analysis, reflecting diverse perspectives on the incident and its implications. Different regions and news organizations presented the story with distinct tones and focuses, highlighting the complexities of interpreting such a politically sensitive event.This analysis delves into the international media’s response, exploring the diverse perspectives presented and the potential motives behind the cyberattack.
It examines the varying approaches of different news organizations, providing a comparative overview of their coverage.
International Media Coverage
The incident garnered significant attention across international news outlets. Major global news agencies, including Associated Press, Reuters, and BBC News, extensively covered the story, providing updates and analysis. Regional news outlets also contributed to the narrative, often emphasizing the geopolitical context and potential implications for regional stability. Social media platforms played a vital role in disseminating information and fostering discussions, though the veracity of some claims needed careful evaluation.
Media Analysis of the Situation
Media analysis of the KUNA hack focused on several key aspects. Discussions explored the technical details of the attack, examining the methods employed by the perpetrators and the vulnerabilities exploited. Furthermore, the political implications of the incident were extensively analyzed, with many outlets exploring the potential motives and actors behind the cyberattack. Many analyses also highlighted the importance of cyber security for news organizations in the digital age, underscoring the need for robust security measures to protect vital information.
Differing Perspectives on the Incident
The incident sparked diverse perspectives on the potential motives behind the cyberattack. Some outlets focused on the geopolitical tensions between Kuwait and Iran, suggesting that the hack could be a manifestation of those tensions. Other analyses highlighted the potential for the hack to be a diversionary tactic, masking other agendas or objectives. Differing opinions emerged regarding the extent of Iran’s involvement, with some outlets presenting it as a plausible suspect while others expressed skepticism or sought alternative explanations.
Comparative Analysis of News Coverage
News coverage from different regions exhibited distinct approaches. For example, Middle Eastern news outlets often emphasized the regional context, focusing on the potential implications for regional stability and the dynamics of the broader geopolitical landscape. In contrast, Western news outlets often presented a more global perspective, examining the attack within the context of broader cyber security concerns.
Comparative Table of News Organization Approaches
| News Organization | Tone | Focus | Angle | Source |
|---|---|---|---|---|
| Associated Press | Neutral | Technical aspects of the attack, political implications | Focus on the event itself and its possible implications | AP News Archives |
| Reuters | Analytical | Geopolitical context, international relations | Emphasis on the regional context and its impact on stability | Reuters News Archives |
| Al Jazeera | Critical | Regional tensions, Iran’s role | Focus on the political implications of the event, particularly regarding the relations between Kuwait and Iran. | Al Jazeera News Archives |
Cybersecurity Measures
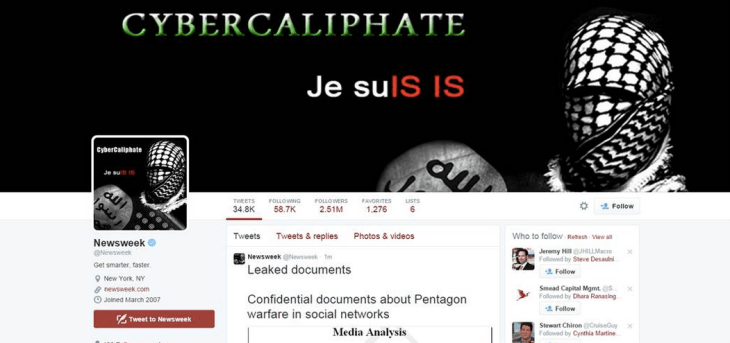
The recent cyberattack on the Kuwait News Agency (KUNA) highlights the critical need for robust cybersecurity measures in the digital age. News agencies, like KUNA, are prime targets for malicious actors seeking to disseminate misinformation or disrupt vital information flows. Protecting their systems and maintaining the integrity of their reporting is paramount. This necessitates a proactive approach to cybersecurity, encompassing both preventative measures and incident response strategies.The attack underscores the vulnerability of even well-established organizations to sophisticated cyberattacks.
This necessitates a thorough review of current protocols and a commitment to continuous improvement in cybersecurity infrastructure. This includes not only technical measures but also a strong cultural emphasis on security awareness among staff.
Current Cybersecurity Practices of News Agencies
News agencies, including KUNA, likely employ a multi-layered approach to cybersecurity. This typically involves firewalls, intrusion detection systems, and antivirus software to prevent unauthorized access and malicious code. Regular security audits and vulnerability assessments are also crucial. Employee training on phishing scams and secure password practices is essential. Data encryption and backup procedures are also critical to mitigate the impact of a successful breach.
Potential Improvements in Cybersecurity Protocols
A proactive approach to cybersecurity requires a constant evaluation and adaptation to evolving threats. The following table Artikels potential improvements to KUNA’s and similar news agencies’ cybersecurity protocols.
The Kuwait News Agency Twitter hack, reportedly linked to Iran, is a serious issue. Meanwhile, it’s worth noting that many people are experiencing streaming issues with Spotify right now. This is likely causing a lot of frustration for music lovers, similar to the disruption caused by the Kuwaiti hack. It’s a shame that these kinds of incidents can affect both the news and our music, making us wonder about the safety of online platforms.
spotify experiencing streaming issues are certainly a distraction from the bigger story. Hopefully, the Kuwait News Agency issue will be resolved soon.
| Aspect | Current Situation | Recommended Improvements |
|---|---|---|
| Firewall Configuration | Likely configured but potentially outdated or lacking sufficient rules. | Implement next-generation firewalls with advanced threat intelligence integration and real-time threat mitigation capabilities. Regularly update firewall rules to block known malicious IPs and domains. |
| Intrusion Detection/Prevention Systems (IDS/IPS) | Possibly in place but may not be actively monitored or updated regularly. | Implement advanced IDS/IPS solutions that detect and respond to zero-day exploits and advanced persistent threats (APTs). Establish a dedicated team to monitor and analyze alerts. |
| Security Information and Event Management (SIEM) | Possibly utilized but may lack comprehensive analysis and correlation capabilities. | Implement a robust SIEM solution to centralize security logs and correlate events. Use threat intelligence feeds to improve detection accuracy. Implement automated response mechanisms to critical alerts. |
| Vulnerability Management | Likely conducted periodically, but may not be continuous. | Implement a continuous vulnerability management program. Automate vulnerability scanning and patching processes. Prioritize vulnerabilities based on risk level and exploit potential. |
| Employee Training | Training may be provided, but may not be frequent or comprehensive. | Implement regular and targeted security awareness training programs, including simulations of phishing attacks. Update training materials based on emerging threats. |
Importance of Proactive Cybersecurity Measures, Kuwait news agency twitter hack iran
Proactive cybersecurity measures are crucial in the digital age. The cost of a data breach can be substantial, ranging from reputational damage to financial losses. Proactive measures can significantly reduce the risk of such incidents.
Security Vulnerabilities in KUNA’s Systems
Potential vulnerabilities in KUNA’s systems could include outdated software, weak passwords, inadequate access controls, or insufficient monitoring of network traffic. Lack of a comprehensive security awareness program could also expose the organization to phishing attacks.
Preventative Measures to Reduce Risk of Future Attacks
Implementing a layered approach to security is vital. This involves using strong authentication methods, regularly updating software, and conducting thorough security audits. Staff training on recognizing and reporting suspicious activity is also crucial. A robust incident response plan is essential to minimize the impact of a breach if one occurs. The adoption of zero-trust architecture, which assumes no implicit trust, is a key component of modern cybersecurity strategies.
International Relations Implications
The recent Twitter hack of the Kuwait News Agency (KUNA) has significant implications for international relations, particularly within the Middle East. The incident, with its potential link to Iran, underscores existing geopolitical tensions and raises concerns about the weaponization of social media platforms. This incident is more than just a cyberattack; it’s a demonstration of the evolving nature of conflict and its impact on diplomatic discourse.The hack’s repercussions extend beyond the immediate damage to KUNA’s reputation and Kuwait’s standing.
It has the potential to further strain already complex relationships, potentially exacerbating existing conflicts and creating new obstacles to cooperation. The perception of who is responsible and the subsequent responses will heavily influence future interactions between nations.
Potential Impact on Diplomatic Relations
The incident’s impact on diplomatic relations will be multifaceted. Attribution of the attack will heavily influence how countries react. If Iran is definitively linked, it could lead to a significant escalation of tensions, potentially impacting broader regional security. Conversely, if the attack is attributed to another actor, the consequences will likely be less severe, but still create an atmosphere of distrust.
Regardless of attribution, the incident will likely lead to increased security measures and greater scrutiny of social media platforms’ role in international affairs.
Effects on the Broader Middle Eastern Geopolitical Landscape
The hack highlights the vulnerability of vital information sources in the Middle East. It potentially alters the perception of trust and reliability in news dissemination in the region. This could further destabilize the existing geopolitical landscape, already marked by complex alliances and rivalries. The incident could influence the trajectory of regional cooperation efforts and potentially hinder future diplomatic initiatives.
The region’s already complex political dynamics will be further tested and may lead to a period of increased suspicion and reduced cooperation.
Comparison to Past Diplomatic Tensions
The KUNA hack bears resemblance to past instances of cyber warfare and disinformation campaigns. For example, the Stuxnet virus, which targeted Iranian nuclear facilities, exemplifies the use of technology as a tool of geopolitical pressure. Similarly, the spread of misinformation through social media has been a factor in escalating conflicts in various parts of the world. However, the specific context of the KUNA hack and the potential involvement of Iran will add a unique layer to the geopolitical calculus.
Role of Social Media in International Relations
Social media platforms have become increasingly significant actors in international relations. They can be utilized for disseminating information, fostering public opinion, and influencing policy decisions. However, they are also susceptible to misuse and manipulation. The KUNA hack demonstrates the potential for social media to be weaponized, undermining trust and potentially escalating tensions. This incident raises the need for greater awareness of the role of social media in international relations and the importance of robust cybersecurity measures.
Summary of Overall Geopolitical Implications
The KUNA hack, with its potential link to Iran, carries significant geopolitical implications. It underscores the escalating use of cyber warfare and information operations as tools in international conflicts. This incident will likely lead to increased scrutiny of social media platforms and greater emphasis on cybersecurity measures in the region. Furthermore, the hack may impact future diplomatic efforts and regional cooperation, exacerbating existing tensions and creating new challenges for international relations.
Concluding Remarks: Kuwait News Agency Twitter Hack Iran
The KUNA Twitter hack, potentially connected to Iran, has exposed critical vulnerabilities in online news dissemination. The incident’s geopolitical implications are significant, potentially straining diplomatic relations and highlighting the role of social media in modern international conflicts. Understanding the details, motivations, and long-term consequences of this hack is vital for future preventative measures and maintaining trust in news sources.





